Manual account provisioning is error-prone and doesn’t scale. Automated user account management speeds onboarding and offboarding, enforces least privilege, and maintains audit trails for compliance. The best tools integrate with HR and cloud directories, support Zero Trust and MFA, and give IT and users self-service capabilities — boosting both security and productivity.
Each individual in your organization needs a user account to access data, applications, servers, cloud services and other resources. If you have just a few accounts, you may be able to create, secure and govern them throughout their lifecycle using manual processes.
However, manual processes are highly prone to human errors and do not scale to meet the needs of any but the smallest businesses. Instead, most organizations need automated user management tools. By choosing the right solution, your organization can get the efficiency and accuracy required for strong security, regulatory compliance, and user and IT team productivity.
This article explains the benefits of automated user account management, details the essential features to look for in a tool, and explores the top solutions available on the market. We’ll also review best practices in user account management and offer guidance in implementing a solid strategy.
Benefits of Automated User Account Management
Automated account management offers multiple advantages, including the following.
Time and Resource Optimization
Automating user account management processes can significantly reduce the time and resources needed to handle user accounts throughout their lifecycle:
- Onboarding — Automation allows for rapid onboarding to ensure that new employees, contractors and other users can be granted quick access to necessary systems and applications to enable productivity on day one.
- Role changes — An automated user account management tool also helps ensure that a user can quickly be granted the access they need to handle new roles or responsibilities, and that access they no longer require is promptly removed.
- Offboarding — When individuals leave the organization, the tool can automatically disable or delete the associated user accounts.
Enhanced Security and Compliance
Automating user account management can also elevate your security posture and assist in maintaining compliance with regulatory requirements. In particular, you can ensure that access policies are applied uniformly across all users and systems, and that detailed audit trails are automatically maintained for all account activities for later use.
Streamlined User Experience
Automation can also enhance the user experience through features like the following:
- Self-service capabilities — Users can reset their own passwords or request access to the resources they need without the frustration and delays of helpdesk tickets.
- Single sign-on (SSO) —Enabling users to access multiple applications with one set of credentials reduces password fatigue and increases productivity.
- Faster access provisioning — Automated provisioning means users spend less time waiting for a new account or new access rights to be set up.
Key Features of User Account Management Tools
Core Capabilities
When evaluating user account management tools, be sure to check for the following essential capabilities:
- Broad platform support — The tool you select should support the systems that you rely on and be flexible to meet your future needs. For example, most organizations today use both Active Directory (AD) and Entra ID (formerly Azure AD), so they need a tool that includes centralized user account management and consistent security policies across the hybrid environment.
- Identity management — Automating account management processes helps organization ensure that they have exactly the right set of digital identities, which reduces the risk of unauthorized access.
- Access management — Automation makes it easier to enforce the principle of least privilege, which requires that each user to be granted exactly the access necessary to do their job, with no unnecessary permissions. To achieve this goal, modern solutions use role-based access control (RBAC), rather than assigning access rights directly to users. With RBAC, organizations develop a set of roles that correspond to job roles (like Helpdesk Technician and Sales Rep), grant each role the corresponding access rights, and then assign each user the appropriate roles.
- Configuration analysis — A good tool will also analyze user configurations and permissions to identify vulnerabilities such as excessive permissions and unused accounts.
- Real-time monitoring — The right automated account management solution will track changes to user permissions and monitor access behavior to help ensure that individuals have only the necessary rights to perform their roles. For example, promptly detecting unusual login attempts or changes to roles enables prompt responses to potential threats.
- Compliance features — Account management tools can help organizations achieve and prove compliance with the requirements of data protection laws like the GDPR, payment card standards like PCI DSS, and healthcare information privacy and security regulations like HIPAA. Look for a solution that automatically maintains a detailed audit trail and offers customizable reporting.
Emerging Trends
To ensure that your investment delivers value over the long term, also be sure to look for the following modern capabilities in the solutions you evaluate:
- Support for Zero Trust — The Zero Trust security model requires that no user, device or network be automatically trusted, even if it resides within the local network. Instead, every access request must be thoroughly authenticated, authorized and encrypted before access is granted. In addition, Zero Trust requires continuous monitoring and analysis of user activity, network activity and system behavior to ensure prompt threat detection and response.
- Passwordless authentication — Passwordless authentication eliminates traditional passwords in favor of options like biometrics, hardware tokens, and one-time passwords sent through text, email or authentication apps. This approach improves security by eliminating the serious risks associated with weak or stolen passwords, enhances the user experience by removing the need to remember complex passwords, and reduces IT support costs by decreasing password management overhead, including password reset requests. However, adoption can require significant changes to existing infrastructure and user behavior.
