Traditional endpoint security often overlooks critical layers like privilege control, automated policy enforcement, real-time visibility, compliance assurance, and modular scalability. To reduce risk, organizations must enforce least privilege, detect drift, monitor devices, prove compliance, and integrate tools that adapt to evolving threats across all endpoint types and configurations.
Most posts about types of endpoint security mention antivirus software, firewalls, or maybe EDR/XDR. And while those security technologies are important, they’re not enough.
Cyberattacks have evolved. Today’s cyber threats target laptops, smartphones, and even IoT devices. Ransomware moves laterally. Zero-day exploits bypass signature-based defenses. Phishing attacks hit the end-user, not just the firewall.
That’s why a modern endpoint security strategy must go beyond traditional antivirus and signature-based detection. You need tools that can automate policy enforcement, reduce your attack surface, and give security teams full visibility into potential threats.
In this article, we’ll walk through five overlooked layers of endpoint protection, show how they work together, and explain how to implement them inside your organization’s network.
1. Overprivileged Users: A Silent Threat
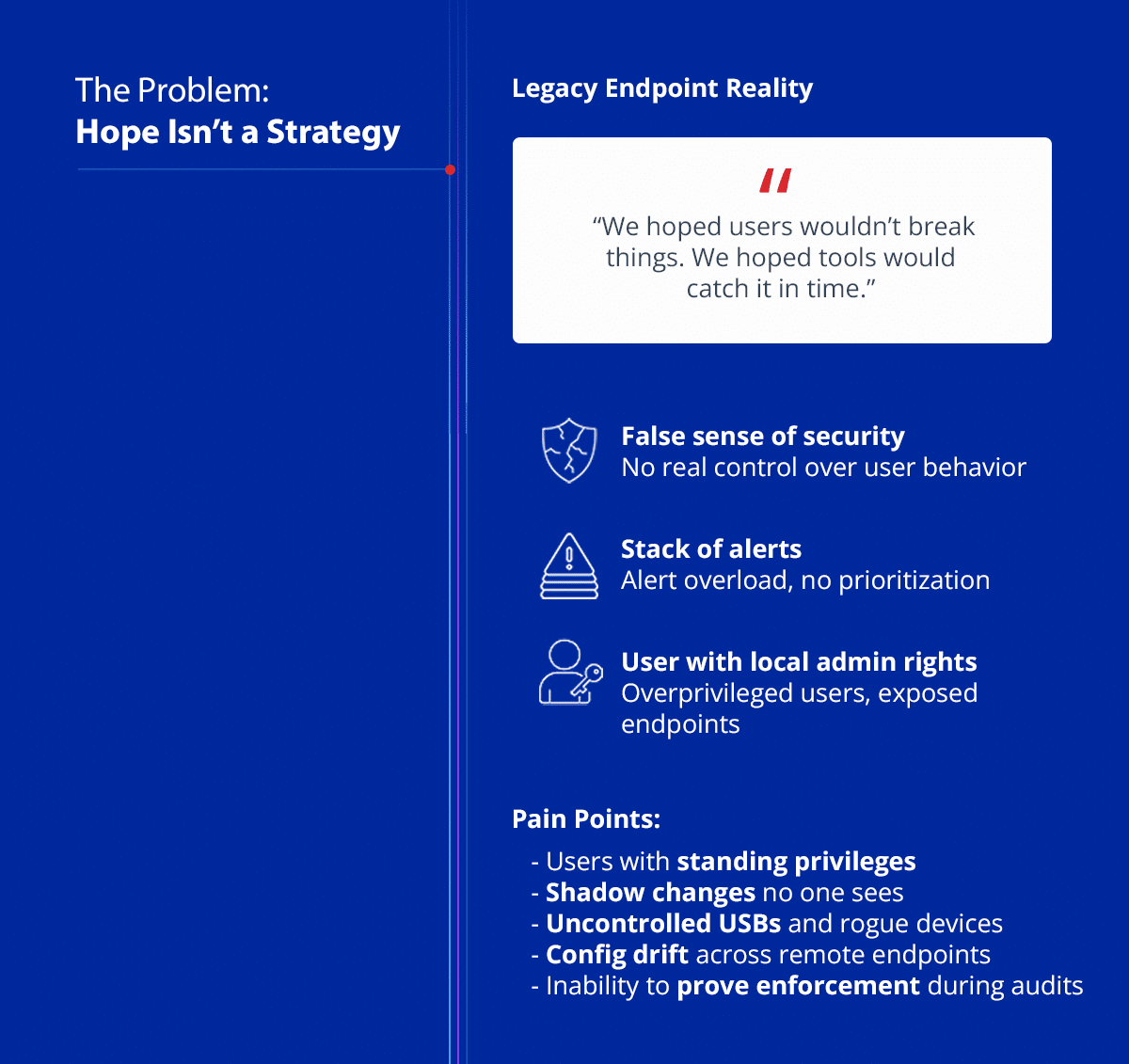
Most cybercriminals don’t break in – they log in. And if users have local admin rights? You’ve just handed them a master key. Overprivileged users with local admin rights create massive vulnerabilities for malware, ransomware, and unauthorized changes.
