This post is the first one in the series dedicated to the in-depth discussion of the findings of our Netwrix 2017 IT Risks Report. While the report presents the summarized survey results of 2017 and compares them with the 2016 findings, further, we are reviewing the most interesting findings, focusing on different industries, company sizes, and regions.
Overall, 723 IT pros from organizations around the globe provided their feedback for the report. Almost a third of them come from large enterprises with 1,000 or more employees, and another two thirds from small and medium businesses.
Cybersecurity Context in SMBs and Enterprises
We were interested to see to what degree large organizations and small and medium businesses (SMBs) are exposed to cyber risks, whether or not the risks they face are different, and what they do to strengthen the security of their critical assets against IT threats in the future. Large organizations typically have more resources and larger budgets than SMBs, enabling them to better prepare themselves for any cyber threat Let’s see what the findings reveal.
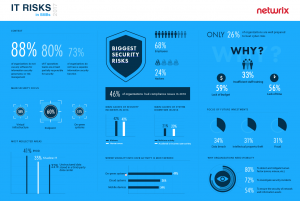
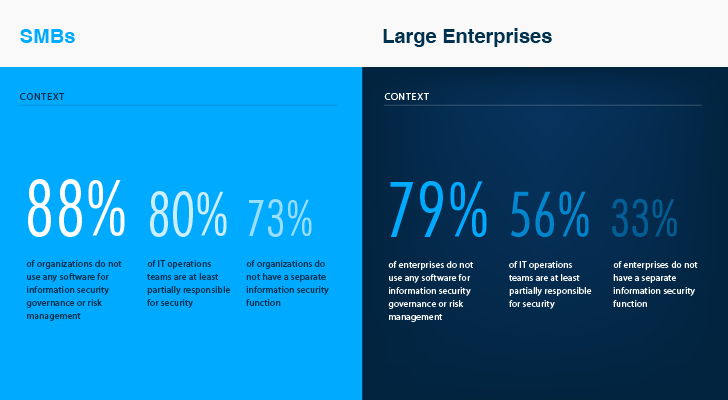
Only one third of enterprises do not have a separate information security function (33%), and IT operations teams are responsible for security in more than half of large businesses (56%). Both of these numbers are much higher among SMB respondents (73% and 80%, respectively). One would expect that just as enterprises are likely to hire more IT staff than SMBs, they would also have deployed advanced security solutions to help IT personnel better do their job. Here is where we got it wrong. The absolute majority of large businesses (79% vs. 88% of SMBs) do not even use any software for information security governance or risk management.
Focus of Security Initiatives in SMBs and Enterprises
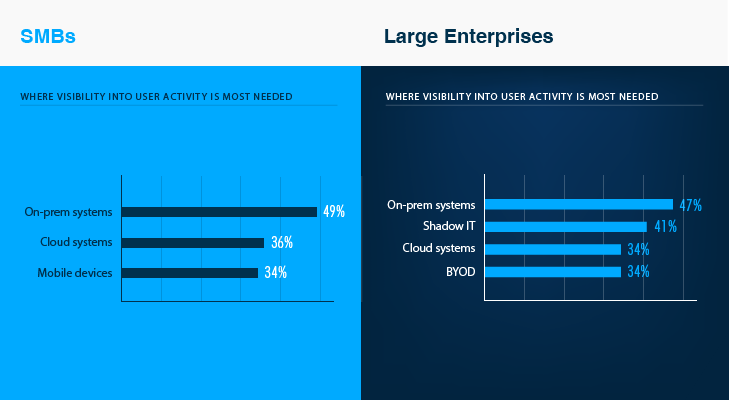
In what areas of the IT infrastructure do enterprises succeed when it comes to security? Overall, about two thirds of enterprises claim they are very well aware of user activity and IT changes in the corporate databases, virtual infrastructures, and endpoints. Here, I would like to point out the very important aspect that distinguishes enterprises from SMBs: While the majority of enterprises have deeper visibility into what is happening with their structured data (65%), SMBs seem to be more adept at perimeter defense.
65% of enterprises prioritize security of data, while 60% of SMBs are primarily focused on endpoint protection
In terms of the less successful areas, a little over one quarter of enterprises admitted being unable to control users’ personal devices and unauthorized installations. BYOD and shadow IT are the areas with which organizations of all sizes tend to have the majority of problems. However, only large enterprises see them as a high risk to security. While SMBs are mostly concerned with corporate systems and devices, enterprises have more or less succeeded in these areas and have taken the next step. For more details, see the full infographic below.
It is interesting, though: Why do organizations struggle to gain control over manipulations with unstructured data stored in a third-party data center (another most neglected area) just as much as they try to tame BYOD and shadow IT? Is it due to the insufficient visibility provided by data centers? Or because data stored there is not sensitive enough and its security is not worth the effort? If you have any ideas you would like to share, please leave a comment in the comments section below.
Who is the Biggest Threat to Cybersecurity?
Back to our survey results, regardless of the level of data sensitivity, only 13% of enterprises and 8% of SMBs see third parties with legitimate access to data/systems as the main threat to security. If we look at the incident data provided by our respondents, we will notice that about half of enterprises and a quarter of SMBs speak from personal experience.
Meanwhile, employees are perceived as the number one threat by the majority of both SMBs and enterprises, despite the fact that malicious intent is often absent This finding is confirmed by some incident statistics. First, about 72% of enterprises and 59% of SMBs had security issues in 2016 due to human errors, malware, or both. Employees’ accidental or incorrect actions were also the reason 28% of enterprises and 20% of SMBs experienced system downtime in 2016. A quarter of respondents noted that outages happened too often or lasted for too long, which inevitably impacted business operations.
