If you do a Google search for products and services that can help your company be more secure, your Web browser might very well explode. The sheer number of results you’ll get — solutions promising everything from a hack-proof network to a cure for major diseases — will likely leave you overwhelmed, frustrated and confused. However, what you may not realize is that many fundamental layers of security are cheap or free, and they can significantly reduce your organization’s security risks in a short amount of time.
In this blog post, I’ll share some of these data and network security fundamentals and help you get started implementing them.
Ask yourself, “What do we need to protect?”
When I sit down with a new client, this is one of the first questions I ask. I want to get the organization thinking about what they truly care about the most. If my question is met with blank looks, I ask it another way: “If a reporter called you tomorrow morning and said an attacker stole ‘X’ from your network and posted it on the internet, what would that be?” The “X” is often sensitive data, such as credit card information, protected health records, trade secrets, sensitive financial information or other business-critical information. Once they have identified their crown jewels, we will then start a discussion about how to build appropriate security layers around them.
Adopt a proven standard
One of the best ways to create a solid security program is to follow a standard. There are many to pick from, such as the NIST Cybersecurity Framework and the International Standards Organization (ISO). Personally, I really like the Center for Internet Security’s Top 20. As much as I think we should get away from thinking about security as a checklist, the CIS controls provide a great prioritized list of actions your organization should take to better protect yourself against threats. The list includes some security “hand washing” basics, such as installing antivirus software and controlling network access. But it also covers more advanced controls, like deploying an intrusion detection/prevention system, creating a secure configuration for mobile devices, and implementing data loss prevention (DLP).
Know what’s on your network
The #1 control in the CIS list is Inventory and Control of Hardware Assets. It calls for you to track devices on your network so that authorized devices can access network resources but any unauthorized access is blocked. After all, if you don’t know what’s connected to your network, you can’t protect it. Free tools like nmap can help discover the devices on your network. For example, on a Linux system you can do the following:
- Download an nmap style sheet with git clone at https://github.com/honze-net/nmap-bootstrap-xsl.git /opt/nmap-bootstrap-xsl/
- Scan your network with nmap -sS -T4 -A -oA MyCompany –stylesheet /opt/nmap-bootstrap-xsl/nmap-bootstrap.xsl 192.168.55.0/24 (replace 168.55.0/24 with your network subnet).
- Create a pretty HTML version of the scan’s output using xsltproc -o MyCompany.html /opt/nmap-bootstrap-xsl/nmap-bootstrap.xsl MyCompany.xml.
Once these steps are completed, you’ll have a nice starter inventory with the devices discovered on your private networks:
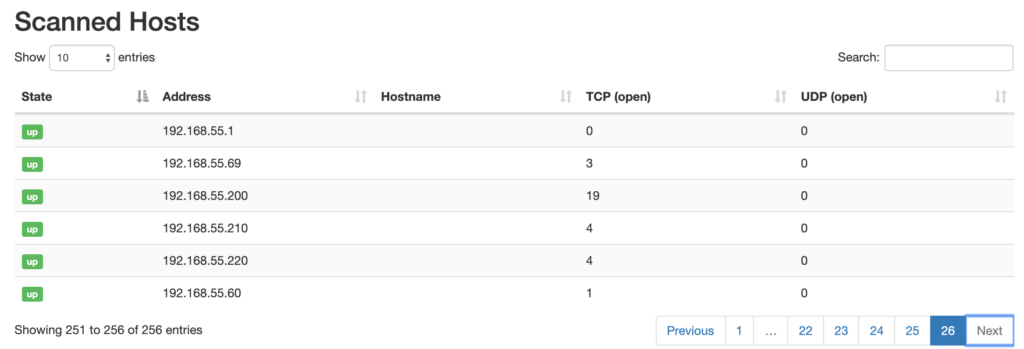
Additionally, you can look at each individual host and see the details about any running services:
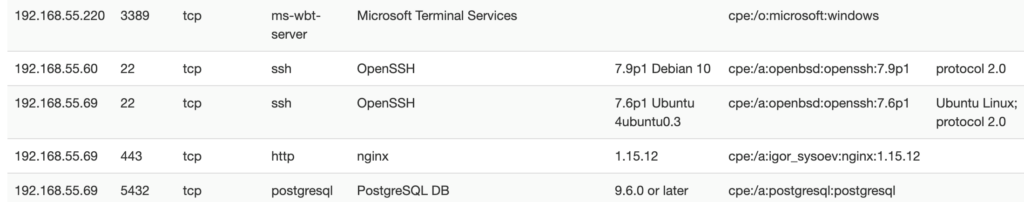
Outlaw common passwords
CIS control #16 is Account Monitoring and Control, and a critical part of it is controlling passwords on user accounts. If you’re running Active Directory, you can prevent your users from picking over 500 million bad passwords by implementing Troy Hunt’s Pwned Passwords list, which can be done easily (and for free!) using this GitHub project. There are also commercial tools, such as SafePass.me, that make it easy to keep common passwords out of circulation.
