Salesforce is an incredibly powerful system that nearly every department in an organization relies on. But as the platform evolves and businesses grow, complexity grows along with it — and without effective controls for managing that complexity, businesses can expose themselves to risk.
Ultimately, risk is determined by two things: who can access the system, and what they can do in it. Which leads us to good news, and bad news.
The good news is that Salesforce comes out of the box with a suite of powerful tools for monitoring security, as well as support from a world-class SecOps team. The bad news is that that complexity we mentioned above — it means businesses need to work harder to use those tools effectively.
We’ve put together a bunch of links and other resources on this page that will help you better understand Salesforce security — how it works, what’s at stake and what you can do to build a tighter Org from the ground up.
Salesforce Security Assessment: Understanding Risk
Risk assessment in IT systems will always involve some degree of triangulation. Systems leadership must consider several factors, including the value of the asset at risk, the severity of the threat and the cost involved in mitigating it. So before we start looking at the nuts and bolts of data security in Salesforce, it’s worth reviewing some general risk management best practices.
Free Salesforce Security Tools and Resources
Your organization chose Salesforce for a reason — the platform’s ubiquity means there are plenty of resources and tools available for managing security. Some of them are in your Org today; others are available through the extensive third-party ecosystem of Salesforce apps and thought leadership.
Salesforce Health Check
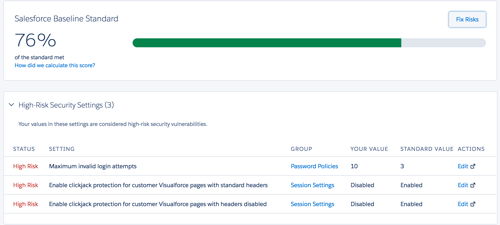
The Salesforce Security Health Check is a tool included with almost all versions of Salesforce. It helps systems leadership quickly identify potential vulnerabilities in your security settings, and monitor overall security health on an ongoing basis.
Running the Salesforce Security Health Check is one of the first things you should do to improve security in your Org.
Salesforce Data Classification
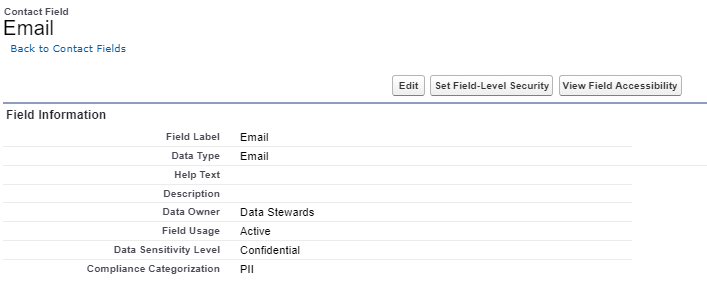
Salesforce introduced data classification metadata fields as part of its ‘19 summer release. This feature allows you to add data classification tags to any field in a standard or custom Object. By identifying data that’s more sensitive, or in scope for regulatory compliance, you can build more effective controls to protect it.
Data classification is critical to data governance, which in turn is a key part of overall Salesforce security.
Flashlight by Netwrix Strongpoint
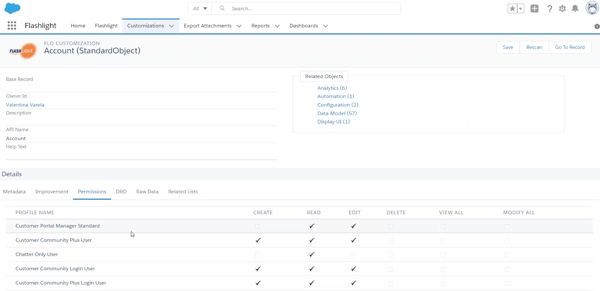
Our free tool, Flashlight, scans your Org to produce a continually updated record of how it’s customized. With it, you can review access controls (more on this below), and identify technical debt that prevents you from building effective data security controls. Flashlight also includes a suite of impact analysis tools, which will help you see the hidden connections between Objects, fields and automation — and understand with minimal investigation what can affect sensitive data in your Org.
