Past years have been too crowded with cybersecurity events. A lot of financial, health care, government and social media data were compromised. Systems failed and services were disrupted. TV shows were leaked online before the official release. Last of all, there were ransomware crusades. Every week, there is a new adversary: a state, an individual or an international group of hackers. It seems impossible to find anybody who has not been directly affected by any of the IT threats, or at least at risk. Some businesses received publicity they definitely wished they would not get.
But what dominates the press and what bothers IT pros on a daily basis are not necessarily the same thing. For this reason, every year, we conduct a survey to identify what IT risks organizations and IT departments face during their everyday work. These risks are usually related to cybersecurity, operations and regulatory compliance. We are interested to learn more about the processes and widely used practices, as well as IT pros’ perceptions of the greatest IT threats and how well they are ready to beat cybersecurity risks.
This year, we received feedback from 723 IT pros from various industries and countries. We asked them about the information security threats they face every day and analyzed the results.
What Is the Current State of Cybersecurity?
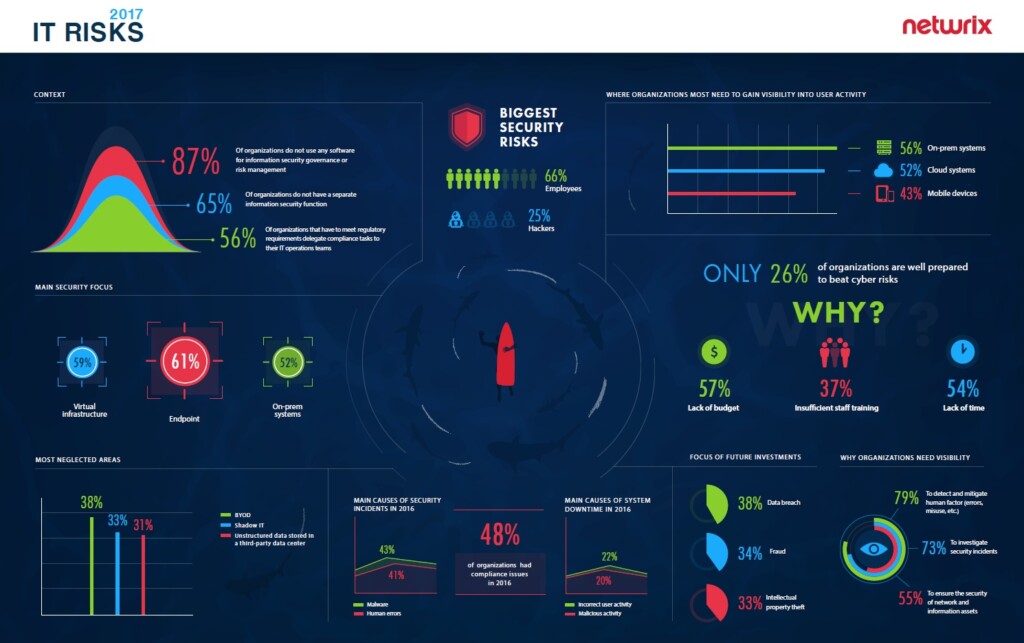
65% of organizations don’t have a dedicated person or department responsible for cybersecurity
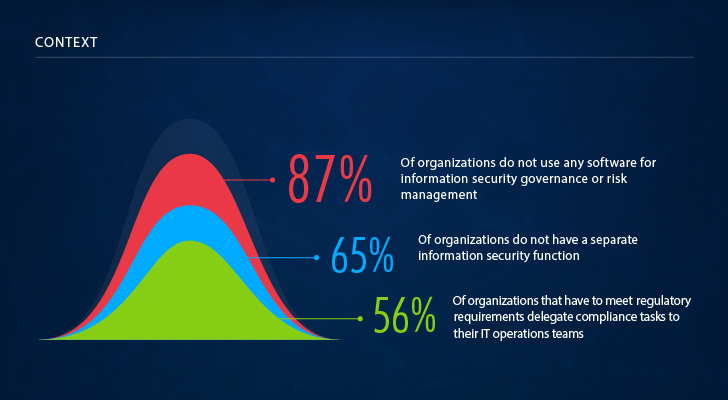
First, let’s take a look at the context within which the surveyed IT departments operate and deal with cyber risks. The absolute majority of respondents said that they use some security software, but only 13% of respondents use advanced solutions for information security governance and risk management. Also, we got confirmation of what our customers tell us: More than half of organizations lumber their IT departments with all kinds of IT-related tasks. These include not only stable operations of IT systems and business user support but also cybersecurity, reporting and compliance.