Deploy two-factor authentication
Too often, passwords are our only defense against malicious people accessing legitimate accounts. By adding two-factor authentication (2FA), we force users to prove who they are by providing not only something they know (a password) but also something they have (such as a text message) or something they are (such as a fingerprint).
In other words, if someone figures out my PayPal account password and attempts to log in to the website and drain my funds, they’ll be stopped in their tracks because they won’t know the code that PayPal sent to my phone (unless the attacker has my phone too, in which case I’ve got bigger problems).
Most popular sites and services offer two-factor authentication. To check if the services you use offer 2FA, take a look at https://twofactorauth.org. If you find that a service you use does not offer 2FA, you’re given the option to send the site a friendly tweet or Facebook message saying “We’d like it if you supported two-factor auth.”
Train your users continuously
When it comes to security, I don’t think it’s possible to over-train your users. They are the human firewall for your company, and you need them to thwart any social engineering threats that come in through emails, calls and even your front door. Don’t just push a YouTube video at them once a year and call it “yearly security awareness training.” Trickle security information to them continuously through newsletters, email tips, and lunch and learn sessions. Also, your internal staff doesn’t always need to be the mouthpiece for security gospel. Bring in outside consultants once in a while to change things up a bit.
One company I worked with created giant posters with security tips and hung them on the inside of the bathroom stall walls. I laughed at first, but soon heard feedback from employees saying that the posters were effective. If you think about it, the bathroom is one place everybody is sure to see those security tips!
Log everything
When you find yourself responding to an attack or security breach (notice I said when, not if), one of the most important things you can have is a log of the important events on your systems. Often, logs are gathered through a commercial security information and event management (SIEM) solution, which can be effective but also pricy. If you’re not logging anything today and don’t have a large budget for this type of technology, Netwrix Free Community Edition is a great free way to get started. It delivers information about changes and access control events on a wide range of systems and applications. Logging Made Easy is another free kit that, as its name implies, makes it quick and easy to start logging activity on your Windows endpoints. It provides step-by-step instructions, scripts and Group Policy objects to make the install a snap. I had it up and running in my lab in just a few hours.
Patch your systems promptly
To gain a foothold on your network, one easy win attackers look for is computer systems that are missing critical patches. If a Microsoft Windows system hasn’t had the MS17-010 update applied, for example, hackers can fully compromise it in seconds. I’m still surprised at how many companies have not applied this critical patch. If you don’t have a well-managed patching routine, consider outsourcing the work to a managed service provider.
Remove local administrator rights
If your users are local administrators on their machines, they can do anything they want to the system. While this configuration might cut down on the number of help desk calls you receive, it also makes the machines much more vulnerable to viruses, malware and other attacks. Migrating users to a non-administrator configuration will take some time, and you might need to work with your software vendors to iron out a few kinks, but I’d argue the network security trade-off is worth it. To put it in perspective, a team of security researchers found that removing local administrator rights would mitigate 81% of all critical vulnerabilities Microsoft patched in 2019.
Remember that security is a journey
As you can see, there are many security layers you can wrap around your internal network that cost little to no money. Start slowly with free tools and focus on implementing a few controls at a time, using the CIS Controls as your guide. As your program matures and your security policies evolve, you can graduate into using commercial tools to improve your security posture even further.