Salesforce Access Controls and Access Management
Maintaining tight controls over who can access your Salesforce Org — and what they can do when they’re in there — is your first line of defense against security breaches in Salesforce. Not only do you need effective password policies, you need to make sure your internal access controls are structured in a way that preserves the principle of least privilege — while still enabling users to access the functionality they need to do their jobs.
Between sharing settings, roles, profiles, permission sets and more, access in Salesforce is a complicated topic — full discussion of which is beyond the scope of this page.
Salesforce Security: Best Practices for Access Management
You might have the best security software and most comprehensive staff policies, but as it’s told: security is a joint responsibility between you and your system. Your actions play a huge role in the safety of your Salesforce Org, and while security awareness is important — taking premeditative action is your best bet at keeping your Org safe.
1. Develop Onboarding and Offboarding Policies
Onboarding and offboarding is a critical time for data security. It’s important to ensure IT and HR are in alignment on how to effectively manage user roles and access privileges when an employee starts or ends their tenure with your organization. Having a formalized process will ensure your employees have all of the resources they need to be successful in their role — and that your business is protected from security threats in the process.
2. Review and Restrict Admin, Full, and View Access
Only a small group of authorized personnel should be able to view and edit business-critical information — but if you don’t have time for a comprehensive access review, start by making sure only Admins have the System Administrator profile. Then, work towards implementing the principle of least privilege — restricting employees’ access rights to the minimum required to do their job.
3. Cleanup Unused Permissions
Cloud environments like Salesforce make it very easy to grant wide-ranging permissions — but when roles change or an employee leaves the company altogether, their previous roles and permissions aren’t usually removed. Cleaning up any unused or inactive permissions is a good first step in protecting your account from unauthorized user access and insider attacks.
Key Netwrix Strongpoint Features
Netwrix Strongpoint was designed to help with some of the most time-consuming parts of access management and data security in Salesforce. Here’s a look at three key features that will save you hours of work, while helping you build more effective controls.
- Roles, Profiles, and Permission Set Monitoring: Netwrix Strongpoint lets you create policies that monitor for changes to specific profiles or permission sets — and log everything in audit-friendly reports [insert image]
- Field Access Review: A complex object in Salesforce may contain multiple custom fields, standard fields, formula fields, record types, picklist values, buttons and links. Netwrix Strongpoint gives you easy-to-work-with reports and spreadsheets showing all settings attached to an Object, profile or permission set.
- User/Profile/Permission Set Review: Netwrix Strongpoint helps you get an in-depth look at everything a user can see and do. With out-of-the-box reporting, Netwrix Strongpoint makes it easy to perform detailed reviews and determine who has access to sensitive data: [insert image]
Change Management for Salesforce Security
Salesforce Orgs are constantly changing. The platform’s ‘low-code/no-code’ development makes it very easy to add or modify fields, Objects, etc. Access controls will ensure that only authorized users are able to make these changes. But access controls can’t account for the complexity of an evolving Org — in other words, even authorized users with the best intentions can do things with unanticipated downstream security risks.
Building more accountability and security into your change processes is an important corollary to building tight access controls in Salesforce. But what does that look like in the real world?
What drives change in Salesforce?
The Salesforce platform is constantly evolving — and the businesses that use it are evolving, too. Even if you continue to use it exclusively as a CRM, it’s not uncommon to see your Org undergo almost constant change as you manage the demands of growth, security and compliance.
In a perfect world, all changes in your Org would be planned and follow a strict change management process. However, changes are sometimes driven by urgency or unexpected errors, and unfortunately, these unplanned changes — think, making a quick fix to push out a new release on time — are hard to track, and can have detrimental downstream impacts.
What are the risks of change?
