Netwrix conducted its 2017 IT Risks Survey to learn more about the security, compliance and operational issues that bother organizations worldwide. We asked IT pros from over 30 industries about their thoughts on the adequacy of existing IT security controls, the biggest IT risks they face every day and their readiness to beat these risks.
As part of the survey, we’ve extracted some pretty interesting findings about the healthcare industry based on the feedback provided by IT specialists working for medical organizations around the globe. We aimed to look deeper into IT security practices, successful experiences and plans of healthcare organizations, as well as the most typical pain points.
Our key questions were: which security, compliance and operational issues bothered healthcare organizations in 2016, and how well were they prepared to protect their assets against cyber threats?
Who is responsible for security?
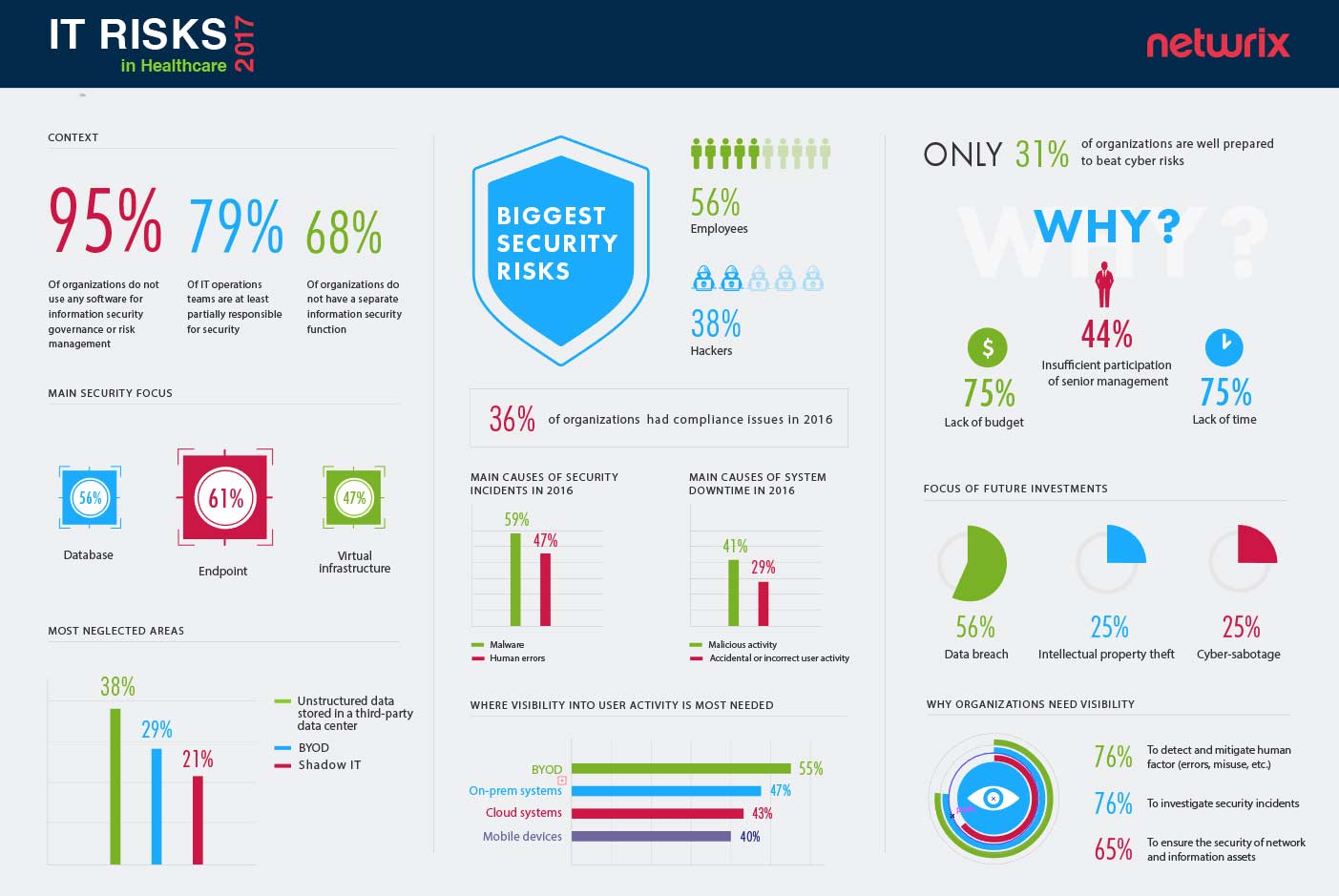
95% of healthcare organizations do not use any software for security governance or risk management
Let’s take a look at the resources that healthcare organizations have in their IT ecosystems to handle issues related to security and compliance. These resources may be divided into two groups: human resources and solutions that provide security governance and risk management. This section reveals an interesting finding: the absolute majority of organizations do not use any software for security governance or risk management. There may be two possible explanations for this: organizations either haven’t faced any threats yet, think of security as a “set and forget” thing, which does not require more investment, or they simply do not have enough financial resources.
