Getting a User’s Group Membership
Administrators often need to find out which Active Directory groups a certain user (or machine, group, or service account) is a member of. They have several options for discovering this information, including:
- Active Directory Users and Computers (ADUC)
- GPResult cmdlet
- Whoami cmdlet
Using the ADUC Console
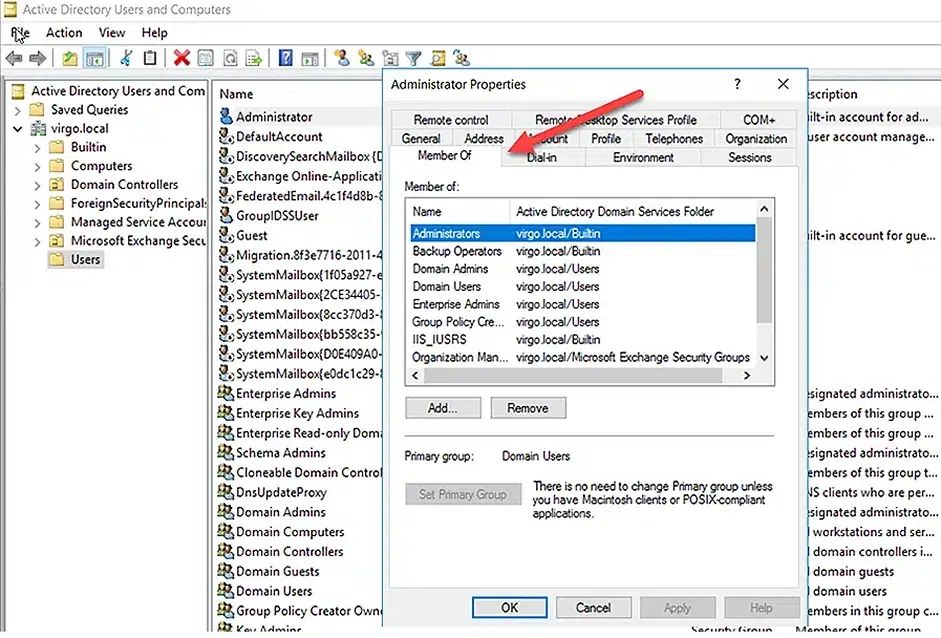
ADUC remains the most common way to investigate a user’s group memberships. Simply launch the console, open the user’s properties, and go to the MemberOf tab, as shown below:
Using the GPResult Cmdlet
GPResult is used primarily to check Group Policy settings on a client or workstation, but it also provides information about the group memberships of the user who runs it. Simply open an elevated PowerShell command line, log in as the user you want to check and issue the following command:
gpresult /R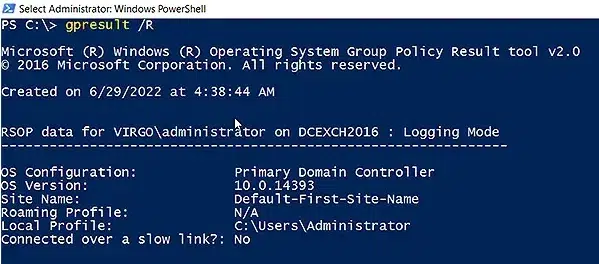
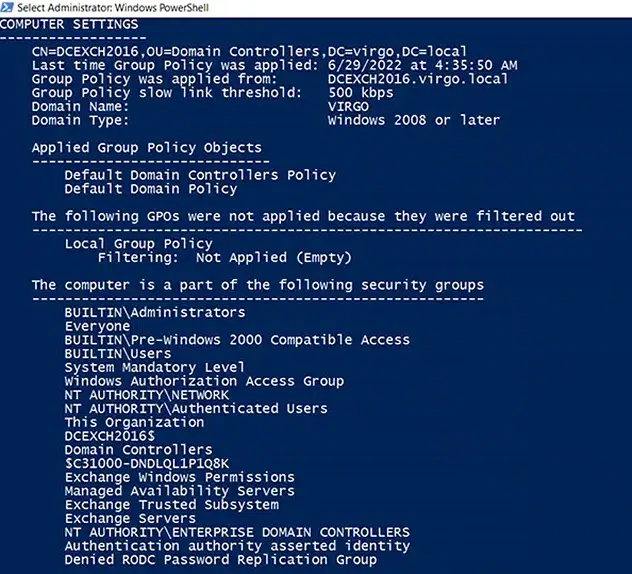
The Computer Settings section shows the group memberships of the computer object.
