No organization is immune to data security threats. But as your IT environment becomes more complex — for example, through the adoption of cloud technologies — it’s even harder to implement the data protection you need to protect your business. Many organizations struggle to protect critical data, such as intellectual property, personally-identifiable information covered by various regulations, and sensitive financial data.
The best way to help prevent data leaks and data loss is to build a layered defense strategy. You need to reduce your attack surface, actively look for suspicious activity and insider threats that could lead to data breaches, and plan an effective response strategy.
Data loss prevention (or DLP) is a critical component of any effective strategy. In this article, you will learn what DLP is and why it is worth your attention, what types of data loss prevention methods exist, and how to choose the best approach for your organization.
What is DLP?
Data loss prevention processes are information protection practices designed to protect sensitive or critical information in the corporate network from being lost, misused or accessed by unauthorized people. Data loss prevention controls help mitigate the risk of data leakage, data loss and data exfiltration by ensuring that sensitive information is identified and risk-appropriate controls are deployed, with minimal impact on business processes.
DLP is a process, not a single piece of software, and it is just one component of your comprehensive data protection program.
If you’re just getting started with data loss prevention, remember that data governance should come before DLP. Effective data leak protection requires knowing what critical data you store and having policies and rules about storing, using and moving that data. For example, if your file server permissions are not configured properly and reviewed regularly, your DLP process will produce false alerts that can lead to costly improper responses, such as blocking legitimate activity that is essential for a critical business process.
How does DLP work?
Data loss protection involves three primary tasks:
Analyze and classify content. A critical prerequisite for data loss protection is understanding your data, both on premises and in the cloud. The best approach is to use automated data discovery and classification technology to scan your data repositories and tag all critical, sensitive or regulated data with digital signatures that indicate whether it is, for example, a medical record, financial data or intellectual property. That way, you can use DLP to protect data in accordance with its value to the organization.
Link to context. Enterprise data can be at rest, in motion or in use, and each state involves different vectors for data loss. Data loss prevention technologies help mitigate these risks by analyzing the context of each action or event, such as who is copying the data, which machine it’s
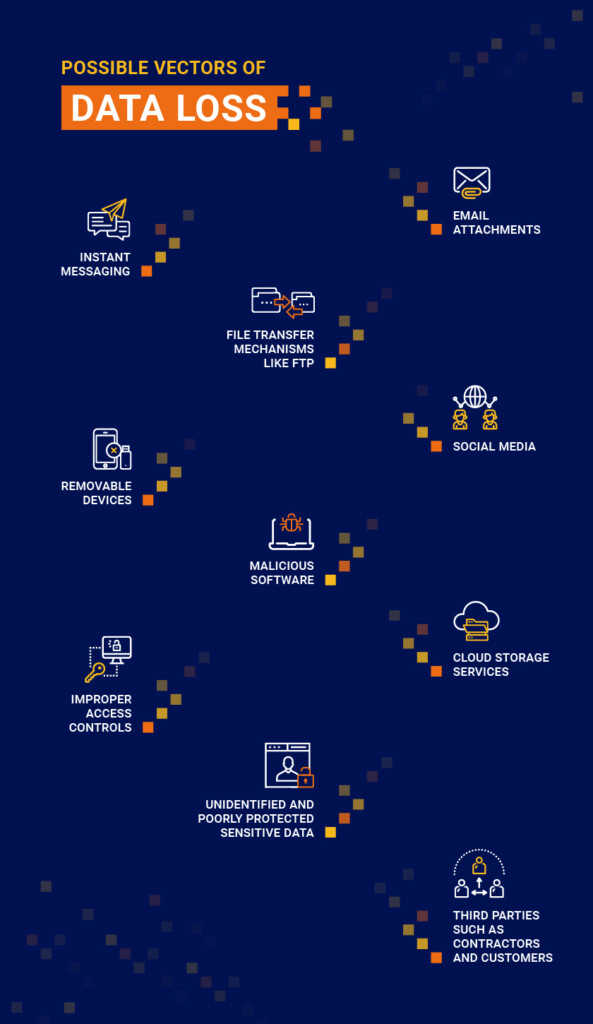
Compare with policy and act. This process is specific to DLP solutions that rely on business rules, policies and conditions to detect improper or malicious activity, such as an attempt to copy sensitive data onto removable media in violation of corporate rules. The DLP policies specify the action to be taken when a given condition is met, such as allowing or blocking the activity, suspending the account, or reporting the event to the security administrator.
