PowerShell Remoting is enabled in Windows Server 2012 (and later) out-of-the-box, and while many IT shops see this as a potential security risk, PowerShell is in fact one of the most secure ways to administer servers if best practices are followed. In this article, I’m going to show you how to configure Windows Server 2012 R2 to accept remote PowerShell connections from a specific group of users, and how to restrict the cmdlets that can be run.
What Are Constrained Endpoints?
Remote endpoints determine the users that can connect to a device with PowerShell Remoting, as well as what they can do once authenticated. The default PowerShell endpoint allows users that are members of the built-in Administrators and Remote Management Users group to connect remotely and exposes all available cmdlets and functions on the device.
The good news is that you can create your own constrained endpoints and restrict what users can do, allowing you to minimize the risks of allowing PowerShell Remoting for administration purposes.
Create Constrained Endpoints in Windows Server 2012 R2
Let’s create our own constrained endpoint in Windows Server 2012 R2. Log in with local administrator privileges, and click the blue PowerShell icon on the desktop taskbar.
- To see the existing endpoints on the server, type Get-PSSessionConfiguration in the PowerShell prompt and press ENTER.
- In the PowerShell console, you should see the four default endpoints.
To restrict the cmdlets and functions that a user can execute when they connect to the constrained endpoint, we need to create a configuration file. In the PowerShell console, type the cmdlet shown below and press ENTER. New-PSSessionConfigurationFile creates a new configuration file called PrintAdmin.pssc and sets restrictions including limiting remote users to functions that are part of the PrintManagement PowerShell module.
New-PSSessionConfigurationFile – Path PrintAdmin.pssc – SessionType RestrictedRemoteServer -LanguageMode NoLanguage – ExecutionPolicy Restricted – ModulesToImport PrintManagement -VisibleFunctions Get-Printer
NoLanguage restricts users to running just cmdlets and functions, i.e. no script blocks, variables, or operators can be used. The –SessionType value RestrictedRemoteServer limits users to the following proxy functions: Exit-PSSession, Get-Command, Get-FormatData, Get-Help, Measure-Object, Out-Default, and Select-Object. The Restricted value for –ExecutionPolicy parameter also prevents scripts running. Note that there is also a –VisibleCmdlets parameter that can be used if the modules you want to import contain cmdlets.
Now that we have a configuration file, we can register a new endpoint called Helpdesk:
Register-PSSessionConfiguration -Name Helpdesk -Path PrintAdmin.pssc –ShowSecurityDescriptorUI
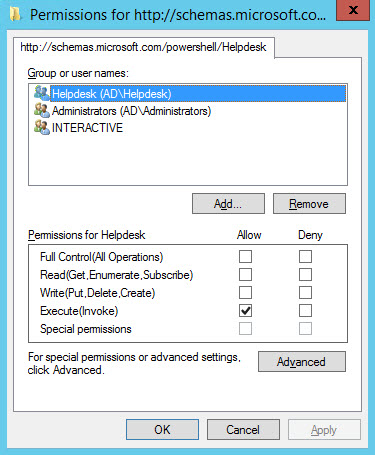
You’ll be prompted to confirm that you want to configure the new endpoint, restart the WinRM service, and configure access permissions to the endpoint. In this example, I’m going to give a group called Helpdesk ‘Execute (Invoke)’ permission on the new endpoint. Don’t forget to give the Helpdesk group permission to manage printers on the remote device, otherwise get-printer will fail.
If you run Get-PSSessionConfiguration again, you will be able to see the new endpoint listed.
Connect to a Constrained Endpoint
Now connect to the endpoint from a remote machine. Log in to Windows 8 with a user that’s a member of the Helpdesk group or the group to which you assigned permissions on the endpoint. Open a PowerShell prompt and run the command below, replacing contososrv1 with the name of the remote server:
Enter-PSSession -ComputerName contososrv1 -ConfigurationName Helpdesk
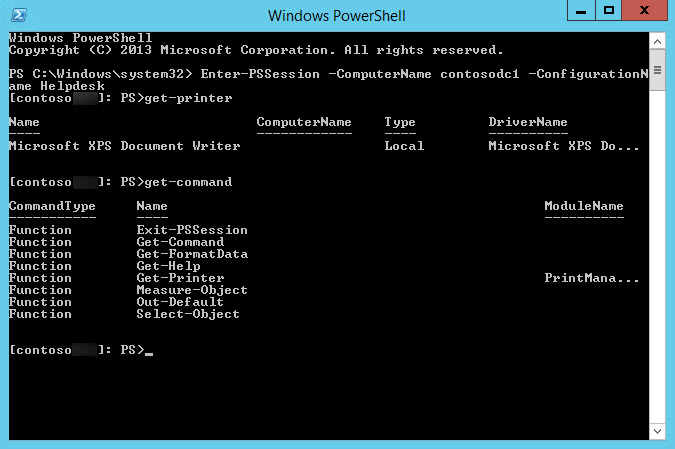
Once connected to the remote server, the prompt will change accordingly to indicate you are working with a remote device. Type get-command and press ENTER, and you’ll see the list of available functions and cmdlets are restricted by the endpoint. In this example, you’re left with the 7 proxy functions allowed by the RestrictedRemoteServer session type and the get-printer function specified in the endpoint configuration file.