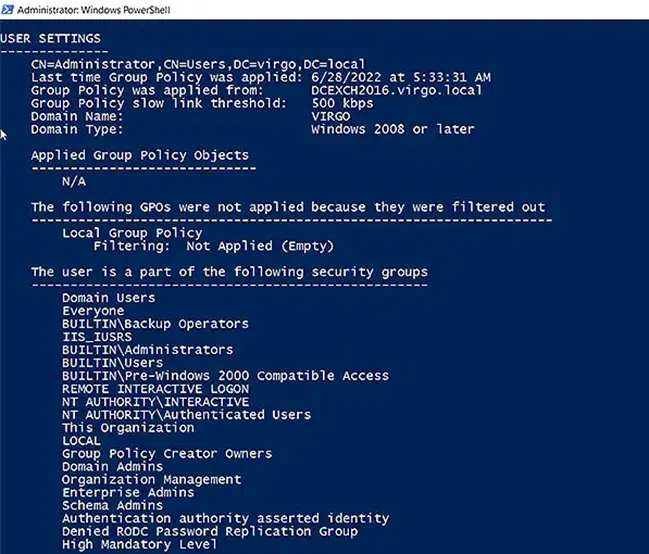
Under User Settings, you can see the group memberships of the logged-on user:
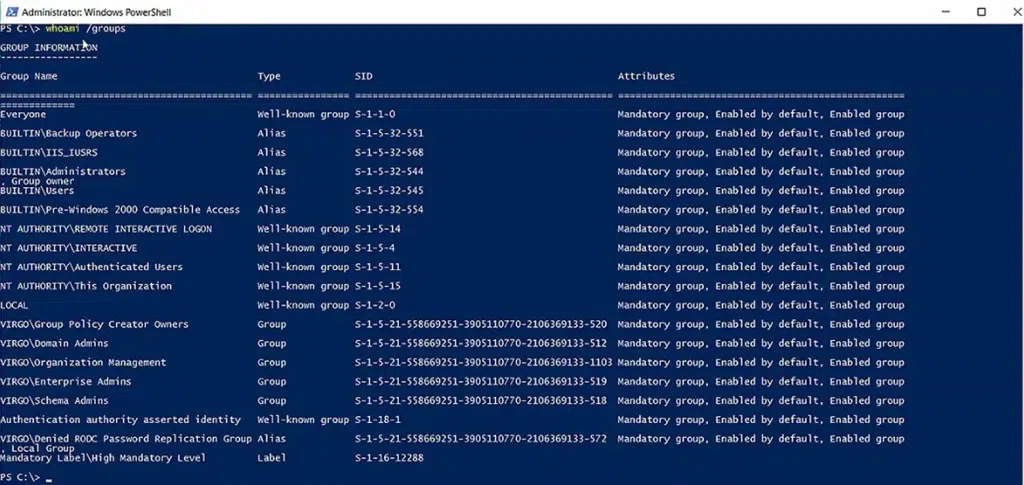
Using the Whoami Cmdlet
Alternatively, a logged-on user can see their group memberships by using this command:
Whoami /groupsThe output is shown below:
Get-ADPrincipalGroupMembership Cmdlet
While these methods are sufficient if you need to check the membership of just one or two users, or only your own group membership, they do not scale for the needs of many administrators.
Enter the PowerShell cmdlet Get-ADPrincipalGroupMembership. This cmdlet shows the AD groups that a specified user, computer, group, or service account is a member. A global catalog is necessary for this command to perform a group search. If the forest that contains the user, computer, or group doesn’t have a global catalog server, the cmdlet gives an error.
Get-ADPrincipalGroupMembership: Parameters
The following parameters are most commonly used with the Get-ADPrincipalGroupMembership cmdlet:
- AuthType
- Credential
- Identity
- Partition
- ResourceContextPartition
- ResourceContextServer
- Server
AuthType
Use this parameter to specify the authentication method to be used. Valid values are:
- Negotiate or 0 — This is the default authentication mechanism.