Types of data loss prevention
Types of data loss prevention available on the market today include:
Network data loss prevention. Secures all network communications, such as email and web applications. DLP in networking is designed to control and protect information flows over the network using techniques like automatic data encryption.
Endpoint data loss prevention. This type of DLP protects data at the computer level, so it’s not dependent on the corporate network. For example, endpoint DLP can encrypt all data that is transferred to portable devices, or enable admins to scan for sensitive data at rest on computers company-wide and take remediation actions if it is being stored or handled improperly.
Data identification is the process of detecting sensitive or critical information using predefined categories. Your DLP data identification is only as good as your data classification; if sensitive data is not tagged properly, it could be left unprotected. Unfortunately, many organizations rely on user-driven data classification, which is notoriously inconsistent inaccurate. Using an automated data discovery and classification solution will help ensure reliable and accurate discovery and classification.
Data leak detection. Spotting data leaks effectively requires monitoring user behavior across the environment over time to develop a baseline of normal activity, and then actively looking for unusual behavior. This is not a primary function of DLP solutions, so it’s wise to augment your DLP process with a tool that provides advanced user behavior analytics.
Protecting data in motion. Confidential data is often transmitted within the organization or to outside parties, such as the bank and user involved in a payment transaction. DLP can help ensure that data is not routed to improper recipients or insecure storage areas.
Protecting data at rest. These DLP technologies are designed to protect data residing in databases, cloud repositories, computers, laptops, mobile devices and other storages. Their capabilities can include data discovery and classification, encryption, blocking of inappropriate activities, and data deletion. However, most DLP technologies will not show you which data in your environment is available to employees that shouldn’t have access to it, or data that is stored in places where it should not be kept. To fill these gaps, consider investing in data access governance and data remediation tools.
Protecting data in use. Data needs to be protected as it is being modified, uploaded via a browser, copied to the clipboard, and so on. Techniques include ensuring proper authentication and controlling data access rights granted to users, applications and endpoint processes.
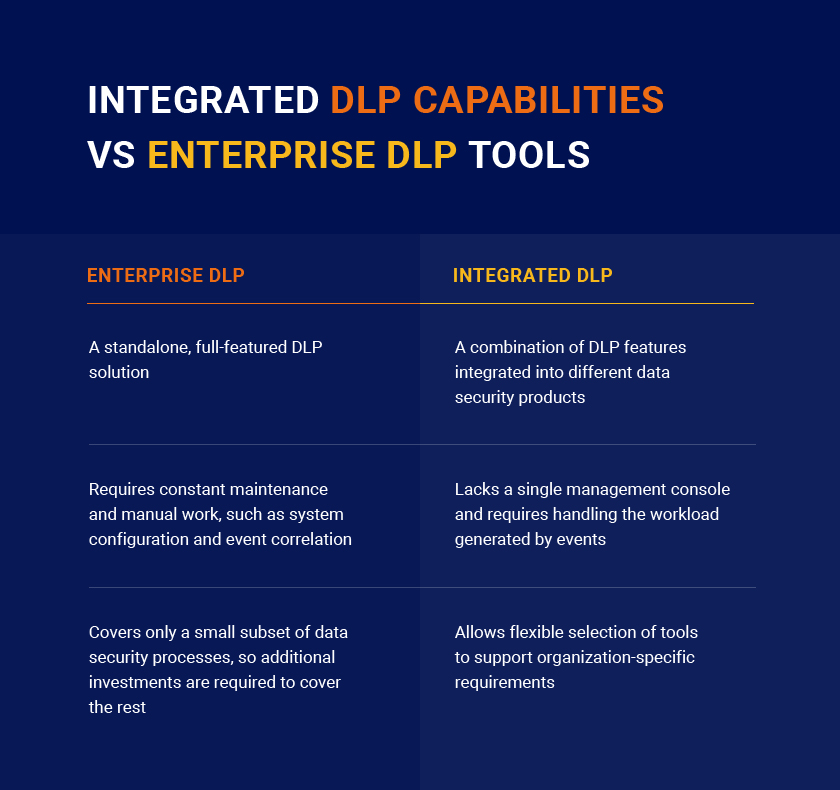
Comparing DLP approaches
Comparing DLP approaches
The breadth of data loss prevention solutions available can be overwhelming. To understand the approaches taken by different vendors and how well various solution perform their core task, read the Gartner paper, “How to Choose Between Enterprise DLP and Integrated DLP Approaches.” As this paper notes, before you rush to purchase a full-featured enterprise DLP solution, figure out what DLP capabilities are included in the solutions you already own. Look at your antivirus software, firewalls, endpoint protection, IT asset management, identity management, secure web and email gateways, log analysis tool, and data discovery and data classification solution. Although they are not DLP products in the conventional sense, they do fulfill certain data protection goals. Gartner estimates that “by 2021, 90% of organizations will implement at least one form of integrated DLP, an increase from 50% in 2017.”
