With attacks getting increasingly frequent and sophisticated, the traditional approach to shielding your IT ecosystem is no longer working. You can’t simply tie hands of “bad guys” and give full privileges to “good guys” because you can’t know which users you can actually trust. For example, employees you think are “good” can become malicious insiders given the right motivation, and stolen credentials enable attackers to masquerade as “good guys.”
We can’t know what tactics attackers will dream up next. Moreover,
Evolving digital business needs and opportunities (adoption of cloud, mobile ecosystems, etc.) also come with new risks
Therefore, we need to shift our mindset away from yes/no approaches that simply cannot move at the same pace as security threats. We must rethink our security skill sets and build an adaptive security architecture enriched with advanced analytics that brings cybersecurity to a completely new level. From my takeaways, the Gartner Security and Risk Management Summit this year addressed this very issue, identifying four important trends that we’ll cover in this series of blog posts.
Trend #1. Understanding CARTA Approach
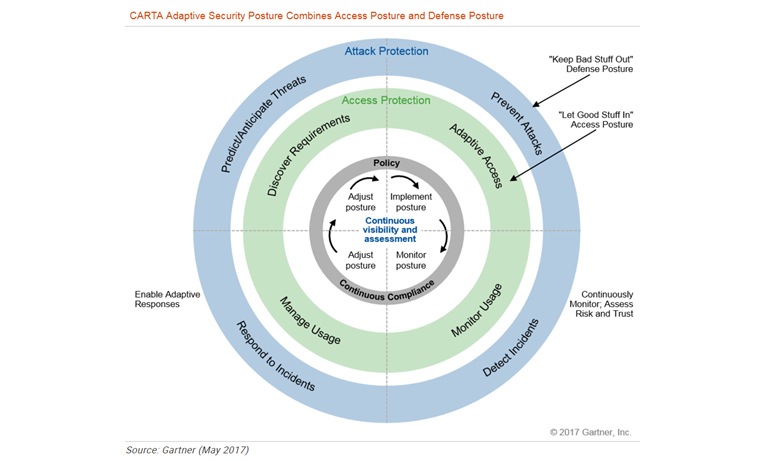
Let’s begin by exploring the continuous adaptive risk and trust assessment (CARTA) approach to security.
Gartner’s CARTA represents a critical strategy for forward-thinking CIOs and CISOs. With digital trust as a key concept, CARTA enables you to recognize the changing risk landscape and place only the trust appropriate at a given time in your employees and entities. Security is not a set-it-and-forget-it thing; it’s a process that has to be always reviewed and adjusted based on ongoing real-time assessments of risk and trust.
To see how, let’s walk through how information security decisions are made in most IT environments these days. Suppose a user is trying to access a folder with sensitive PII. First, there will be a series of validation questions to determine whether this user should be allowed to access this folder, and if so, what actions the user can perform with the folder. These decisions will all be based on the “let good stuff in and keep bad stuff out” policy that you have already fine-tuned.
What if the user — someone you’ve always trusted — has turned into a rogue insider and is about to compromise your data? Or a hacker has stolen the user’s credentials?
Here CARTA comes into play. A CARTA approach goes beyond yes/no questions and assesses risk and trust related to both the user and the entity (in our case, a folder), at the exact point in time when the decision has to be made — all based on continuous top-to-bottom visibility. For example, perhaps the user is logging in from an unusual location or at an unusual time, which might be reason to raise a red flag right now. These context-adaptive, real-time answers help you make better decisions about what access to grant to a specific user to particular data at a given time based on user history and other contextual factors. While you are still trying to sort out “good guys” from “bad guys,” a CARTA approach balances risk and trust, minimizing the risk of a “good guys gone bad” situation.
To implement a CARTA approach, you need a complete picture of roles and privileges in your IT environment and be able to assess how a user behaved before he or she tried to access specific data. User and entity behavior analytics (UEBA) capabilities will help you with this.