In accordance with the overall 2017 IT Risks Survey results, over half of the organizations do not have a separate cybersecurity function, which means the responsibility for security-related tasks will most likely fall on the IT operations teams. Although this approach can be successful in certain conditions, it has some serious shortcomings. Being responsible for everything puts pressure on IT operations teams and may cause them to overlook critical changes indicating security violations or even cyber-attacks.
Which areas must be protected?
Healthcare providers focus mostly on endpoint security (61%) and security of databases (56%)
If we look a bit deeper into how organizations prioritize certain areas of security, we will see that companies focus most of their attention on endpoint security and security of databases. While the first finding is rather typical for different industries, the focus on database security may be considered a healthcare industry-specific feature.
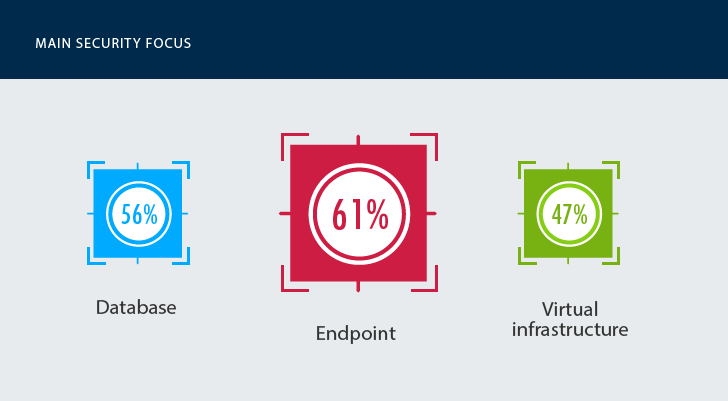
Despite being strict, compliance standards like HIPAA do not cover database protection directly. Reading “between the lines” makes it clear that database protection should be in place for a reason. Most compliance regulations stand for the safety and security of Protected Health Information (PHI). Healthcare organizations store massive amounts of sensitive consumer and patient data and need to make sure that data stored on premises (e.g. Social Security numbers, medical records, healthcare plans and other) are protected.
Which systems are most neglected?
Not all systems, however, are equally “cherished” by medical organizations. The results show that the healthcare sector (similar to other industries) have low visibility into data stored in third-party data centers—this generally includes documents, reports, paper forms, emails, test results and any other data that is either not captured or poorly captured in a structured format. Although less sensitive than data stored on premises, their records, just like every electronic health record, may be critical for assessing clinical risks and must be stored securely. Further, since many organizations have chosen hybrid cloud options for cost reduction, a lack of control over these records may become a problem for both security and compliance in the long run.
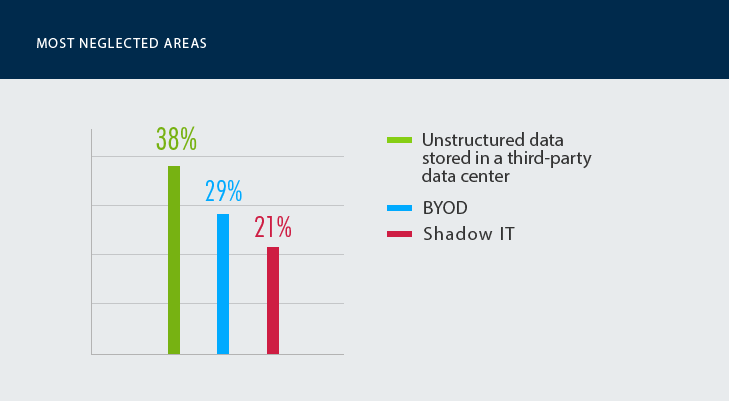
Another neglected area is BYOD—a peculiar result—as over half of the respondents say that lack of visibility into BYOD poses a threat for their security posture. This is quite predictable, as the growing use of electronic health records (EHR) and personal devices in daily activities does not only make the medical workforce more mobile and efficient but also increases its potential security risks.