Where Are Cybersecurity Risks Hiding?
31% of IT pros don’t have any idea what is happening to the data stored in third-party data centers

Now we will go a little deeper and find out how much our respondents know about what is happening in their IT infrastructure. Here we see that not all areas of IT are created to be equally loved. Organizations tend to have pretty good visibility into endpoint, virtual infrastructure and on-premises systems, with more than half of organizations being fully aware of what is happening there. At the same time, they still struggle to control BYOD policies and shadow IT (two of the typically most difficult areas), as well as – surprisingly – unstructured data stored in third-party data centers.
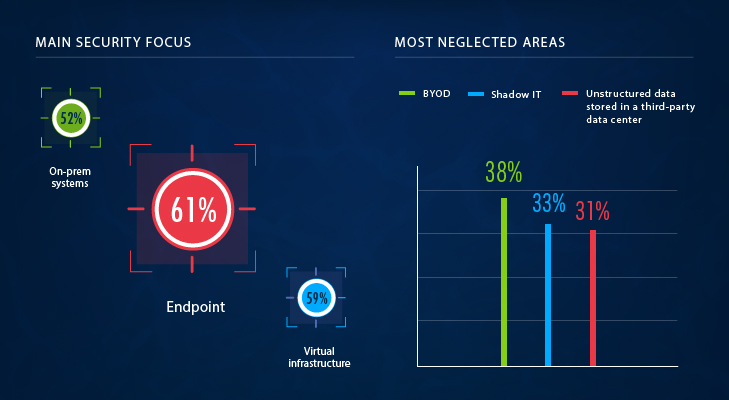
One third of organizations don’t know what is happening with their data in third-party data centers at all, and only a quarter of respondents said they have complete visibility into it. Startling, isn’t it? How about the rest of the corporate data? Things are not much better for the unstructured data stored on premises: Only 32% of respondents have complete visibility into user activity around it. Respondents mostly have visibility into activity in databases (and 52% of them stated that visibility is complete). To sum up, visibility into unstructured data, regardless of its location, leaves much to be desired; visibility into the databases is better, but only for half of respondents, which is still far from perfect.
Where Does Visibility Matter the Most?
75% of IT pros see those who have legitimate access to the internal systems as the greatest threat to IT security
With that said, the question remains: Where is visibility critical and where is it not? Respondents indicated that visibility is the most critical for on-premises systems, cloud systems and mobile devices. Visibility into data takes the last place in this rating. With all the breaches we hear about, it’s startling, that visibility directly into activity around data and data access for the majority of organizations is less significant than visibility into systems and devices.
If organizations are more preoccupied with the perimeter defense, does it mean they see hackers as the main threat for cybersecurity? Yeah, well, no. According to our respondents, the greatest cyber security threat comes from those who have legitimate access to the internal systems: employees (66%), vendors, contractors, partners and other third parties (9%). Only a quarter of all surveyed IT pros indicated hackers as the main threat.
Where Are the Biggest Information Security Threats Coming From?
Is the statement that employees represent the biggest risk only a perception or actually the fact? Let’s look at the real incidents that happened in 2016. The main causes of security incidents were malware and human errors. In the case of malware, as we know, it is often unintentionally launched by employees when they click on links they should not. Only about 8% of companies said they experienced external intrusions or unauthorized access. The main reason for operational issues in 2016, such as system downtime, was improper or malicious activity. All of these findings lead us to conclude that organizations mostly have security and operational issues due to lack of visibility into user activity.