- Basic or 1 — This option requires an SSL (Secure Sockets Layer) connection.
Credential
If you want to run a PowerShell cmdlet or script and the logged-on user does not have enough rights, use this parameter to specify alternate credentials.
Specify the username in the format AbbeyCrawford or domain\AbbeyCrawford. Alternatively, you can create a PSCredential object by using the Get-Credential cmdlet.
Identity
Use the Identity parameter to specify the AD object whose group memberships you want to see. You can specify the object by its distinguished name (DN), GUID, security identifier (SID) or SAM account name. Alternatively, you can build a variable or provide an object via the pipeline to the Identity parameter. For example, you could retrieve a user object using the Get-ADUser cmdlet and send it through the pipeline to the Get-ADPrincipalGroupMembership cmdlet.
Partition
Use this parameter to specify the distinguished name of an Active Directory partition to search for groups that an object is a member of.
ResourceContextPartition
Use this parameter to specify the distinguished name of a partition of an AD or AD LDS instance to search for groups that an object is a member of.
To indicate a partition hosted by the provided server, combine this option with the ResourceContextServer parameter. If the ResourceContextPartition option is not provided, the ResourceContextServer’s default partition is searched.
ResourceContextServer
Use this parameter to identify group memberships in a domain other than the one where the user’s account is located (i.e., the user or object whose memberships you want to fetch). Include the ResourceContextPartition parameter as well if you want to search in a partition other than the domain’s default partition.
Server