This first overlooked type of endpoint security solution isn’t a tool — it’s a gap in your security policies.
- Remove standing privileges
- Enforce least privilege access across endpoint devices
- Prevent rogue applications and unauthorized access
Endpoint protection platforms (EPP) that address privilege risk can reduce both insider threats and advanced threats.
2. Policy Enforcement: Control That Sticks
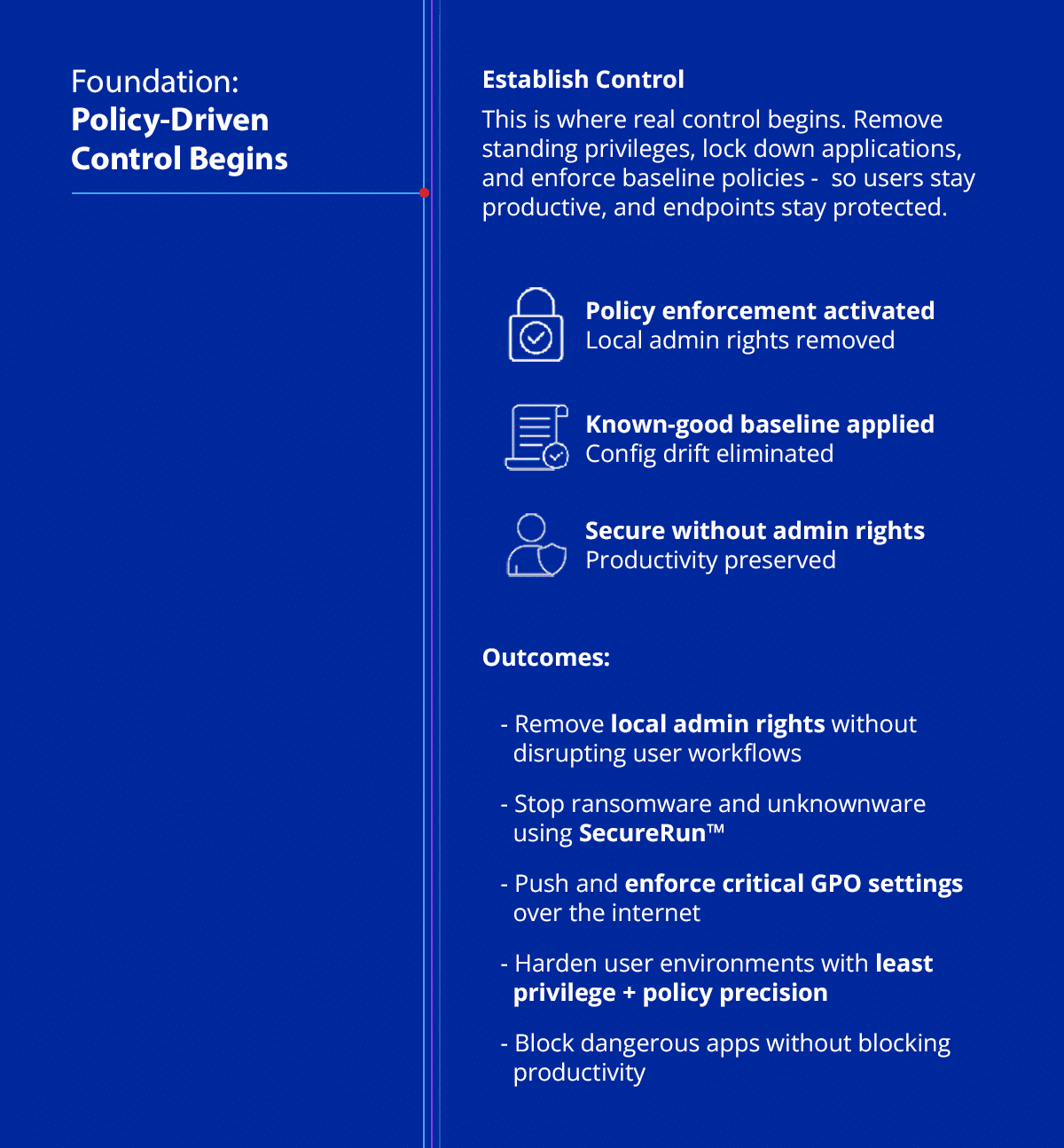
Your users might be secured – but are your security configurations?
Policy drift is one of the most common entry points for breaches. That’s why your endpoint management solution must automate enforcement of secure baselines.
- Apply and verify Group Policy and MDM settings
- Stop ransomware and malware with tools like SecureRun™
- Enforce baselines across on-premises, cloud-based, and BYOD endpoints