Trend #2. Detecting Insider Threats and External Hackers with UEBA
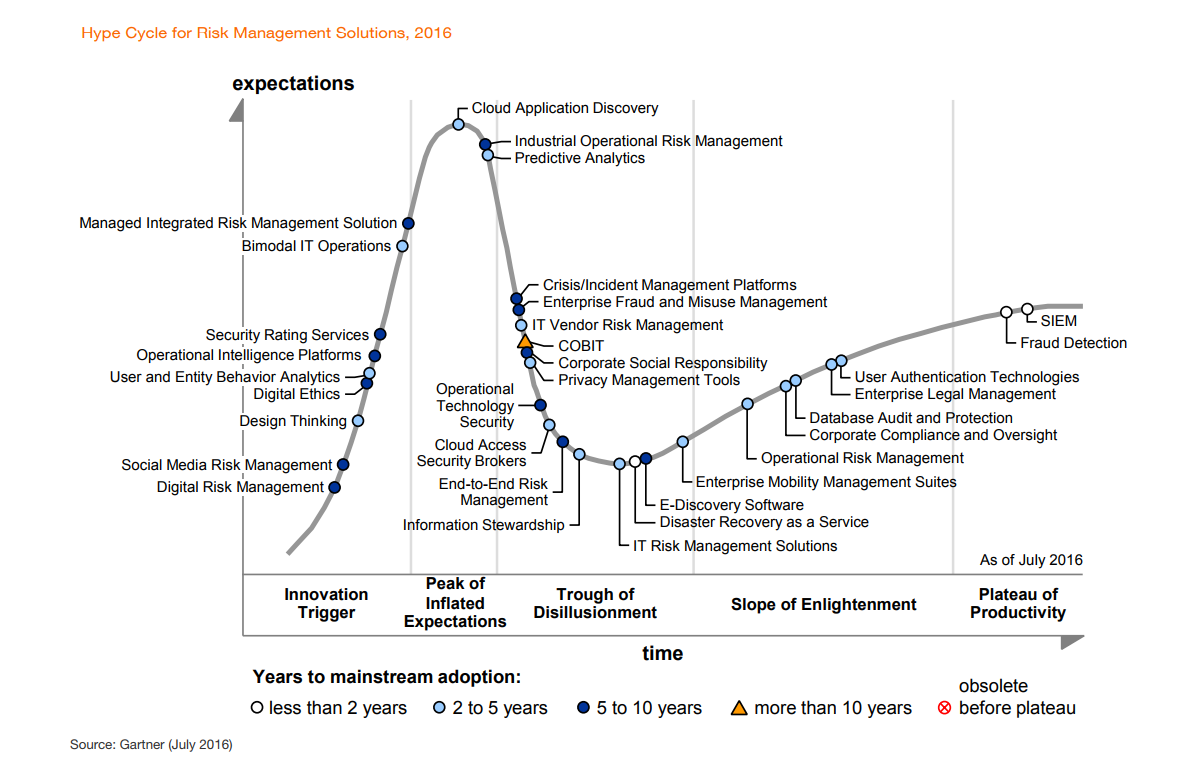
Advanced analytics technologies like UEBA are on the rise because of the high demand to have more context around insider behavior, which many traditional monitoring solutions simply misses. Take a look at Gartner’s Hype Cycle for Risk Management Solutions diagram below:
Gartner, Hype Cycle for Risk Management Solutions, 2016
UEBA uses user behavior and advanced analytics to identify insider threats, which would otherwise go unnoticed, in their early stages. UEBA is not a brand-new technology — it has been on the market since 2015 — but it’s still in the Innovation Trigger stage.
Organizations are thirsty for advanced analytics because the deeper and more precise analytics about user behavior they get, the better they can mend their security holes, detect threats, and investigate breaches and other incidents. Gartner forecasts that spending on UEBA stand-alone platforms will grow at a CAGR of 48%, from $50 million in 2015 to $352 million in 2020. (Gartner, Forecast Snapshot: User and Entity Behavior Analytics, Worldwide, 2017, 03 March 2017)
But before you rush to incorporate UEBA in your IT environment, be sure to take the following steps:
- Identify your primary use cases for UEBA. For example, you may want to more effectively spot insider threats, or improve operational efficiency by adding more context and slashing the number of alerts. Keeping your use cases crystal clear helps you better understand your true business need and assess possible solutions more thoughtfully. (We’ll discuss developing good use cases in more detail in the fourth blog post in this series).
- Evaluate whether your existing security solutions can cover the use cases you’ve identified. Keep in mind that UEBA can be implemented both as a feature and as a stand-alone solution. Your SIEM provider might already include some UEBA functionality that you don’t know about. If it does, then double-check whether the use cases you defined are all covered.
- If your use cases are not covered, consider how UEBA might co-exist with the existing solutions in your security landscape. For instance, you might have a pool of logs with valuable filtered monitoring data collected by your SIEM that you could easily ingest into a standalone UEBA solution, and thereby gain more context, minimize the risk of suspicious activity going under your radar and slash incident response time.
Leverage UEBA as a feature unless you have sufficient resources to add yet another tool
– Avivah Litan, VP and Distinguished Analyst and Toby Bussa, Research Director at Gartner Inc. Gartner Event Presentation, To the Point: Understanding the UEBA Landscape, Gartner Security & Risk Management Summit, 12 –15 June 2017 / National Harbor, MD
- Remember that UEBA is not a panacea. You still need to have a basic security detection strategy in place, implemented with SIEM, DLP, IAM or other technologies. Plus, you can’t fully rely on advanced analytics to replace the security experts who know your IT ecosystem and can make decisions based on their knowledge and experience.