Use this parameter to provide the fully qualified domain name, NetBIOS name or fully qualified directory server name of the AD Domain Services instance that you want to connect to (with or without port number).
Get-ADPrincipalGroupMembership: Examples
The following examples showcase the use of the Get-ADPrincipalGroupMembership cmdlet:
- Get Group Memberships for a User in a Particular AD LDS Instance
- Get the Group Memberships for the Domain Administrator
- View Group Membership Information in Tabular Form
- Get the Group Memberships for an Account in a Resource Domain
- Filter Groups using Get-ADPrincipalGroupMembership
- Get a Computer’s Memberships
Get Group Memberships for a User in a Particular AD LDS Instance
To retrieve a user’s group membership information from a specific server and partition, use the following cmdlet. The -Identity parameter is used with the distinguished name of the user whose membership you want to see.
Get-ADPrincipalGroupMembership -Server localhost -Identity " CN=AbbeyCrawford,OU=Versacorp,DC=virgo,DC=local" -Partition "DC=Virgo,DC=local"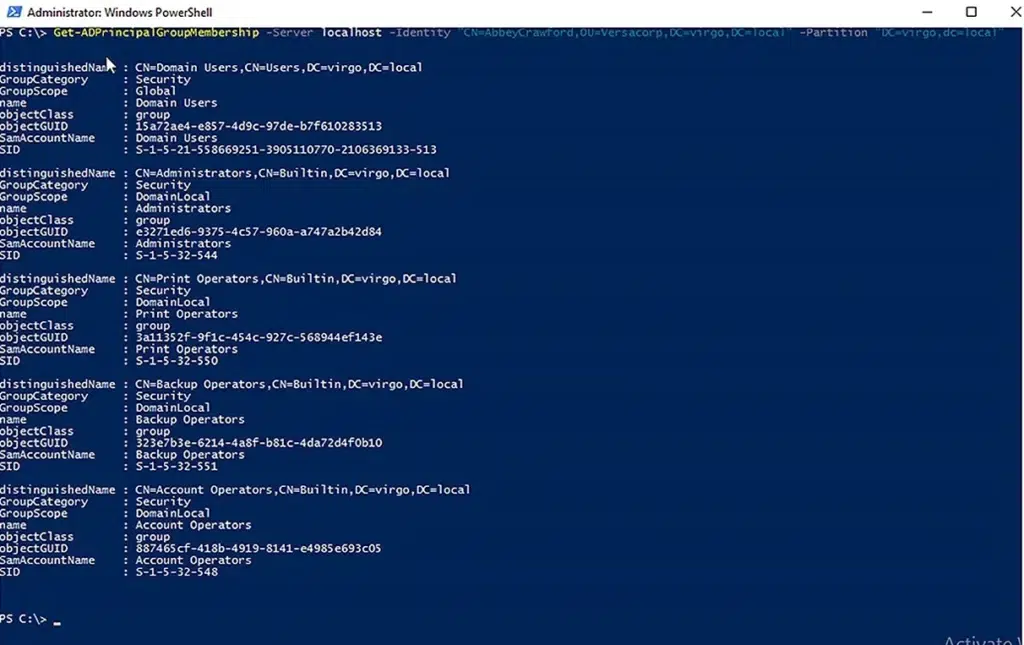
Get the Group Memberships for the Domain Administrator
To view the group membership of the built-in administrator of a domain, use the following cmdlet:
Get-ADPrincipalGroupMembership administrator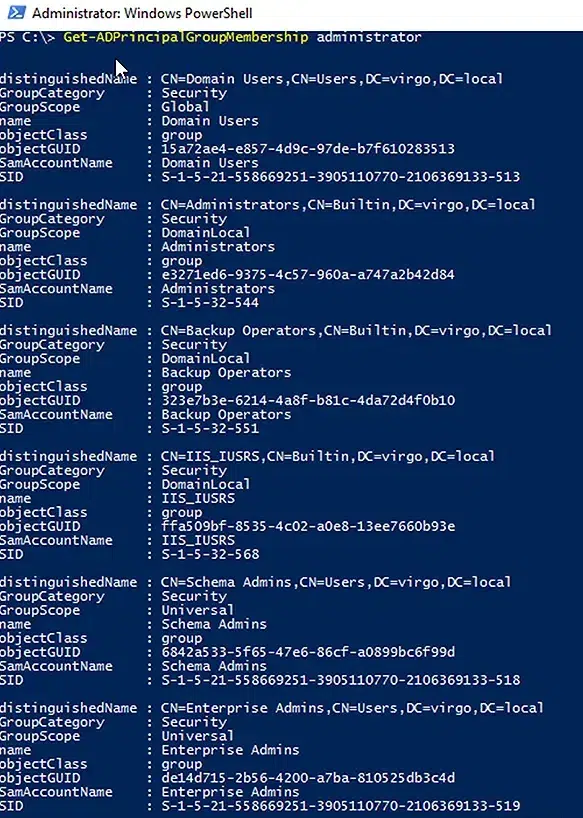
Note that by default, the built-in administrator is a member of commonly known security groups such as Administrators, Backup Operators, Schema Admins, Enterprise Admins and Domain Admins.
View Group Membership Information in Tabular Form
If this information is too raw and you prefer to view it in a tabular form, use the command below. First, Get-ADPrincipalGroupMembership gets the group memberships of the user specified in the Identity parameter. That result is passed to Get-ADGroup, which gets the details about the groups. That information is passed to the third cmdlet, Select, which prints the name and description of each group that the user is a member of.
