The year 2020 has shown us that cloud computing is among the most powerful capabilities humanity has, enabling people around the globe continue their everyday business and education uninterrupted. We continue gathering the most interesting findings from industry research. If you’re interested in learning statistics on cloud usage, top cloud initiatives and cloud security concerns, read the 2020 State of the Cloud Security Statistics article.
In this article, we reveal how companies are dealing with cloud adoption, and how they can avoid one of the most critical challenges: cloud service misconfigurations.
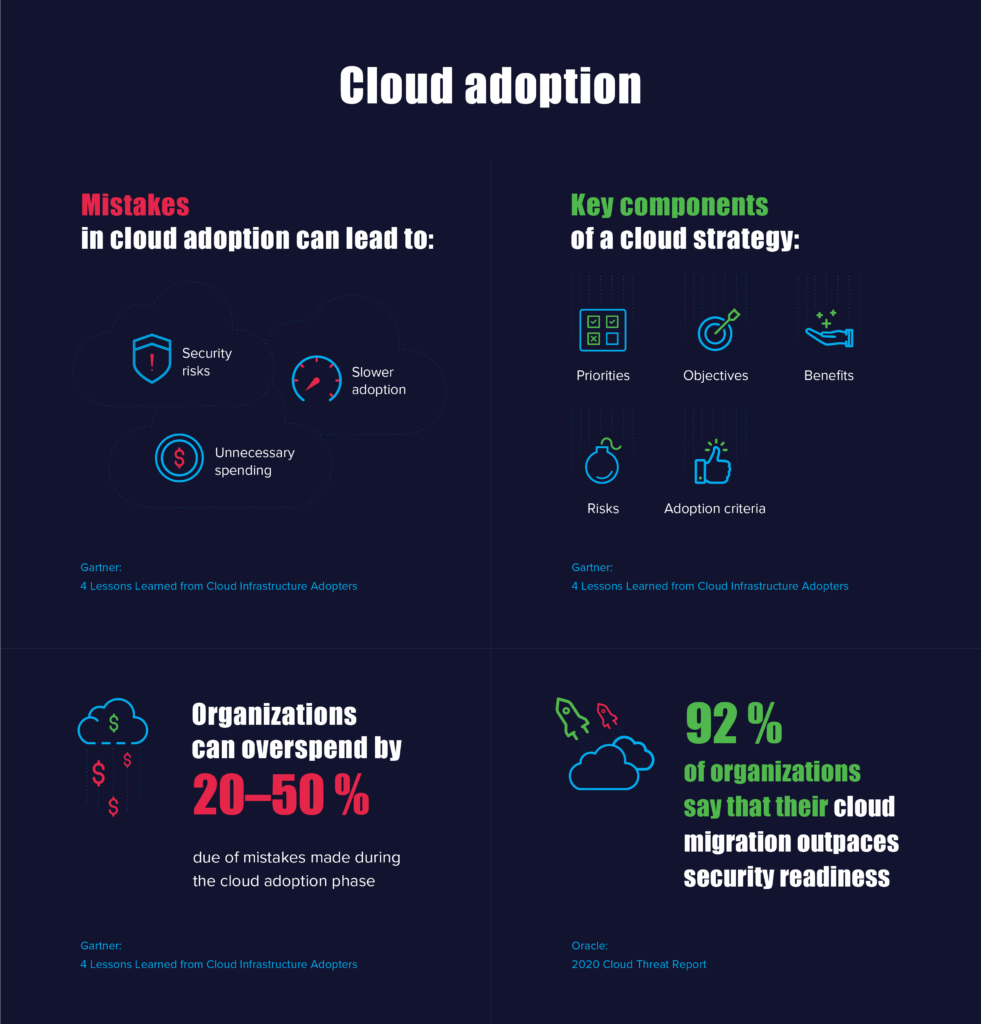
Cloud adoption
If you are beginning to embrace the cloud, it’s important to plan your cloud adoption carefully, for multiple reasons. First, Gartner warns that, through 2024, most companies that are unaware of the mistakes they make in cloud adoption will overspend by 20 to 50%. Another critical factor is cloud security risks, which often arise when cloud migration outpaces security readiness. Unfortunately, the Oracle Cloud Threat Report shows that 92% of companies admit having a security readiness gap.
To overcome these and other cloud adoption challenges, develop guidelines to define the cloud strategy for your entire company. The document should explain priorities, objectives, benefits, risks and adoption criteria. Then, it’s important to align your cloud strategy with your cybersecurity efforts.
As you conduct your planning, it is crucial to remember that cloud and on-premises applications and infrastructures require different sets of security policies and processes. In fact, 82% of organizations say that traditional security solutions either don’t work at all or only provide limited functions in cloud environments (2020 Cloud Security Report, Cybersecurity Insiders).
To build an appropriate cloud defense, it’s important to shift away from a perimeter security mindset, as there’s no such thing as a perimeter in the cloud. Focus on data protection instead. Start with data discovery and classification to know which of your data is sensitive and where it resides, so you can determine whether it can be stored in the cloud and ensure that it is accessible only by authorized users. Knowing exactly what data needs protection will help you set priorities and apply different security controls based on classification results. Implement robust data access controls, including identity and authorization management; enforce cloud data encryption for data uploaded to the cloud; and monitor your cloud to identify activity patterns and potential vulnerabilities.
Misconfigured cloud services
Many companies that proceed to cloud adoption too quickly, before they have a well-defined strategy, end up with configuration issues. What’s worse, McAfee reports that about 99% of misconfigurations go unnoticed, which leaves them exposed to the risk of costly data loss and data theft.
To mitigate cloud misconfigurations, companies need to leverage security automation to address policy infringements or security issues.
Consider having solutions that automate the following:
- Configuration auditing — Define a baseline for secure configuration and regularly check your current cloud configuration against that baseline.
- Entitlement reviews — Review permissions to your cloud resources on a regular basis and strictly limit access based on the need-to-know for each employee to enforce the least-privilege principle.
- Change auditing — Monitor changes made to configurations across the cloud environment.
- Strong authentication — Use methods like multi-factor authentication (MFA) to reduce the risk of unauthorized access to your applications, systems and data.
- Data access monitoring — Spot unauthorized access to your sensitive data.
- Data discovery and classification — Scan data repositories for sensitive data and configure these repositories with the strongest security measures in mind.
- Data encryption — Apply this additional barrier to further protect data from unauthorized access.

 of ENG [Free Trial] short-840x350.jpg)