- AI and machine learning (ML) — Modern solutions leverage AI and ML to more accurately analyze user roles and behavior patterns, automate account creation, and predict access requirements based on historical data to help ensure that users have the appropriate permissions from day one. AI and ML to establish accurate baselines of user behavior; spot suspicious deviations like unusual login activity, access attempts or data transfers; and automatically initiate threat response protocols.
Detailed Comparison of Top User Account Management Tools
There are many user account management software solutions available on the market today. Below is are brief descriptions of some of the most popular solutions you may want to consider.
Netwrix Directory Manager
Netwrix Directory Manager automates user and group management to enhance security, compliance and productivity across your on-prem AD domains, cloud environment or hybrid ecosystem. It boasts features like the following:
- Automated creation, modification and deletion of AD groups
- Connection of on-premises AD, Entra ID and HR databases to keep them up to date and enable comprehensive identity management
- A self-service portal that allows users to update their own information and request access
- Role-based access control
- Identification and handling of inactive or obsolete user accounts and groups
- Periodic user access reviews to ensure that employees only have the permissions necessary for their current roles
SolarWinds Access Rights Manager
SolarWinds Access Rights Manager is a unified platform that helps organizations manage user access across their Active Directory or Entra ID environment. In particular, it:
- Streamlines the process of creating and removing user accounts based on predefined templates
- Tracks changes to user permissions and group memberships in real time
- Enables the creation and management of access rights based on user roles
- Streamlines compliance efforts by generating detailed reports on user access rights, group memberships and permission changes
- Traces the source of user permissions to identify unnecessary or redundant permissions
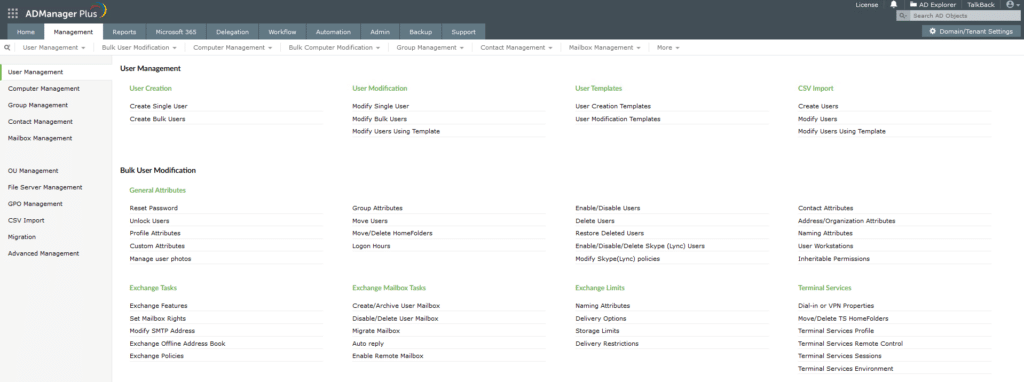
ManageEngine ADManager Plus
ADManager facilitates the work of creating, modifying and deleting user accounts across platforms like Active Directory, Exchange, Microsoft 365 and G Suite. It also supports remote user management.
With this tool, you can:
- Create, update or delete user accounts in bulk using CSV files or templates
- Use PowerShell scripts to schedule tasks and reduce manual work
- Easily generate reports on topics like inactive users, password expiration and group memberships.
A free trial enables you to explore this product and see how it works for your particular organization. Below is a screenshot showing the various management options.
Okta
Okta is a leading cloud-based identity and access management platform that provides flexible user account management capabilities. Some of its key features include:
- Automated user provisioning and deprovisioning across connected systems
- A self-service portal that allows users to update personal information, manage security settings and view account activity
- Privacy controls that allow users to manage their consent preferences and data-sharing options
- Support for biometric authentication and other passwordless technologies
- Synching of the directory with existing user directories such as Active Directory or LDAP
- SSO across a wide range of applications
- Advanced AI and ML capabilities
JumpCloud
JumpCloud is a SaaS solution that lets you provision, manage and de-provision user accounts using a single interface. It eliminates the need for multiple directories or on-premises infrastructure. JumpCloud:
- Supports authentication protocols like LDAP, SAML and RADIUS for both cloud-based and legacy applications
- Integrates with Google Workspace and Microsoft 365
- Integrates with multifactor authentication (MFA) to require users to provide supplementary verification methods
- Enables tailoring of conditional access policies to specific user groups or applications for fine-grained control
- Allows rules that require users to complete additional authentication steps based on factors such as location, device type or risk level
JumpCloud offers a free trial so that you can test it out before becoming a committed customer.
Oracle Identity Management
Oracle Identity Management helps organizations effectively govern user identities and manage access across various systems. For example, it:
- Automates the processes of creating, updating and deleting user accounts
- Enables you to manage user permissions through roles that your admin teams create
- Can synchronize identities from authoritative sources such as HR applications or existing directories
- Allows you to edit user attributes, properties, roles and permissions using a single intuitive interface
- Provides reporting capabilities for tracking user activities, access requests and changes made within the system
Oracle Identity Management is designed to scale for millions of users and integrate seamlessly with Oracle Cloud Infrastructure and applications. It can be deployed on premises or as an Oracle Cloud Infrastructure (OCI) instance.