Get-ADPrincipalGroupMembership -Identity administrator | Get-ADGroup -Properties Description | Select Name, Description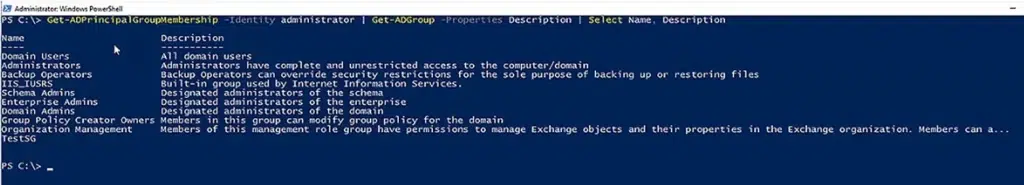
Get the Group Memberships for an Account in a Resource Domain
To search a particular resource domain for the group memberships of an AD user account, run the following command:
Get-ADPrincipalGroupMembership -Identity AbbeyCrawford -ResourceContextServer virgo.local -ResourceContextPartition “DC-virgo,DC=local”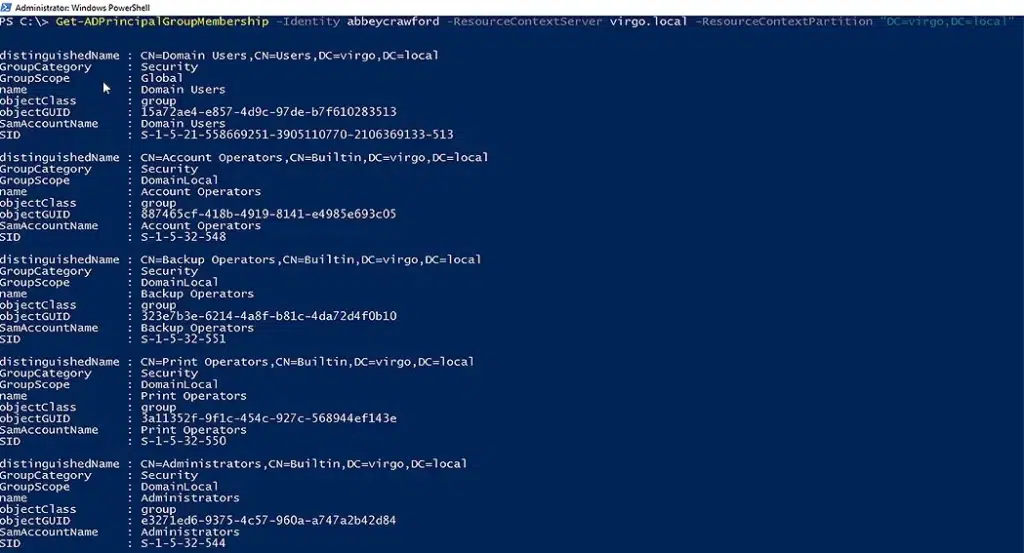
Filter Groups using Get-ADPrincipalGroupMembership
If you want to filter the groups that the user is a member of, run the following command:
Get-ADPrincipalGroupMembership -Identity AbbeyCrawford | Select Name | Where-Object {$_.Name -like 'S*'} | Sort Name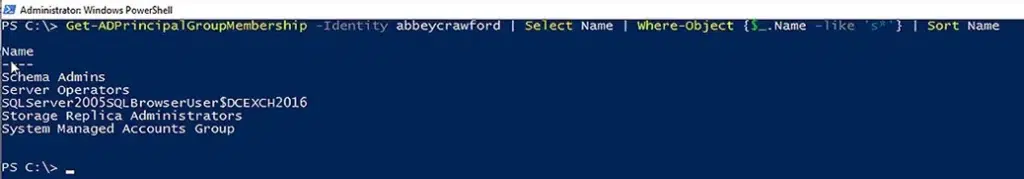
In this cmdlet:
- Get-ADPrincipalGroupMembership gets the group memberships of the specified user and passes that output to the Select command.
- The Select command limits the results to just the names of the groups.
- The where-object argument filters the groups according to the condition specified.
- The last command sorts the filtered list and displays the results in the PowerShell console.
Get a Computer’s Memberships
To get the groups that a computer object is a member of, run the following cmdlet:
Get-ADPrincipalGroupMembership -Identity 'CN=DCEXCH2016,OU=Domain Controllers,DC=virgo,DC=local' | Select-Object Name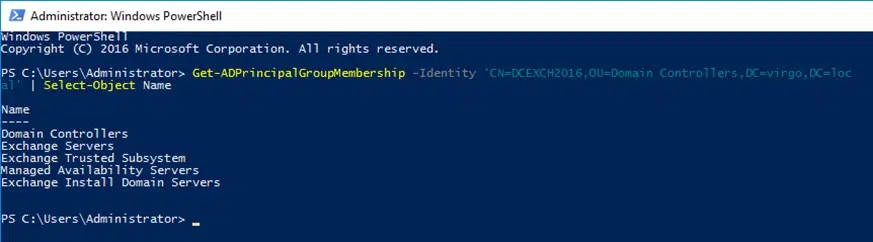
Here, the Get-ADPrincipalGroupMembership cmdlet gets the membership of the computer object specified in the Identity parameter as a distinguished name. It passes the output to the second cmdlet, which displayed the group names in the PowerShell console.