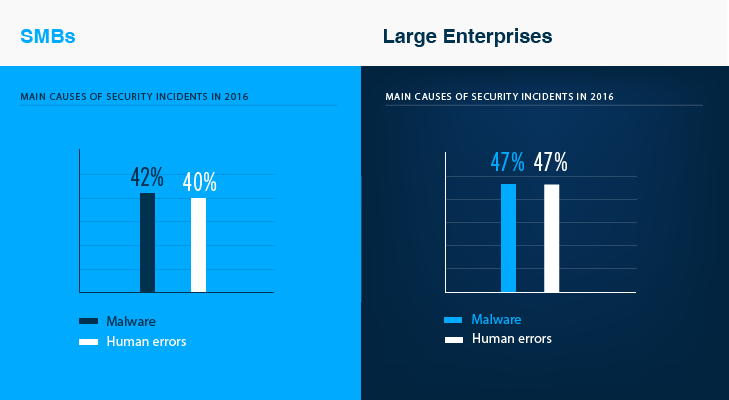
It is only when it comes to compliance-related risks that the human factor doesn’t play a significant role. Inadequate automation and unsatisfactory IT auditing processes led to the fact that 59% of enterprises and 46% of SMBs that have to comply with regulatory standards had problems during IT audits or could not pass them on the first try. The most common causes of compliance issues were inability to provide complete evidence of compliance, inability to provide relevant evidence within a reasonable time frame, or problems with converting requested information into a suitable format for reporting.
Are SMBs and Enterprises Ready to Handle Cybersecurity Risks?
With that said, only 25% of enterprises and 26% of SMBs claimed to be well prepared to face and combat cyber risks.
Only 25% of large enterprises and 26% of SMBs are well prepared to beat cyber risks
Just like SMBs, enterprises also complained about lack of budget and insufficient staff training. However, besides that, enterprises are preoccupied with the growing complexity of the IT infrastructures that aggravates the challenge of detecting, investigating, and mitigating various IT risks.
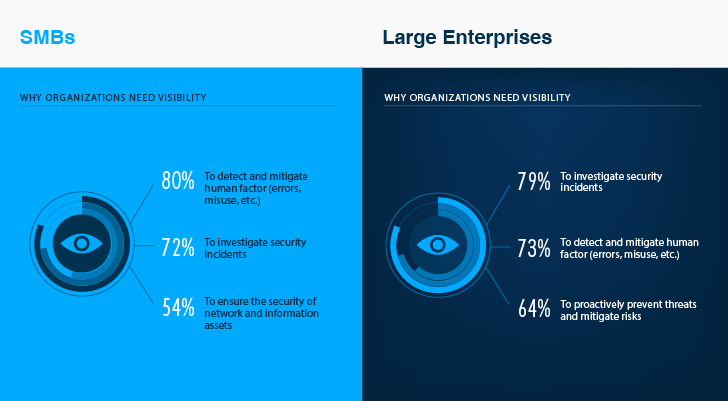
Why Visibility into User Activity Matters
64% of enterprises leverage visibility to proactively mitigate IT risks
Organizations that have good visibility into user activity across their critical IT assets claim that it helps them detect and investigate suspicious activity in order to mitigate the risks of cyberattacks in the early stages. Enterprises find visibility to be critical in building a proactive security strategy that minimizes the risk of unauthorized activity from the inside or outside.
The Focus of Future Investments for SMBs and Enterprises
To sum up all the past and present issues, successes, and mistakes of our respondents, we could not miss the chance to ask them about their future security plans. Both enterprises and SMBs put data security first. About 72% of enterprises and 41% of SMBs are willing to invest in solutions designed specifically for data protection against breach, theft, or fraud.
How SMBs Can Get Enterprise-Level Security
As we can see, organizations of various sizes often face common problems. However, small companies can take the best from enterprises’ experience and improve their security posture by adopting these practices:
- Focus on what’s important, not just the perimeter. Both enterprises and SMBs see their own employees as the biggest threat to the security of data and systems, regardless of whether or not their intent is malicious. However, the survey data shows that SMBs choose to focus on perimeter security more, while enterprises put priority on data security. SMBs should determine what assets or systems are critical to their business and focus on monitoring user activity there.
- Try to shift from the reactive to the proactive mode. This is another thing to learn from enterprises. While they, just like SMBs, strive for more efficient detection and investigation of security incidents, they also go a step further and look for ways to learn what the risky areas are. You should clearly understand what data you have, how important it is for the company, who has access to what files, and if they need it or if you can limit their privileges and therefore lower risk of data exposure.
- Dedicate at least one employee to focus on security. In the majority of small companies, the IT team is responsible for nearly everything connected with computers. IT pros have to ensure continuous operation, patch the system, support users, repair hardware, develop security policies and make sure everyone is following them, educate other employees, deal with compliance auditors, perform backup regularly, fight against ransomware and viruses, and much more. However, remember that being buried in routine and trying to address each and every possible IT issue with no skills to handle IT security, the IT operations team (usually two or three people) will inevitably fail at a certain point. Such failure can come at high cost, so the risk may justify the extra investments necessary to hire a security guy.
View the full infographics (click on the image to open a high resolution version in a new tab):
IT Risks in SMBs
IT Risks in Large Enterprises

Interested in learning more about other findings from this survey? Please read the full Netwrix 2017 IT Risks Report.