Talking with IT pros, I hear a lot about security issues, and one story is extremely common. The details vary, but at the core is the same threat: privilege account abuse or misuse. In this post, I’ll explain what privilege abuse is, the benefits real companies are realizing by keeping an eye on privileged accounts, and three key things you can do now to start to gain the control you need over privileged users.
What is privilege abuse? Is it really worth worrying about?
Privileged account abuse occurs when the privileges associated with a particular user account are used inappropriately or fraudulently, either maliciously, accidentally or through willful ignorance of policies. According to Verizon’s 2017 Data Breach Investigation Report, abuse of privileged accounts is now the second most common cause of security incidents and the third most common cause of breaches.
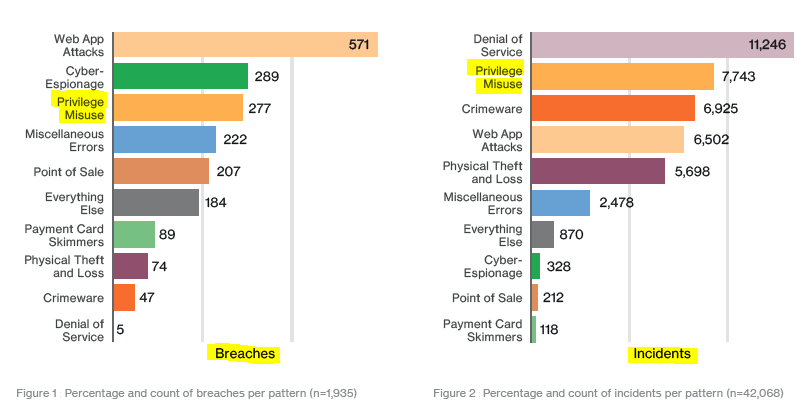
According to the 2017 DBIR, privilege misuse is one of the top causes of both breaches and incidents.
How privilege abuse happens
In a typical scenario, privilege abuse is the direct result of poor access control: Users have more access rights than they need to do their jobs, and the organization fails to properly monitor the activity of privileged accounts and establish appropriate controls.
Access control issues often stem from a lack of coordination between IT management and security teams
These access control issues often stem from a lack of coordination between IT management and security teams. IT is in charge of user accounts, but its main goal is administration. Security teams, meanwhile, are responsible for monitoring privileged accounts to protect the company from insider and outsider threats and ensure compliance with regulatory requirements.
Consequences of privilege abuse
Privileged accounts are a gateway to critical systems and data. Abuse of these powerful accounts can lead to the loss of sensitive data and business intelligence, as well as downtime of systems and applications essential for business operations. In addition to the direct damage to the business, these issues can result in bad publicity and loss of customers and lawsuits that can last for years — as well as compliance failures and their related penalties, which can include both steep fines and imprisonment for top management.
Real-world examples of the value of proper privileged account management
Proper privileged account management is the key to minimizing the risk of privilege abuse. Here are some real cases that illustrate the benefits of privileged account security in different industries and in IT departments both large and small:

1. Protection against any unwanted activity. A government agency stores a variety of personally identifiable information (PII) about citizens. To ensure the security of this sensitive data and comply with regulatory requirements, the IT team carefully performs user activity monitoring and reviews all suspicious actions and other anomalies with other IT staff to determine whether the action was authorized or needs to be investigated further.
2. Protection against third-party violations. A financial company also deals with a lot of sensitive data that must be stored securely to comply with regulations, maintain customer trust and loyalty and ensure ongoing business operations. But monitoring of employee activity is not enough, because vendors also access internal systems to perform maintenance tasks. By automatically video recording all vendor activity, the IT team stays aware of exactly what each account does, so they can quickly spot any misuse of permissions that could endanger sensitive data.
3. Protection against ex-employees or temporary workers. An educational institution has high turnover of staff and students, but HR doesn’t always report these important changes to IT. To prevent security incidents, the IT team continuously apply user activity monitoring across its distributed IT infrastructure, including file manipulations, so they can quickly spot any unwanted activity and respond appropriately. One investigation led to the discovery of two ex-employees who still had access to their accounts and took advantage of it by deleting curriculum files.
4. Protection against low experienced employees. Another educational institution offers students the opportunity to work in the IT department, which requires giving them rights to critical systems to perform specific tasks. But they must not be allowed to read or delete files that contain sensitive information, such as grades and financial data on loans. While students are trusted to make appropriate IT changes, department heads track their activity to verify the changes have been made correctly and that no one accesses anything they shouldn’t.
5. Protection against human mistakes. An energy company uses SQL databases to store extremely important data, such as sensitive customer information and usage data used for billing. Because this data is business-critical, the IT department pays special attention to monitoring all changes to it. One of the routine checks revealed an unauthorized change. Further investigation showed it was made by an employee who gained DBA rights by mistake. By removing those privileges right away, the company reduced the risk of data loss and operational downtime.
6. Protection against overexposure of data. A lottery company stores sensitive information about players and retailers. Employees need different level of access to this data, and as their roles change (for example, due to a promotion or internal transfer), their access permissions must be updated accordingly. To avoid overexposure of sensitive data and minimize the risk of privilege misuse, the company continuously reviews user access rights, access attempts, manipulations with files and other activity in the IT environment.
7. Self-protection in case of a security breach. What if you are the only IT person in your organization? If you follow all security policies and diligently perform your duties, then you can never be accused of privilege misuse, right? Well, no. There might be a situation when you need to prove that you did your best and a breach is not your fault. Proper privileged account management will be your savior. As one IT administrator put it, “I’m the only person managing IT in our company. I keep track of my own activities not only for compliance reasons, but to save my hide as well. If anything happens, nobody can accuse me of doing something wrong. There is proof.”
Three steps for reducing the risk of privileged account abuse
Is it possible to prevent all privilege abuse? No. Some insiders will misuse their privileges, either accidentally or maliciously, and your privileged accounts will always be a top target of outside attackers who want to take advantage of their powerful permissions. However, you can minimize these risks. Here are three key steps to get started:

Step #1. Continuously assess and properly manage assigned privileges
Ask your friends whether they have ever accessed information they shouldn’t have seen. I’m sure you’ll find that many of them have. This happens because privilege assignment is often seen as a one-time task, which it shouldn’t be. Instead, on a regular basis, you make sure to:
- Review access rights and remove excessive permissions in accordance with the least-privilege principle.
- Review and update permissions whenever a user’s role in the organization changes.
- Make sure your sensitive data is not overexposed by verifying that access to it is granted based strictly on a specific need.
- Pay special attention to your privileged accounts — who can use them and what permissions they grant.
Step #2. Gain visibility into your IT environment
Would you know if there was a suspiciously high number of failed attempts to access a critical file or database, or an unauthorized modification to your security groups? If not, this step is especially important to you. Without a thorough monitoring of all changes and user activity in the IT environment, it is impossible to detect threats, including privilege abuse, in their early stage.
Step #3. Analyze user behavior
It’s one thing to collect data. It’s totally another to get meaningful insights out of it. Can you tell when your users exercise their privileges outside of normal working hours? Do you know whether their current behavior deviates from the norm? User behavior analysis will show you anomalies that are not always obvious if you just look at event logs.
* Extra tip
Pay special attention to privileged accounts that are shared by multiple users. These accounts are here to stay because they are convenient, but beware of the top two security issues associated with them: lack of individual accountability and lack of proper password management. Try to find the right balance between facilitating administration and ensuring robust security.
Please use the comment section to share your stories of privileged account misuse and your tips on how to mitigate the risk!
Want to know more about privilege abuse issue? Then check these four notorious data breaches caused by privileged account abuse.