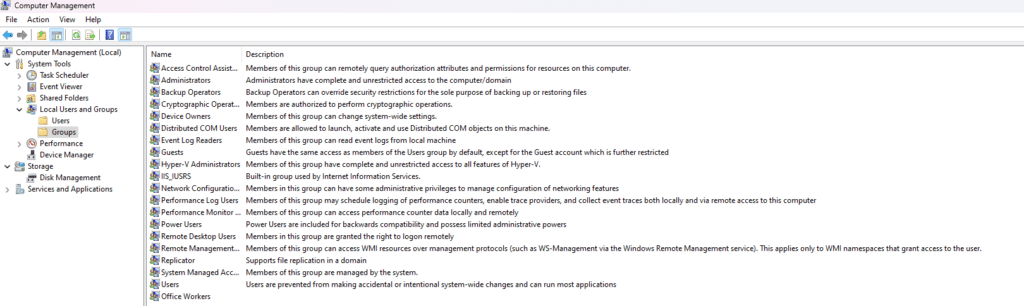
Windows Computer Management Tool (compmgmt.msc)
For efficiency and accuracy, it’s recommended to utilize automated provisioning tools like those described above, especially when managing user accounts at scale. However, Microsoft’s Computer Management tool serves as a basic Windows user management tool. Admins can create, disable and delete local users and groups, as well as perform password resets. The screenshot below displays the default groups available in the Computer Management tool on a Windows 11 machine.
Best Practices in User Account Management
Adopting best practices for user account management helps organizations streamline administration while balancing user productivity with robust cybersecurity.
- Implement standard naming conventions for users and groups. Consistent naming facilitates accurate provisioning, which improves security and productivity.
- Perform regular audits to enforce the principle of least principle. Regular audits of user access rights are vital for ensuring that individuals have appropriate access rights based on their current roles and responsibilities, as well as for meeting compliance regulations and industry standards. Conducting these reviews through automated software streamlines the process and helps ensure accuracy. For example, analyzing audit trails facilitates the identification of overprivileged accounts.
- Implement strong authentication methods. There are so many ways to compromise a password today that the practice of relying on a single password for access authentication should be completely discouraged. Password authentication should be enhanced with multifactor authentication, which adds an extra layer of security, such as a one-time code. An even more effective approach is passwordless authentication, which incorporates technologies like facial recognition or FIDO keys.
- Automate notifications. Real-time alerts can promptly notify administrators of suspicious activity such as a surge in failed login attempts, facilitating prompt response to unauthorized access attempts and other threats.
Implementing a User Account Management Strategy
Adopting an effective user account management strategy involves the following key actions:
Assess Your Organization’s Needs
The first step in developing a strategy is to assess your organization’s needs. Be sure to:
- Conduct interviews with key stakeholders to understand their specific needs and get feedback from end users to learn about their experience with current account management processes and ask how they can be improved.
- Create an inventory of your existing tools and current processes for user onboarding, offboarding, access requests and password management.
- List all the compliance requirements applicable to your organization that your user account management solution must fulfill.
Select the Right Tools
Assemble a list of candidate solutions and assess the capabilities of each product. The sections above provide details about popular tools and functionality to look for. In addition, make sure that the price fits your budget, being sure to consider not just licensing costs but ongoing costs; for example, solutions that are easier to use will save valuable IT team time. Request that solution vendors present use cases demonstrating the value their offerings have delivered for organizations like yours.
Deploy and Configure the Selected Tool
Once a tool has been purchased, it’s time to proceed with deployment. Begin with a pilot group to test the new system and then implement it in stages. Be sure to apply the principle of least privilege when configuring user role permissions and enable multifactor authentication for administrative access. Implement comprehensive logging for all user account activities and set up alerts for suspicious activities or system anomalies.
Integrate your user account management tool with HR systems to enable automated provisioning and deprovisioning of accounts, and ensure that the integration meets regulatory requirements
Provide Training and Support
To maximize your ROI, develop training to help both administrators and end users use the solution effectively. In addition, be sure to offer helpdesk support during the initial phases of implementation to help users adjust to unfamiliar processes.
Offer periodic training refreshers, monitor system performance, and solicit user feedback to optimize user experiences.
Conclusion
Manual user account management is too resource-intensive and prone to errors to be a viable option for modern organizations. Indeed, the need for automated user provisioning and management has exploded as IT environments have expanded to the cloud. By adopting an automated user account management solution that handles the entire account lifecycle, your business can dramatically improve security, compliance, and user and IT team productivity.

.jpg)