Viewing Memberships using the Netwrix Directory Manager Report Module
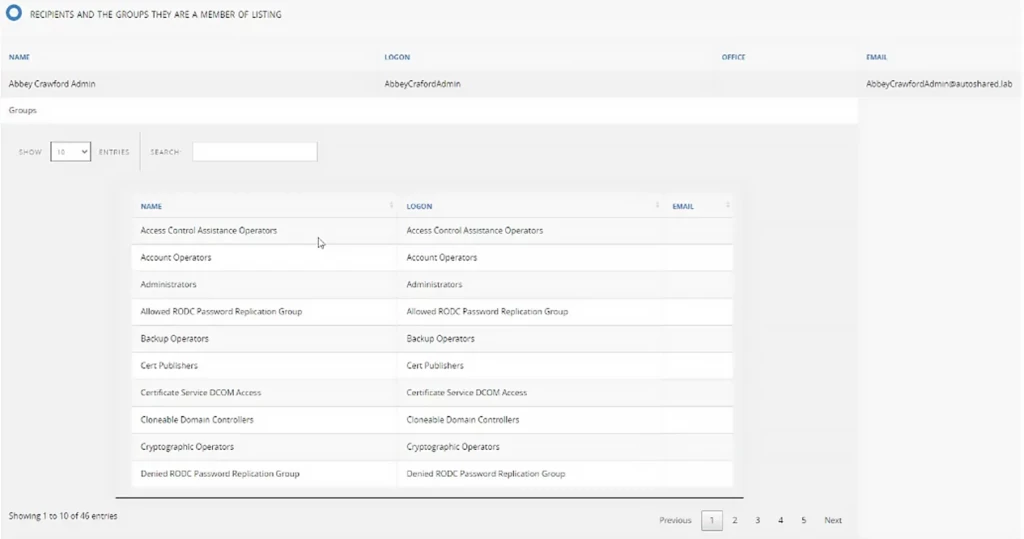
A solid alternative to PowerShell and other Microsoft methods for viewing group members is the Netwrix Directory Manager Reports module. This free reporting tool is designed to run reports on Active Directory, Microsoft Exchange, and Office 365. Here is the report you can quickly create to view users and their group memberships:
You can create a report and schedule it to run as required. The report uses the following LDAP query to fetch users and their group memberships from Active Directory:
(&(objectCategory=Person)(objectless=User))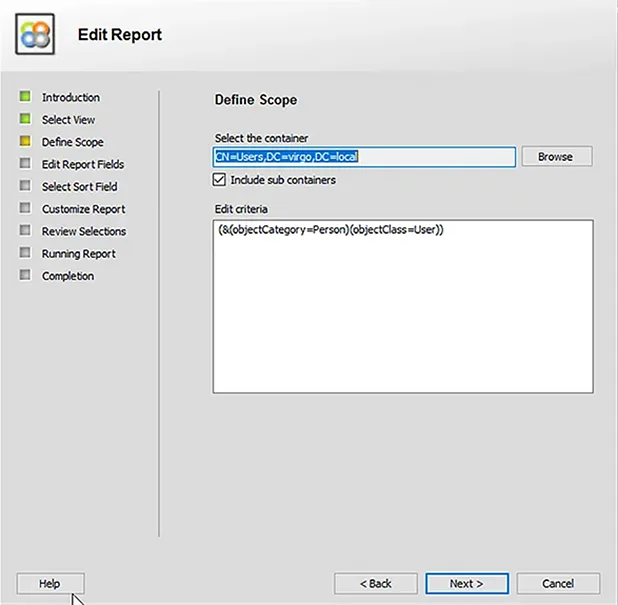
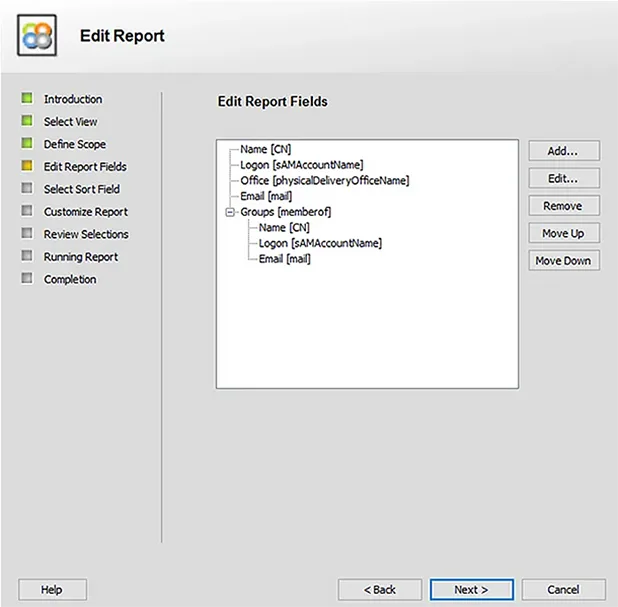
The following screenshot shows some of the columns in the report. You can add more columns or remove the default ones as needed.
