Who is HAFNIUM?
In early March, Microsoft reported a large, coordinated attack that exploited critical vulnerabilities in Exchange Server 2010, 2013, 2016 and 2019 in an attempt to exfiltrate credentials and other sensitive information from organizations’ mailboxes. Microsoft attributed this attack to a sophisticated Chinese group code-named HAFNIUM. The first detected attempts date back to January 2021. Since then, additional actors have begun to use the vulnerabilities to conduct similar attacks on a massive scale across a wide range of sectors, including infectious disease research organizations, law firms, higher education institutions, defense contractors, policy think tanks and NGOs.
How do the attacks work?
The Exchange Server vulnerabilities allow adversaries to deploy a web shell (a form of remotely accessible backdoor) running as the highly privileged SYSTEM user. With these backdoors in place, attackers can run commands on the system even after the vulnerabilities have been patched, enabling them to compromise data and credentials or even deploy ransomware or other malware.
What’s the best way to update Exchange Server?
We highly recommend that you read Microsoft’s blog post about the attack and download and apply the latest cumulative update as soon as possible.
If you can’t do that at this time, we advise you to run this one-click mitigation tool from Microsoft to temporarily protect against currently known attacks that exploit the Exchange Server vulnerabilities.
How can you determine whether your Exchange servers were compromised?
Microsoft is maintaining a list of indicators of compromise (IOCs) and investigation steps in their blog, under the heading “Can I determine if I have been compromised by this activity?” It is essential to use this information to make a complete assessment of your Exchange Server. If you find signs of operational backdoors, we strongly suggest that you engage an incident response firm to assess the extent of the compromise and the potential exposure of other assets.
If you’re running Netwrix Auditor for Exchange, you can also easily check for suspicious export of mailbox data and other unusual activity on your Exchange servers, which can also be a sign that they have been compromised.
Step 1: Check whether any mailbox data has been exported.
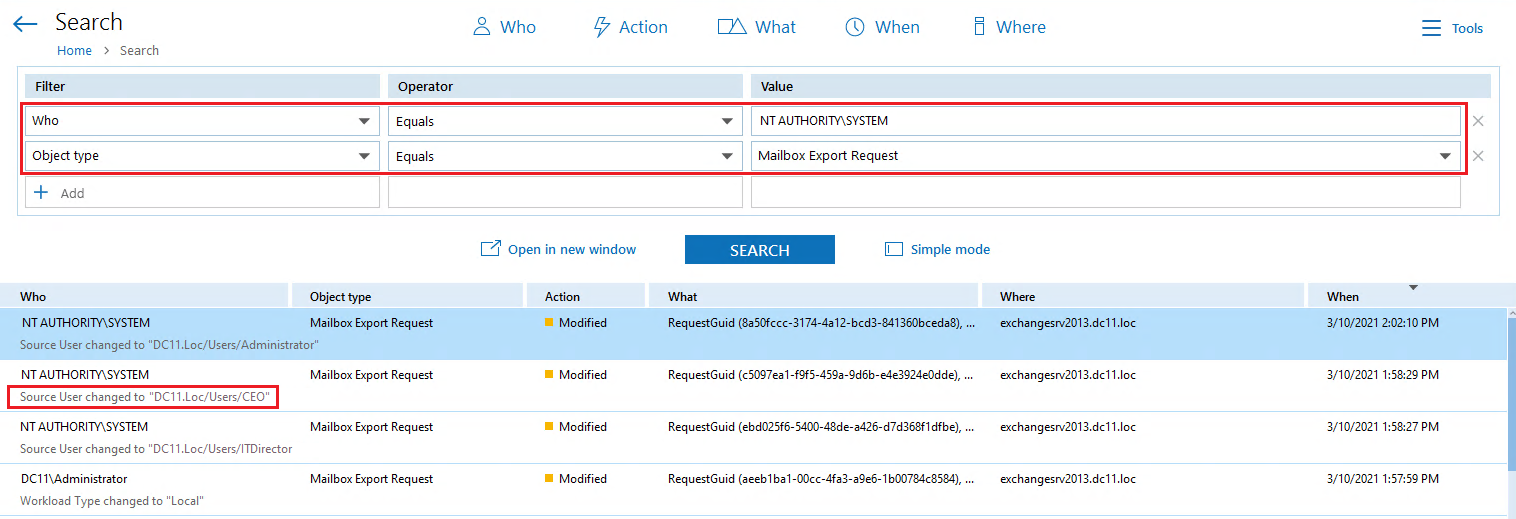
Perform an Interactive Search using the following filters:
- “Who” filter equal to “NT AUTHORITYSYSTEM”
- “Object Type” filter equal to “Mailbox Export Request”
Any mailbox export request by NT AUTHORITYSYSTEM is suspicious and worth investigating. Hopefully, what you see looks nothing like the screenshot below, which shows that several important mailboxes, including the CEO’s mailbox, have been exported.
Step 2: Check for other suspicious activity on your Exchange Server.
HAFNIUM attacks are not limited to stealing mailbox data — once the attackers are in, they can do whatever they want on your Exchange Server, including compromising other credentials to move laterally in your environment. Therefore, it’s a good idea to review all activity by the SYSTEM account starting from January 2021.
Simply execute a new Interactive Search with the following filters:
- “Who” filter equal to “NT AUTHORITYSYSTEM”
- “Data Source” filter equal to “Exchange”
- “When” filter set to “Date Range” of “January 1” to “Today”
Look for any usual activity that could indicate compromise or sabotage, including changes to mailbox delegations and permissions, modification to role groups, non-owner mailbox access events, mailbox deletions, or Exchange database changes. Promptly investigate any suspicious events.
What else can you do to protect your organization?
It’s a good idea to set up alerts around mailbox export requests and other suspicious Exchange Server activity. Remember, even once you’ve installed the latest Exchange Server updates, attackers can still use any backdoors they created before the update.
Any time you’re performing a search in Netwrix Auditor, you can create an alert based on that search in just two clicks:
- Open the “Tools” menu.
- Click “Create Alert”.
Final recommendations
Keep in mind that the threat is still evolving — additional adversaries are actively abusing unpatched servers to steal data and propagate ransomware. Therefore, it’s essential for you remain on guard for any suspicious activity around your Exchange Server.