Even with super-smart machines, human adversary, with all his/her irrationality, will be hard to predict
– Gartner Webinar, How to Test, Deploy and Operationalize User and Entity Behavior Analytics Tools, July 11, 2017 Anton Chuvakin, VP Distinguished Analyst at Gartner
Trend #3. Anticipating SIEM–UEBA Evolution
Today, many enterprise-level IT departments view UEBA solutions as a complementary technology, a way to shore up the defenses they maintain using SIEM, DLP, EDR and other tools. This trend of combining SIEMs and UEBA can play out in either or both of two ways:
- SIEM vendors will either acquire UEBA vendors or build their own UEBA features on top of their existing functionality.
- UEBA vendors will grow their arsenal of functionality, such as the log collection traditionally performed by SIEMs, to cover basic security needs.
By 2022, the stand-alone UEBA market will disappear.*
The other prediction is:
By 2020, at least 60% of major cloud access security broker (CASB) vendors and 25% of major SIEM and DLP vendors will incorporate advanced analytics and UEBA functionality into their products, either through acquisitions, partnerships or natively.**
(* Gartner, Forecast Snapshot: User and Entity Behavior Analytics, Worldwide, 2017, 03 March 2017 **Gartner Event Presentation, To the Point: Understanding the UEBA Landscape, Toby Bussa, Avivah Litan, Gartner Security & Risk Management Summit, 12 –15 June 2017 / National Harbor, MD)
UEBA is a great complement to SIEMs because it delivers additional context to security events that miss important details, doing the heavy lifting for security officers that are overloaded and fatigued by high alert volumes and ineffective detection. While SIEM solutions are good at detecting the known threats, UEBA help identify the unknown threats and malicious user activities that would otherwise go unnoticed.
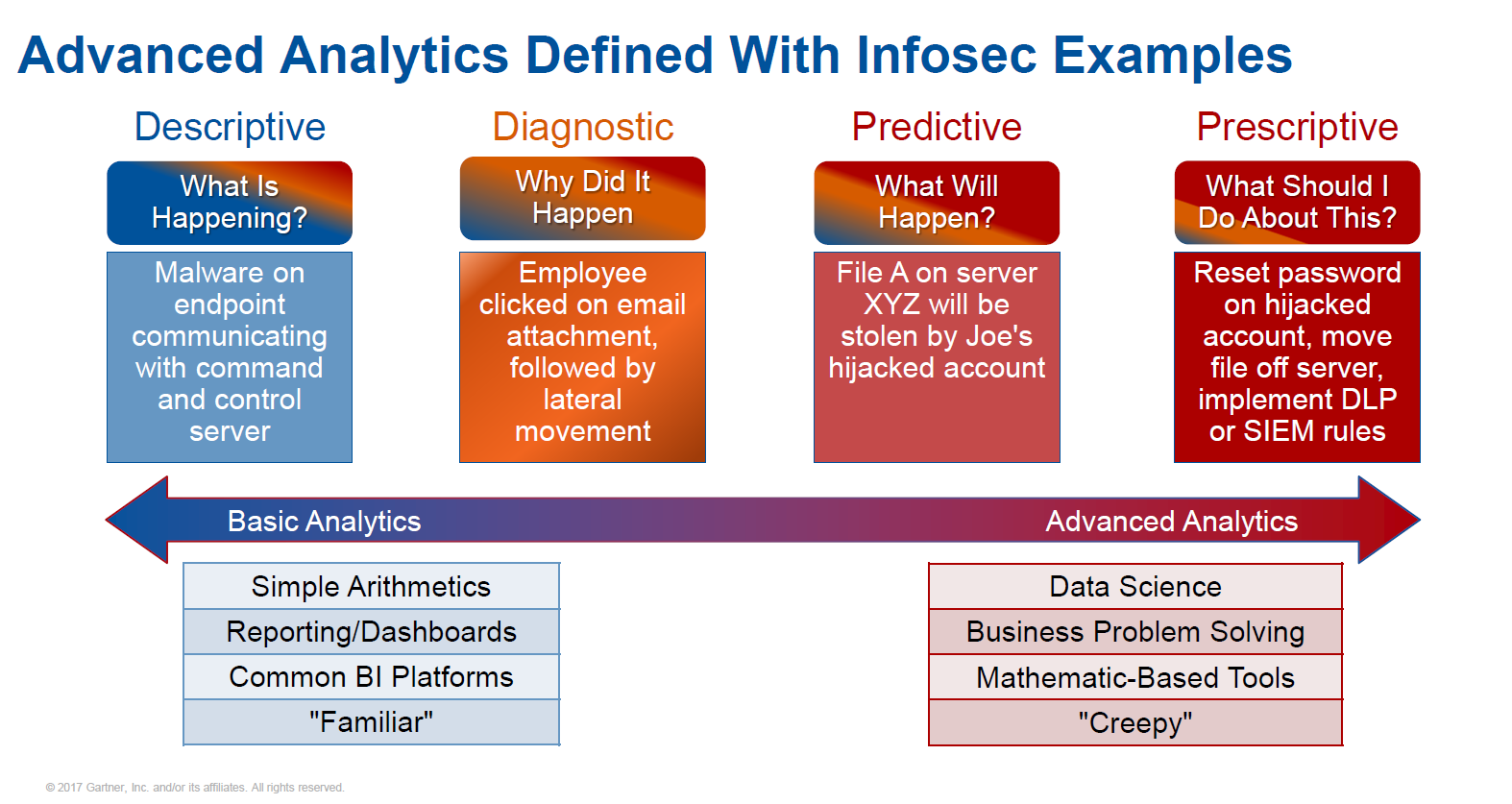
If we take a look at the development of security analytics, we can see that UEBA is a stepping-stone from the diagnostic to the predictive, and also helps provide a prescriptive approach to combating threats. It enriches dispersed raw log data (which contains events that already happened) with a history of user behavior in order to detect atypical actions and foresee possible security risks.
