Data is the lifeblood of any organization today, and therefore data loss is a pressing concern for IT teams and the C-suite alike. Data loss has a wide range of causes, from hard drive failures to data leaks by malicious insiders or external hackers. The consequences of data loss also vary widely. Crucial business processes can easily be disrupted, and having a critical document end up in the hands of a competitor can be devastating. The organization can also face compliance fines and loss of customer trust. All of these factors can hurt revenue, even to the point of putting the company out of business.
To minimize these risks, every organization needs to have a data loss prevention (DLP) plan that safeguards critical data.
Designing an effective data loss prevention program
Effective data loss prevention requires a broad approach. It’s important not to give in to the temptation to select a single software program and think you’ve done enough. The data you’re protecting is too important and the potential fallout from its loss is too severe. Here are the steps involved in establishing a truly effective DLP program.
Step 1: Get executive buy-in.
First, secure approval from leadership, including the heads of all departments and divisions that may be impacted. Their support is necessary for the success of the program.
Step 2: Identify and classify your critical data.
Distinguishing critical data from non-critical data is perhaps the most important step in creating a data loss prevention program. Here are some of the types of data you might need to identify:
- Intellectual property (IP)
- Legal documents
- Strategic planning documents
- Sales data
- Customer information
- Personally identifiable information (PII)
- Marketing data and forecasts
- Operations documentation
- Financial records
- Human resources data
- Government data
- Passwords and other IT data
- Data subject to any compliance regulations
Tag each piece of critical data with a digital signature that indicates its classifications, so your various software solutions can handle it appropriately.
Step 3: Identify threats and risk.
Model the activity around each kind of critical data, including who accesses it and what they do with it. Identify any threats to the security of each piece of data. What vulnerabilities are present at each point in the data’s lifecycle? Who is responsible for the data’s secure use? Do they have the tools that they need to protect it?
Detail what might happen if the data is lost. Be sure to consider both the direct impacts to the business and compliance penalties.
Step 4: Define your objectives.
Specify what goals you want the DLP program to achieve, such as:
- Identifying risks and ways to address them
- Safeguarding data in motion, in use and at rest
- Keeping data available for use without increasing risk
- Standardizing procedures for security, privacy and compliance
Step 5: Create step-by-step procedures.
Establish processes and policies for storing and handling critical data, as well as detailed response plans for data leaks and other security incidents. The following chart offers some proven best practices for the safe handling of critical and sensitive data; be sure to create procedures to implement each of them.
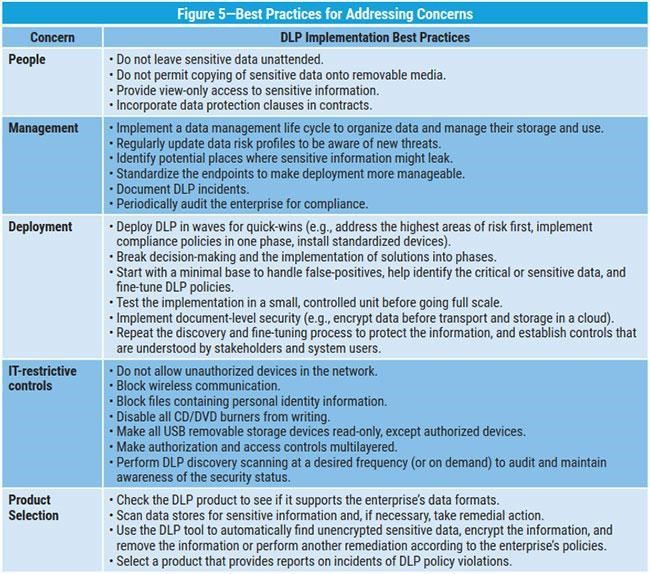
Source: https://www.isaca.org/Journal/archives/2018/Volume-1/Pages/data-loss-prevention-next-steps.aspx
Step 6: Evaluate current and available systems.
Consider whether your existing hardware and software can meet your DLP goals. Remember that most data protection systems cannot classify data accurately and consistently. If your current systems are insufficient, evaluate other solutions, keeping both your goals and your risk/cost analysis in mind. What functionalities do you need and how much are they worth to you?
Step 7: Educate everyone.
Build awareness within the organization about the importance of the DLP program. Include information about:
- What constitutes critical data
- How critical data should be handled in certain situations, including email and internet use
- Which laws the company must comply with
Tailor the training to the needs of different groups of employees, and repeat it on a regular basis. Be sure to periodically test your users and follow up with individuals who do not follow the proper procedures.
Benefits of a strong data loss prevention program
The better your data loss prevention program is, the more secure your data will be. In addition, you will be better prepared for compliance audits, including those related to the National Institute of Standards and Technology (NIST) data loss prevention guidelines for federal entities. NIST DLP programs include the Cybersecurity Framework, which includes recommendations that support compliance with other regulatory systems, such as FISMA and HIPAA.
The cornerstone of DLP: automated data classification
The most important part of any data loss prevention program is data classification. Unless you know what kinds of data you have, you can’t protect that data appropriately.
Netwrix Data Classification delivers the accurate, consistent and flexible data classification you need across your on-premises, cloud or hybrid IT environment.