This layer ensures that even mobile devices, BYOD laptops, or connected devices in the corporate network can’t silently bypass your controls.
3. Real-Time Visibility & Device Control
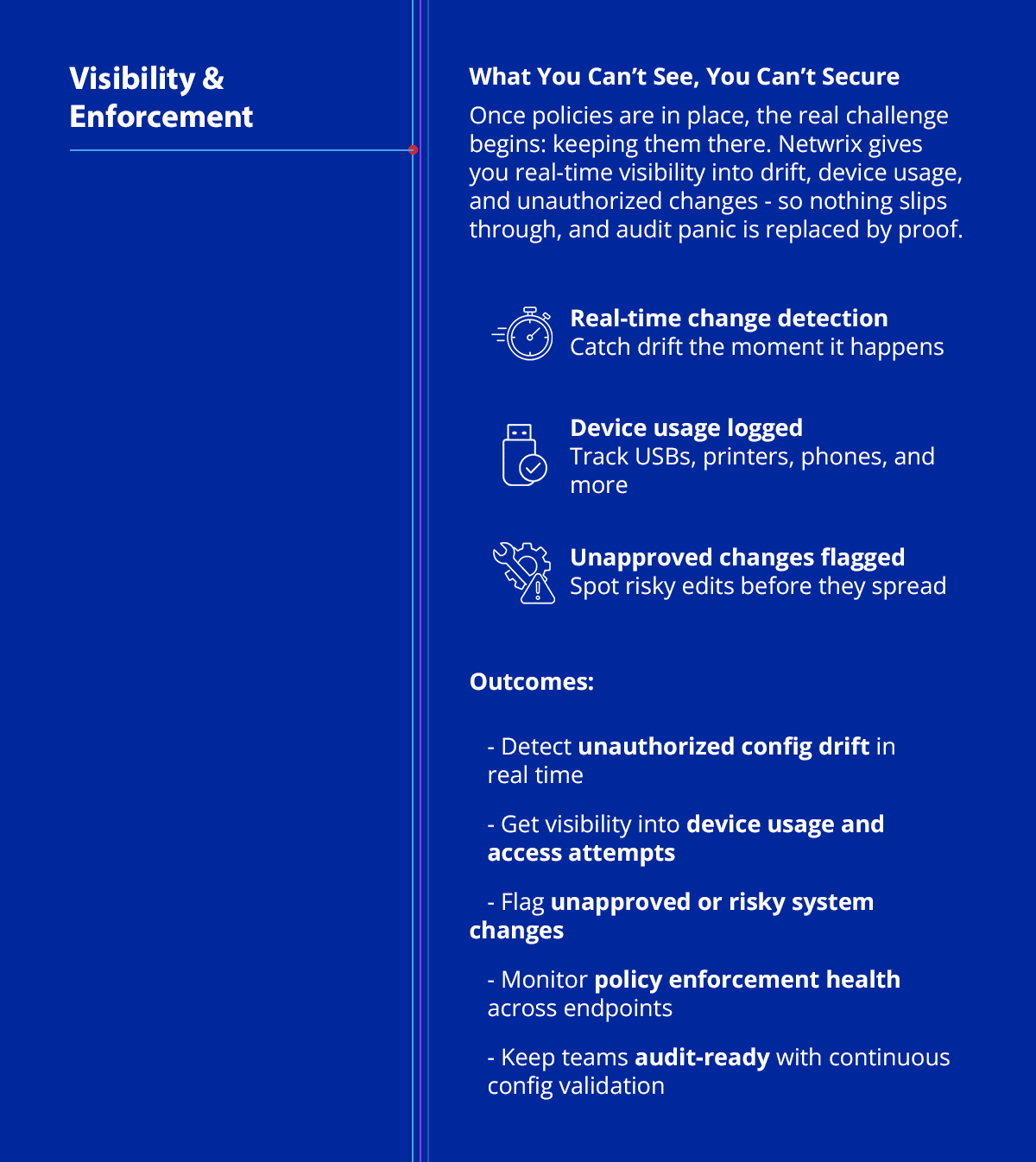
Once policy is enforced, the next step is knowing when it breaks — in real-time.
Misconfigured settings, unauthorized USB devices, and insider actions often go unnoticed without continuous monitoring or threat detection capabilities.
- Detect config drift, unknown threats, and system-level tampering
- Monitor network traffic and behaviors from connected devices
- Log all device activity (USBs, smartphones, printers, etc.)
This is where EDR solutions, sandboxing, and automated responses combine to enable rapid remediation and incident response.
4. Compliance Assurance: From Policy to Proof
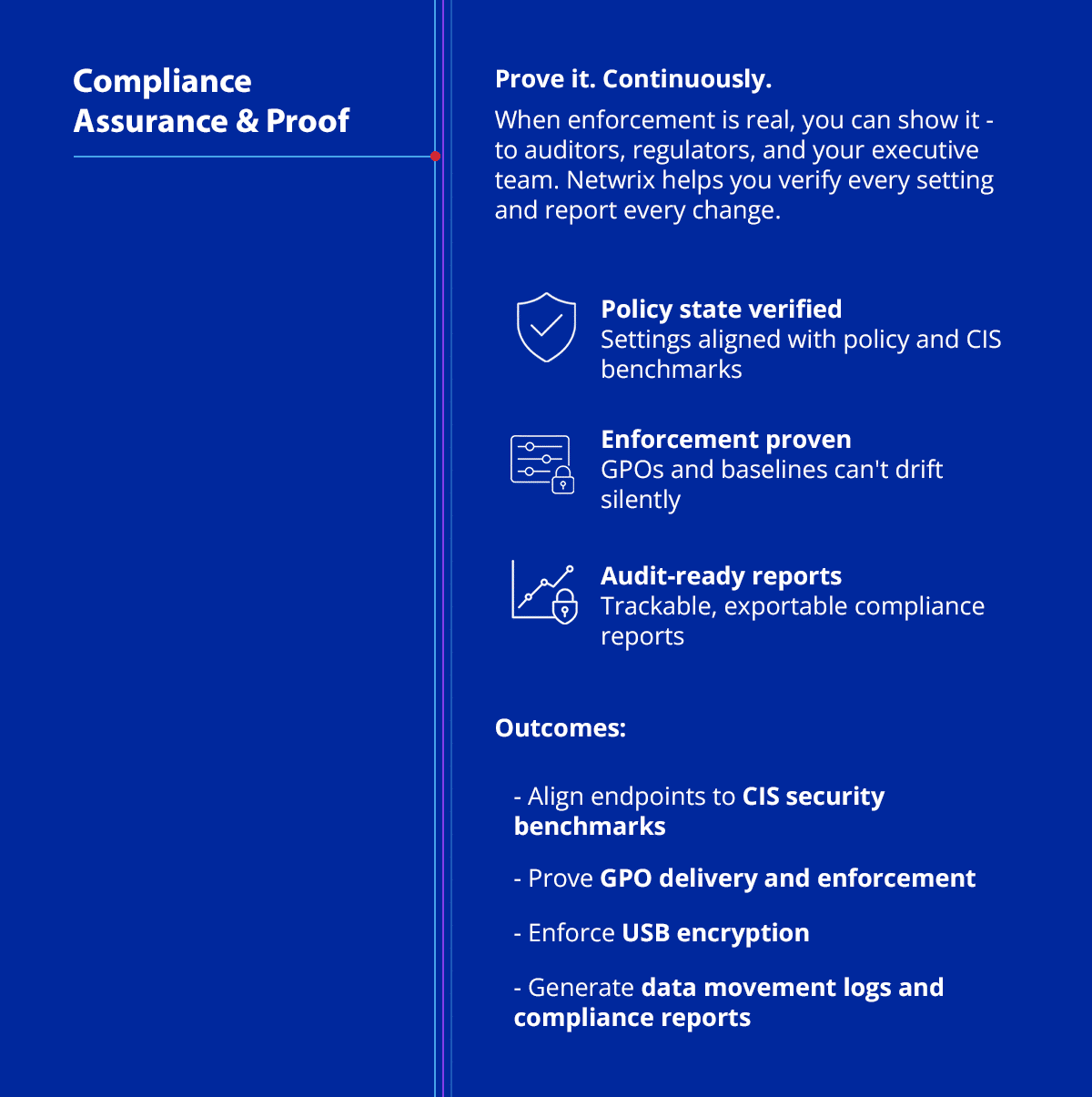
Most compliance frameworks (HIPAA, PCI, ISO) don’t just require controls — they require proof of control.