Even a change that seems simple — modifying a picklist, for example — can have a downstream impact on critical financial reporting or system functionality. As a result, Salesforce teams are faced with two extremes: spend hours on discovery with each change — something that’s virtually impossible to do in a busy Org — or accept risk and manage things reactively when something breaks.
In reality, most Salesforce teams will do a mix of both — but what if there was a way to formalize and automate this, and base decisions on actionable intelligence rather than one admin’s understanding of the system?
Best Practices for Enabling Change in Salesforce
1. Impact Analysis
To make changes safely, you need to be able to see how Objects and fields are connected. For example, if you are going to make a change to a field in the Account Object, you need a list of all the reports, layouts, formula fields, dashboards, etc. that reference it — in other words, anything that could be affected when you make that change.
Normally, admins and developers rely on their own understanding of the system to make the changes. But as things mature, this process becomes riskier, and can require extensive discovery that makes it difficult and time-consuming to evolve your Org as the needs of your business change.
2. Change Logging
Salesforce’s Setup Audit Trail logs modifications to a wide range of change types, and collects them in an exportable file showing what the change was, who made the change, and when it was done. It tracks changes to everything from company and currency information to profile and permission set details.
Field History Tracking allows you to select individual fields in a Standard or Custom Object and automatically track any changes within them. It captures the date and time of the change, who made it, and other important details, and retains it for up to 18 months.
These two tools can help build additional security into your change management process (especially if you’re a public company that’s subject to SOX). But there’s a lot they can’t do.
3. Change Policies
With impact analysis to determine the potential security and compliance risks of a change, you can build formal policies for mitigating those risks. The fact is that many changes in Salesforce are safe, and can be handled by a developer or admin. But some aren’t, and will require review by Finance or IT, or testing across a full SDLC. When you know which is which, you can dedicate resources accordingly.
From a Salesforce security standpoint, this is a huge benefit — safe and simple changes can be fast-tracked, and more complex changes can get the scrutiny they require, from the right authority. As a result, nothing slips through the cracks, and IT can focus on big-picture systems security rather than simple, declarative changes.
Key Netwrix Strongpoint Features
Netwrix Strongpoint is the most comprehensive change management system in the Salesforce ecosystem. Track all development activity in the system — including hard-to-monitor configuration changes — build policies for protecting in-scope Objects and fields, and capture everything in audit-ready reports.
Salesforce Security and Compliance
Auditors will often want to see that you have broad Salesforce data security policies to protect the integrity of the system as a whole. Change and access controls will need to be integrated into a larger data security monitoring system, such as Netwrix Auditor or Netwrix Access Analyzer.
Data and Metadata Backups
Salesforce maintains a fully redundant network architecture and regularly backs up customer data and metadata at the “instance” level. But the company also encourages customers to independently back up their Orgs — and auditors may very well ask to see proof that this recommendation is followed.
Salesforce gives you several ways to back up your data:
- Using the Data Export Service, which lets you schedule exports of your data via the UI
- Using the Data Loader, which lets you manually export your data via the API
- Using the Report Export tool, which lets you manually export your data via reports
Additionally, it is possible to backup metadata to a Sandbox Org using change sets or Sandbox refreshes. There are several third-party tools that will do this.
Netwrix Access Analyzer
We recommend Netwrix Access Analyzer for reporting around data security. Netwrix Access Analyzer automates the collection and analysis of the data you need to answer the most difficult questions you face in the management and security of dozens of critical IT assets, including data, directories and systems.
Event Logging
SOX auditors may want to produce a list of users who viewed or exported a financially relevant record. Salesforce recommends the paid add-on Shield Event Monitoring to handle this.
Event Monitoring produces highly granular, forensic logs of user activity in Salesforce as part of a data loss prevention program (DLP). Again, this will usually apply across multiple systems in addition to Salesforce.
Salesforce Field-Level Security
Maintaining both compliance and data integrity requires implementing field-level Salesforce security controls. In Salesforce, this can be done through access controls. But when you integrate with an ERP or accounting software, the challenge becomes ensuring that those permissions are maintained in both platforms.


