Every organization faces data security threats, which become more complex when integrating technologies like cloud computing or hybrid working options. That’s why it is critical to implement robust data protection to safeguard critical assets such as intellectual property, personally identifiable information, and sensitive financial data. This challenge is further augmented by the growing number of regulations imposed by governmental and industry bodies.
Establishing a comprehensive, layered defense strategy is the optimal approach to help prevent data leaks and minimize the risk of data loss. This involves reducing your attack surface, monitoring for suspicious activities and insider threats that might result in data breaches, and devising an effective response plan. Such a strategy ensures the best protection for your organization’s valuable data assets.
Data loss prevention (DLP) is a crucial component of any practical, strategy-based approach to data security. In this article, you’ll understand what DLP is, its significance, the various types of data loss prevention methods available, and how to select the best approach tailored to your organization’s needs.
What is DLP?
DLP, or Data Loss Prevention, encompasses information security practices specifically tailored to prevent the exfiltration of sensitive and critical data from leaving corporate computers, network, and cloud or on-prem servers. . This is accomplished by identifying sensitive information and deploying appropriate risk-based controls, all while minimally impacting business operations. DLP is not a single software solution but a comprehensive strategy that is crucial to an overall data protection program. Its primary focus is prevention, ensuring robust and proactive protection of sensitive corporate data.
If you’re just getting started with data loss prevention, remember that data governance should oftentimes be combined with DLP as part of the overall strategy. Adequate data loss prevention requires knowing what critical data you store and having policies and rules in place.
Why is DLP important?
In today’s rapidly evolving threat landscape, Data Loss Prevention (DLP) has become crucial due to the significant rise in data breaches. According to the IBM Cost of a Data Breach Report 2023, 70% of all data breach incidents occur via the endpoint. A robust DLP program helps organizations protect sensitive data from unauthorized access and leaks, forming a vital defense against breaches that often target confidential information. By effectively implementing DLP strategies, organizations are better equipped to safeguard their critical data, ensuring data integrity and maintaining the continuity of their operations. Furthermore, a breach of intellectual property can result in an immediate and adverse effect on the business, highlighting the necessity of a comprehensive DLP approach.
When can a DLP Solution help?
Data Loss Prevention (DLP) solutions provide organizations with enhanced visibility and blocking capabilities into the location, usage, and movement of sensitive data. This visibility helps organizations identify and protect sensitive data such as personal identification, financial, intellectual property, and other confidential information from unauthorized access or data loss. It also offers different benefits, including:
- Reduces the risk of data breaches by monitoring, protecting, and blocking sensitive data from being shared inappropriately.
- Helps ensure regulatory compliance concerning personal information protection with required data protection regulations like GDPR, HIPAA, and PCI-DSS. However, these standards have requirements that cannot be addressed by DLP alone, such as minimizing access entitlements and tracking user activity, including access to systems and data usage.
- Detect and prevent accidental or intentional data exfiltration attempts by insiders. However, DLPs don’t do entitlement reviews, log user activity around sensitive data unless it violates policy, or help you assess the scope of data in a breach.
- Assist data breach investigations with forensic event data as well as full copies of the files that were attempted to be exfiltrated in order to understand the nature and scope of the incident.
By implementing a DLP solution, organizations can significantly bolster their data security, ensure compliance with legal and regulatory requirements, and mitigate the risks associated with data breaches.
Components of a Data Loss Solution
A Data Loss Prevention (DLP) system comprises essential components for safeguarding sensitive data. These include data identification through content inspection, policy creation and management for defining handling protocols, continuous data monitoring, and incident detection with alert generation. The system also features data filtering and blocking capabilities, and encryption tools for secure data management. Centralized management consoles for policy and incident oversight and machine learning algorithms enhance the system’s ability to adapt and respond to evolving data security challenges.
How does DLP work?
DLP works by using a combination of technologies and processes to identify, monitor, and protect sensitive data across an organization. There are three primary tasks involved:
- Analyze, understand and classify content: A fundamental step in data loss prevention is thoroughly understanding your data, and if there were to be a breach, knowing what exit points that data could be breached on. It is also helpful to know whether the data is stored on computers, on-premises or in the cloud. it is also helpful to employ automated data discovery and classification technologies. These tools scan your data repositories and apply digital signatures to tag critical, sensitive, or regulated data. This tagging process helps identify various types of content, such as medical records, financial data, or intellectual property. With accurate classification in place, you can use DLP strategies to safeguard data based on its significance and relevance to the organization.