What are the most typical cyber threat patterns?
56% of healthcare organizations think that their employees pose bigger threats to security than anyone else
In light of the headline-making data breaches, which hit the healthcare sector in the last few years, the logical question is: who do healthcare organizations perceive as the biggest threat to their data and system security? Over half of the healthcare organizations perceive their employees (56%) to be bigger threats to their data and systems than hackers from the outside (38%).
These results are no surprise if we take a look at the most typical incidents that have happened to healthcare organizations during 2016. Overall, 59% of healthcare organizations had to deal with malware, which is often spread through social engineering attacks and penetrates organizations’ networks mainly due to employees’ negligence. The second most common cause of security incidents was human error, which encompasses accidental disclosure of sensitive data, loss of critical information stored on mobile devices and other scenarios. As for the system downtime, the main causes of system outages were malicious activities (41%) and accidental or incorrect user activity (29%).
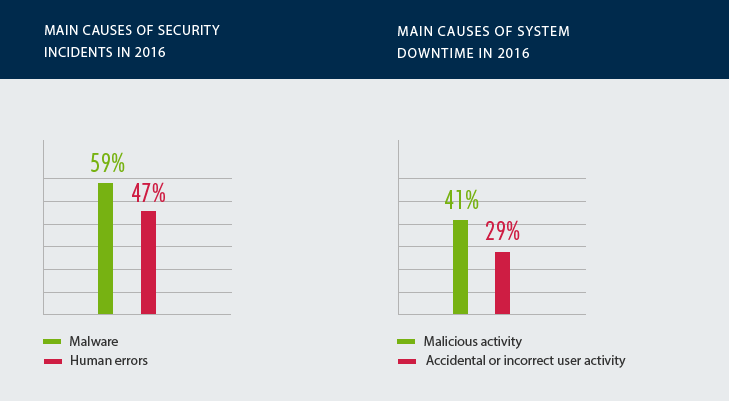
These results confirm the findings of other industry reports like the Verizon 2017 DBIR and indicate that insider threats (regardless of intent) pose serious risks to healthcare organizations, while lack of understanding of user activity can also result in security incidents.
What are the issues with compliance?
36% of healthcare organizations had difficulties with passing compliance audits
Medical organizations have to deal not only with the threats from the inside, but also with pressure from government and legal bodies. They have to comply with a wide range of industry standards to ensure that basic security controls are in place and sufficient. Unfortunately, the survey results demonstrate that organizations’ readiness to meet compliance requirements leaves much to be desired, as 36% of organizations had compliance issues or experienced problems with passing audits. Interestingly, for many healthcare organizations, the main problem is not the inability to provide a complete audit trail of user activity (which, according to HIPAA requirements, they always do), but rather the inability to retrieve relevant evidence in time.
Are they ready to beat cybersecurity risks?
Only 31% of healthcare organizations think they are prepared to beat cyber risks
As healthcare tops the list of industries that are the most vulnerable to cyber threats, the ability to protect sensitive data and withstand sophisticated attacks become critical. Unfortunately, the research showed that only 31% of respondents claim their organizations are well prepared to fight cyber risks, which may vary from common privilege misuse to more sophisticated forms like ransomware.
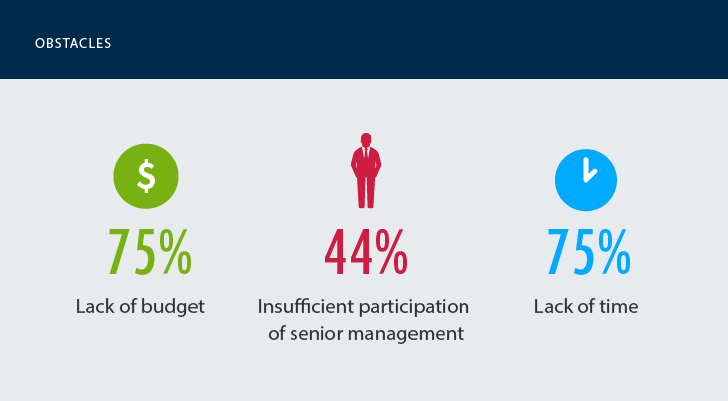
Among the main obstacles to combat cybersecurity is the lack of time and budget. Not a big surprise, as year after year IT pros complain about limited resources for security and data protection. As senior management is not always willing to make security a top priority, healthcare organizations often have to make do with what they have making it extremely difficult for them to ensure network and information asset security and as well as keep the system up and running smoothly.