This layer ensures your security teams can deliver that proof — across any endpoint security tool or operating system.
- Prove policy enforcement across all endpoint devices
- Export audit-ready reports from one interface
- Align with CIS, NIST, or zero trust frameworks
This closes the gap between security incidents and response capabilities, and turns your controls into evidence.
5. Modular Control That Grows With You
Your tools should fit your growth — not limit it.
Modern endpoint security software should be modular, scalable, and focused on functionality over bloat.
- Mix fine-tuned access or hard blocks — per policy
- Connect your EPP, EDR, and Change Tracker into one platform
- Expand from anti–malware to behavioral analysis, authentication, and centralized management
You don’t need to rip and replace. You need tools that automate, scale, and support your evolving endpoint protection goals.
Conclusion: No More Blind Spots
Most organizations don’t lack tools — they lack enforcement, visibility, and proof.
The most effective endpoint security strategies cover more than just malware. They include:
- Privilege control to reduce your attack surface
- Policy enforcement that applies across network-connected devices
- Real-time detection and automated response
- Compliance readiness you can prove
- Modular functionality that works with your existing stack
Want to rethink your endpoint security posture? Not just protect it – prove it?
- Explore Netwrix Endpoint Management – unify privilege control, device access, and drift detection.
- Read more on What Is Endpoint Policy Management? Why Intune isn’t enough – Discover how policy-driven control goes beyond MDM.
- Get the Endpoint Management Manifesto – your blueprint for policy enforcement, audit readiness, and real-time visibility.