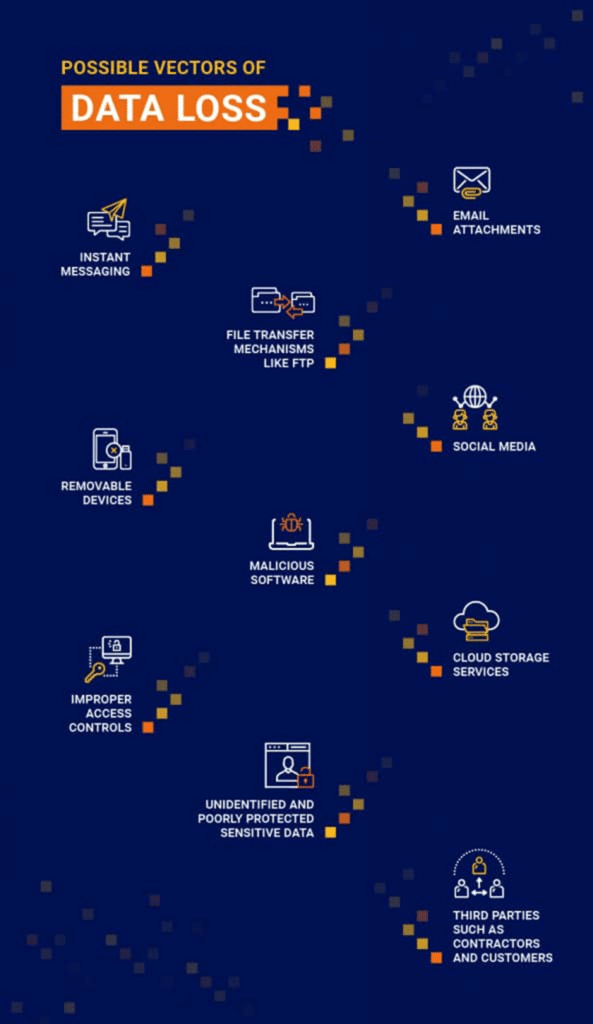
- Understanding the context. Enterprise data can be at rest, or in motion., and each state involves different exfiltration vectors for data loss. DLP Software-based solutions and other Data loss prevention technologies help mitigate these risks by analyzing the context of each action or event. This includes analyzing who copies the data and the specific machine involved in the process. By understanding the context, DLP solutions can more effectively identify and address potential data loss scenarios across different data states within the enterprise.
- Policy Comparison and Action: This step is integral to DLP solutions that operate based on established business rules, policies, and conditions. These solutions detect inappropriate or malicious activities like copying sensitive data onto removable media contrary to corporate guidelines. DLP policies clearly define the responses triggered when specific conditions are met. These responses can range from allowing or prohibiting the activity, suspending the involved account, to alerting the security administrator about the incident. This ensures that actions align with the organization’s data security protocols without impacting the productivity of your employees.
Different Types of Data Loss Prevention
Today’s market offers various data loss prevention (DLP) solutions, each tailored to address specific aspects of data security. These include:
- Network data loss prevention. Prevents data from leaving the network, such as network shares and networked computers. Network DLP ten years ago was fairly common as many company computers and data repositories didn’t leave the network, but now with mobile laptops and work from home and hybrid environments, many industries find that network DLP is less necessary, and can be better suited by using a combination of endpoint DLP and cloud based DLP. Some industries still rely heavily on network DLP based on regulations or business strategy, but this is diminishing.
- Endpoint data loss prevention. This DLP prevention type safeguards data at the individual computer level, so it’s not dependent on the corporate network. Endpoint DLP can prevent any sensitive data from leaving company computers, scanning for sensitive data at rest on computers, and taking company-wide remediation actions if it is being stored or mishandled. Any organization that has company owned computers that have any interaction with senstive data needs to have endpoint DLP. Even if company policy prohibits storing sensitive data on the employee computers, an endpoint DLP is still required to enforce these policies and prevent the computers from acting as a passtthrough to move data from a server to outside of the organization.
- Cloud DLP: Safeguards data stored and processed in cloud environments by ensuring compliance and protecting against data breaches.
- Email DLP: Monitors and controls email communications to prevent the accidental or malicious sending of sensitive information.
DLP Policy Rollout Best Practices
The DLP adoption process should be meticulously strategized and thoughtfully executed. For optimal outcomes, follow these best practices:
- Conduct a thorough assessment of the data that needs to be protected beforehand to understand where your sensitive data resides, how it moves, and who has access to it.