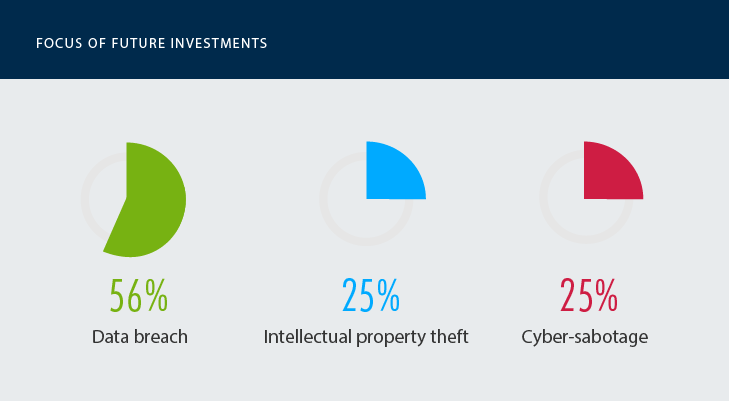
56% of healthcare organizations plan to invest in cybersecurity to prevent data breaches
In case senior management considers the importance of allocating more budgets to cybersecurity, there are certain areas where healthcare providers are more likely to invest. Quite expectedly, the examples of large-scale security incidents like Anthem and Premera Blue Cross, as well as strict compliance regulations, stimulate healthcare organizations to allocate sufficient budgets to solutions and services that would help them better prevent data breaches.
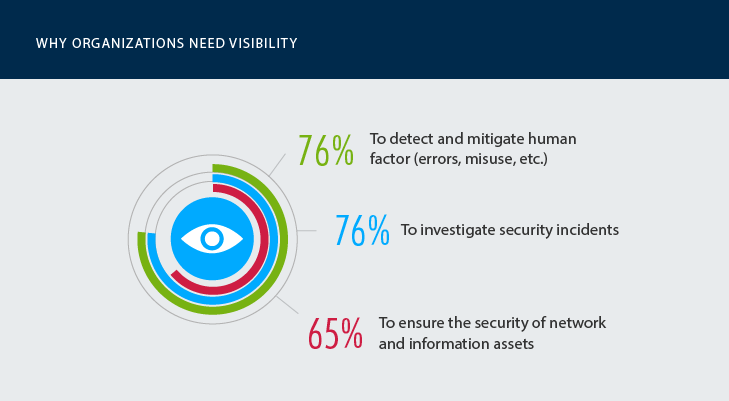
Why is visibility into activity so critical for cybersecurity?
Despite a long list of software providers that offer products for IT security, there are technologies that have proven themselves to be the best for data breach protection, namely those that help identify security vulnerabilities, analyze user behavior, identify threat patterns and assess potential risks. All these solutions have one thing in common: they help organizations gain pervasive visibility into what’s going on in their IT environments and helps them to establish better control over systems and data.
The need for deep visibility appears to be extremely high: healthcare organizations stated that they require better awareness of their IT environment’s activity to detect and mitigate early-stage insider threats, investigate security incidents faster and protect networks against breaches. The systems where visibility into critical changes and user activities are absolutely critical for security posture include cloud-based systems, on-prem systems and BYOD.
The results of the 2017 IT Risks Report found several inconsistencies in the healthcare organizations’ attitudes towards security. On one hand, organizations realize the necessity of data protection and control over their complex IT environments. On the other hand, many of them still fail to implement basic cybersecurity controls and experience difficulties in passing compliance audits. Despite following the requirements of HIPAA and other compliance standards, medical organizations are likely to focus on certain areas of IT environment instead of having visibility across all critical systems, which increases their vulnerability to cyber threats.
That being said, human factor was one of the main causes of security incidents in 201. The majority of respondents are likely to focus on protecting their endpoints and critical databases against insiders’ misuse; this refers to every type of aberrant behavior that may put data at risk from malicious activity to human error. Finally, most organizations perceive visibility as being a critical measure in protecting patient data against cyber threats, and, despite all the difficulties, they are ready to invest in data protection and take more proactive approaches to security.
View the full infographics:
Click on the image above to open a high resolution version in a new tab
Interested in learning about other findings of this survey? Please read the full 2017 IT Risks Report.
We encourage you to share your opinion!