Gartner Event Presentation, To the Point: Preparing for Disruptions in Security and User and Entity Behavior Analytics Platforms, Aviva Litan, Toby Bussa, Gartner Security & Risk Management Summit, 12 –15 June 2017 / National Harbor, MD
While SIEM vendors keep growing functionality for their products, the solutions remain complicated and hard to deploy. Organizations are eager to reduce time to value, and integrating your existing SIEM with UEBA is one of the ways you can significantly improve your ROI. Moreover, you’ll be better enable to identify and analyze bad actions faster, improve your signal-to-noise ratio, handle alerts more efficiently by prioritizing them, and expedite response to security threats.
Trend #4. Staying Pragmatic while Combatting your Environment-Specific Threats
Earlier in this blog posts, I encouraged you to carefully lay out your use cases and investigate the functionality of your existing solutions before investing in new tools. On top of that, you need to carefully evaluate the security posture of your IT environment to discover any holes that might leave you vulnerable. But if your current solutions cannot address all of your use cases and enable you to close the gaps you identify, how can you find the right tools to add in this kaleidoscopic world of IT security challenges?
Anton Chuvakin, a Gartner expert, highly recommends conducting a POC of several tools over 30-90 days* focusing on the specific use cases you are trying to solve, and also considering whether they will scale to meet your future needs. (*Gartner Event Presentation, How to Deploy and Operationalize User and Entity Behavior Analytics (UEBA) Tools, Anton Chuvakin, Gartner Security & Risk Management Summit, 12 –15 June 2017 / National Harbor, MD)
Here are some additional specific tips that I find useful:
- Recognize that different advanced analytics solutions solve different problems. For instance, one solution might be good at monitoring employees for abnormal or abusive behavior only, while another might shed more light on data exfiltration activities.
- Don’t rely too much on your peers’ product reviews. Every ecosystem is unique, budgets vary, so what works best for one organization may not be the best for another.
- Test the solutions in your environment so you’ll know exactly how they will fit into your IT environment and business processes.
- Include time to value in your assessment. Some solutions take much longer to deploy, involve educating IT staff or end users, and require revisions to your business processes. These delays can add up.
- Remember that not all that glitters is gold. “Note that advanced is very elusive,” Anton warns. For instance, one of the top requirements for UEBA solutions is machine learning-based analytics. Machine learning can dramatically reduce the number of false-detects and identify threats that other security solutions couldn’t simply spot. But a lot of machine learning solutions are not working quite as expected. So do your homework, and count machine learning as a plus only if the UEBA vendor has truly mastered it.
Even with super-smart machines, human adversary, with all his/her irrationality, will be hard to predict
– Gartner Webinar, How to Test, Deploy and Operationalize User and Entity Behavior Analytics Tools, July 11, 2017 Anton Chuvakin, VP Distinguished Analyst at Gartner
By staying focused on your specific use cases and seeing whether your existing solutions can cover them, you can find advanced analytics technologies that can help you shift from a diagnostic to a predictive approach.
But no matter which solutions you ultimately choose, it’s critical to understand that you can’t build the ultimate armor against all cyber threats. Attacks are getting both more frequent and more sophisticated, and we simply don’t know what we’ll face next. You might as well hire a fortuneteller to watch out for emerging threats for you. But there is a way to prepare yourself to better face these new threats — making your IT architecture more adaptive.
Good luck fighting this battle.