Here are some key points to keep in mind as you choose how to implement DLP in your organization:
Trends driving DLP adoption and alternative methods to deal with these issues
What are the main drivers for implementing data loss prevention practices and procedures?
Personal information protection and regulatory compliance. To satisfy compliance requirements, companies need to demonstrate the maturity of their security programs and controls to auditors, and having DLP practices in place can play an important role in passing audits. However, standards like HIPAA, GDPR and PCI DSS have requirements that cannot be addressed by DLP alone, such as minimizing access entitlements and tracking user activity, including access to systems and data usage,. For example, DLPs don’t do entitlement reviews, log user activity around sensitive data unless it violates policy, or help you assess the scope of data involved in a breach.
Intellectual property protection. Loss or theft of your IP can mean losing market advantages, profitability, and even entire lines of business to competitors. DLPs help ensure secure access to IP by monitoring user behavior at potential points of compromise and blocking inappropriate activities.
Conclusion
To protect your critical data against attacks and accidents, you need a layered strategy for data loss prevention. No single enterprise DLP tool can solve all your data security problems; DLP requires a comprehensive process. To get started, assess the capabilities of the tools you already have against your company’s business needs. You might be surprised to discover how much they can provide, enabling you to save your budget for crucial foundational technologies like data discovery and classification.
FAQ
What is data loss prevention (DLP)?
Data loss prevention (DLP) refers to tools and processes that protect critical information from being accessed or stolen by anyone without proper permissions. DLP controls help reduce the risk of data leakage, data loss and data exfiltration by ensuring that sensitive information is identified and risk-appropriate controls are deployed, ideally with minimal impact on business processes.
Why is DLP important?
Data loss can result in wide variety of repercussions for the organization, including lawsuits from the people whose data was exposed, penalties from regulatory agencies, and damage to both your business reputation and bottom line. DLP controls help you analyze data and activities and prevent the movement and use of data outside of defined boundaries. DLP also helps you enforce security policies, meet compliance standards and gain better visibility into data across various systems.
What techniques are commonly used for DLP?
Strategies often used for DLP include:
- Network data loss prevention secures network communications using technologies like data encryption in order to control information flow and protect data.
- Endpoint data loss prevention protects data on workstations, laptops and other endpoint devices.
- Data identification involves locating sensitive or critical data based on predefined categories.
- Data leak detection monitors user behavior for activity that could indicate a data leak, usually by establishing a baseline of normal activity and looking for unusual actions.
- Protecting data in motion refers to ensuring that data moving along a network does not get routed to unauthorized recipients or end up in an insecure storage area.
- Protecting data at rest involves building protections around data held in repositories like databases, computers and mobile devices.
- Protecting data in use refers to securing data in various action states, such as an update being received, a file getting uploaded, or content being copied from one place to another.
What does DLP protect?
DLP guards sensitive or critical information in three states: in motion, at rest and in use. Many DLP tools have prebuilt libraries of hundreds of well-known data types, such as personally identifiable information (PII), financial data, and data regulated by mandates like HIPAA and GDPR.
What is a DLP strategy?
A DLP strategy details how the organization will watch for security threats and potential data breaches or data loss. It should include an overview of the solutions implemented and the types of information to be protected. To prevent data leaks, it’s important to classify your data, identify your risks, put the right practices in place to protect data, increase security awareness among all users, enable fast incident detection, and create and regularly test a recovery plan.
What does a DLP tool do?
A DLP tool is part of an overall strategy to keep sensitive data from getting stolen, misused or improperly accessed. DLP tools inspect content in order to identify sensitive and regulated data, and also monitor and analyze how that data is being accessed and used. If the DLP tool spots actions that are unusual for a given user or not permitted by the organization’s security policy, it takes the steps defined by administrators, such as automatically blocking access and notifying the appropriate team.