- Define clear and concise policies that align with regulatory compliance requirements and business objectives.
- Involve all stakeholders in the policy creation process, including IT, legal, HR, and the affected business units, to ensure policies are practical and enforceable.
- Use a phased-in approach, starting with a pilot group to test the policy’s effectiveness and fine-tune it before a full-scale rollout.
- Educate employees about the DLP policy and why it is important for the organization’s security.
- Continue to monitor the policy’s effectiveness after its implementation and make necessary adjustments. Regularly update the policy to adapt to new threats, technologies, and business changes.
By following these best practices, organizations can ensure that their DLP policies are effective and enforceable and contribute to the overall data protection strategy.
How Netwrix Can Help
In today’s interconnected world, safeguarding critical data has become paramount for organizations of all sizes. Implementing a robust Data Loss Prevention (DLP) strategy is imperative with the proliferation of data breaches and unauthorized data sharing. Netwrix Endpoint DLP solutions offer comprehensive features designed to address the evolving threats modern businesses face.
Netwrix Endpoint DLP solutions enable you to prevent unintentional data loss across various channels, including email, removable storage, cloud uploads, and instant messaging, itunes, powershell, airdrop, printing, etc. By effectively identifying and blocking attempts to exfiltrate sensitive data, organizations can protect against both insider threats and malicious actors.
Moreover, Netwrix Endpoint DLP enables organizations to enforce data protection policies in compliance with industry regulations such as GDPR, HIPAA,NIST, and PCI DSS. With features like content inspection, intellectual property protection, and device control, Netwrix Endpoint Protector ensures granular control over data transfers while simplifying deployment and management processes.
In conclusion, a layered approach is essential, while no single DLP tool can address all data security challenges. Organizations can optimize their DLP strategy and allocate resources effectively by evaluating existing tools in alignment with business requirements. With Netwrix DLP solutions, organizations can fortify their defenses against data breaches and mitigate risks effectively.
FAQ
What is data loss prevention (DLP)?
Data loss prevention (DLP) refers to tools and processes that protect critical information from being exfiltrated or stolen by anyone without proper permissions. DLP controls help reduce the risk of data leakage, loss, and exfiltration by ensuring that sensitive information is identified and risk-appropriate controls are deployed, ideally with minimal impact on business processes.
Why is DLP important?
Data loss can result in various repercussions for the organization, including lawsuits from the people whose data was exposed, penalties from regulatory agencies, and damage to your business reputation and bottom line. DLP controls help you analyze data and activities and prevent the movement and use of data outside of defined boundaries. DLP also enables you to enforce security policies, meet compliance standards, and gain better visibility into data across various systems.
What techniques are commonly used for DLP?
Strategies often used for DLP include:
- Network data loss prevention secures network communications using to control information flow and protect data from leaving the corporate network
- Endpoint data loss prevention protects data exfiltration on workstations, laptops, and other endpoint devices
- Data identification involves locating sensitive or critical data based on predefined categories.
- Data leak detection monitors user behavior for activity that could indicate a data leak, usually by establishing a baseline of regular activity and looking for unusual actions.
- Protecting data in motion means ensuring that data moving along a network does not get routed to unauthorized recipients or end up in an insecure storage area.
- Protecting data at rest involves scanning data in corporate assets like databases, servers, computers, and mobile devices.
- Protecting data in use refers to controlling the sensitive data that is generated or inn use by a user, prior to them moving it off of a company asset.
What does DLP protect?
DLP guards sensitive or critical information in three states: in motion, at rest, and in use. Many DLP tools have prebuilt libraries of hundreds of well-known data types, such as personally identifiable information (PII), financial data, and data regulated by mandates like HIPAA and GDPR.
What is a DLP strategy?
A DLP strategy details how the organization will watch for security threats and potential data breaches or loss. It should include an overview of the solutions implemented and the types of information to be protected. To prevent data leaks, it’s important to classify your data, identify your risks, put the proper practices in place to protect data, increase security awareness among all users, enable fast incident detection, and create and regularly test a recovery plan.
What does a DLP tool do?
A DLP tool is part of an overall strategy to keep sensitive data from getting stolen, misused, or improperly accessed. DLP tools inspect content to identify sensitive and regulated data and monitor and analyze how that data is being accessed and used. Suppose the DLP tool spots unusual actions for a given user or is not permitted by the organization’s security policy. In that case, it takes the steps defined by administrators, such as automatically blocking access and notifying the appropriate team.