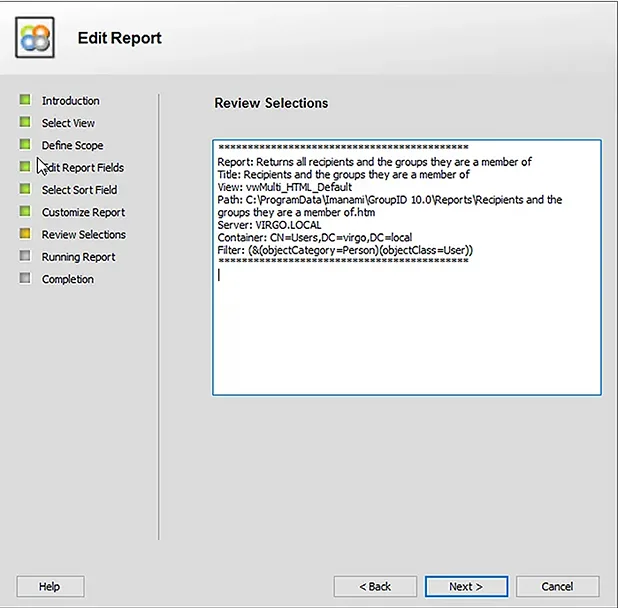
You can review your selections and edit them if you are not satisfied with the query.
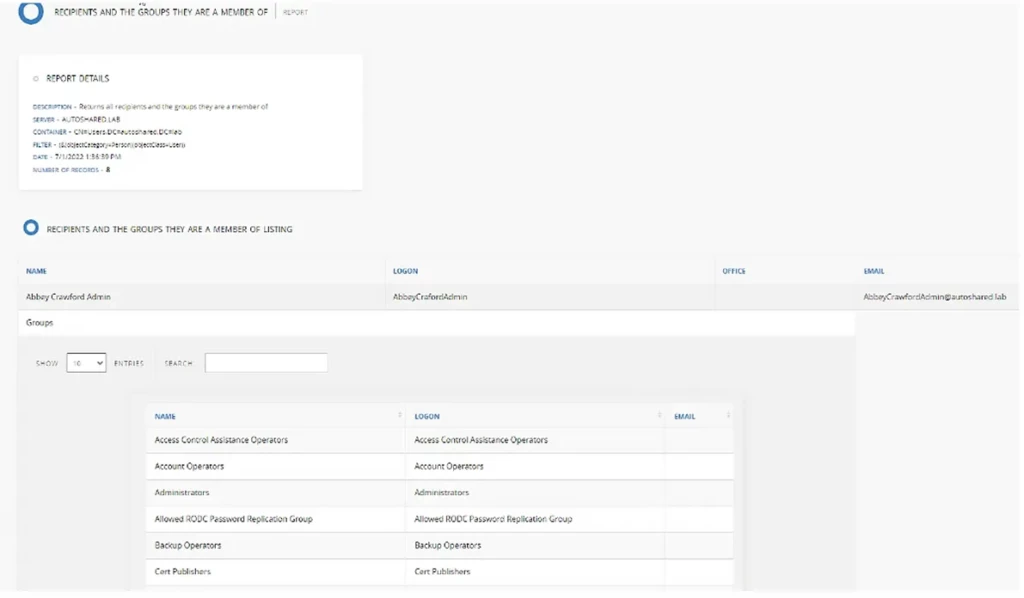
You will get the report as a webpage, as shown below. Alternatively, you can choose to have the output in Excel or XML format.
Conclusion
Administrators have several methods for getting the group memberships of an AD object. One powerful option is the Get-ADPrincipalGroupMembership cmdlet. An easier method is to use Netwrix Directory Manager Reports, which eliminates the need to learn PowerShell cmdlets and write scripts.