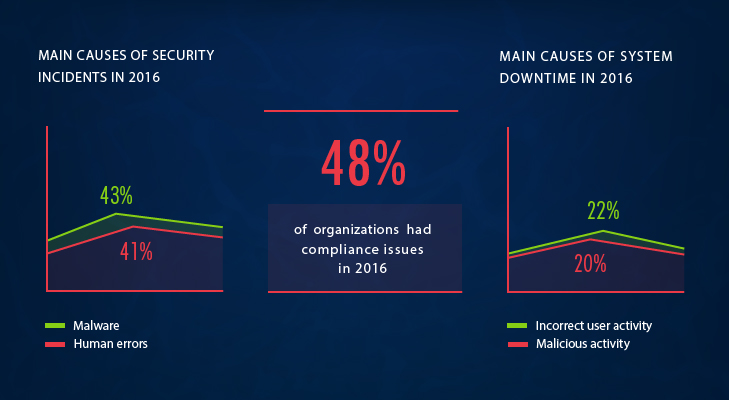
Speaking of visibility into what users are up to, it is also required for compliance reasons. Half of the companies that have to comply with regulations experienced problems with passing audits. The majority of the issues were attributed to the inability to provide a complete audit trail of user activity around sensitive data as evidence of compliance.
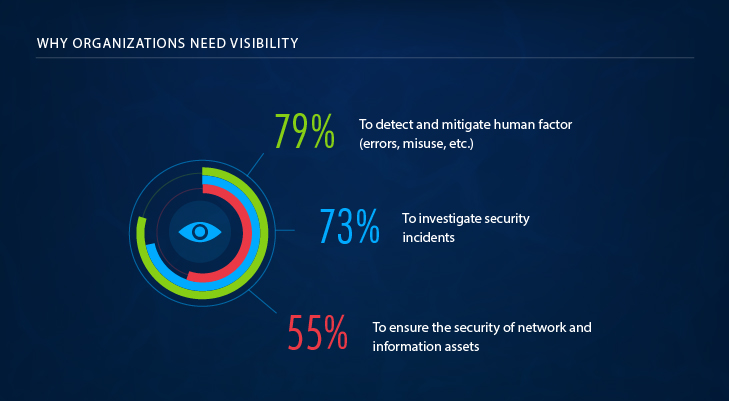
With so many issues caused by the lack of visibility, what do organizations say about the actual value of infrastructure transparency? The absolute majority of them claimed it helps to detect and mitigate the human factor, which includes both unintentional actions and errors and malicious misuse. Another two of the most cited values are efficient investigations of security incidents and maintaining the overall security of the IT environment.
Even though there are a lot of positive tendencies in gaining visibility and fighting cyber security risks compared to the data we received last year, still only about a quarter of respondents claimed their organizations are well prepared to beat cyber risks.
What Are the Main Obstacles on Your Way to Information Security?
38% of IT pros plan to invest in protection against data breach

The most common reasons others are not so sure about their ability to combat information security threats are lack of budget and time and insufficient staff training, or, in other words, the notorious human factor.

So, what are organizations planning to do next? Most of them have built a more or less successful perimeter defense and realize that people with excessive privileges may do more harm (again, intentionally or inadvertently) to sensitive data or business continuity than an adversary from the outside. Also, prevention of each and every possible threat is not at all possible, even with the unlimited resources. With all that in mind, IT pros place securing data among their most important goals on the agenda. About a third of respondents were absolutely ready to invest in protection against data breach, intellectual property theft and fraud.
In general, as I mentioned earlier, tendencies this year are positive, and we see a lot of improvements in how organizations prepare themselves to handle cyber security risks. Despite the obstacles, unsolved issues, ever more rigorous compliance requirements for cybersecurity and so on, organizations have been taking a more integrated approach to dealing with cyber risks and protecting valuable assets.
View the full 2017 IT Risks infographics:
Click on the image above to open a high resolution version in a new tab
Interested in learning about other findings of this survey? Please read the full 2017 IT Risks Report.