Healthcare organizations face severe IT risks where expectations often fail to match reality. While data breaches rank as the top concern, human error and insider misuse cause the majority of incidents, from data loss to system disruption. Real-world cases show that physical damage, IP theft, ransomware, and compliance failures jeopardize patient safety and trust. With per-record breach costs among the highest in any industry, healthcare must prioritize identity-first security and proactive risk detection.
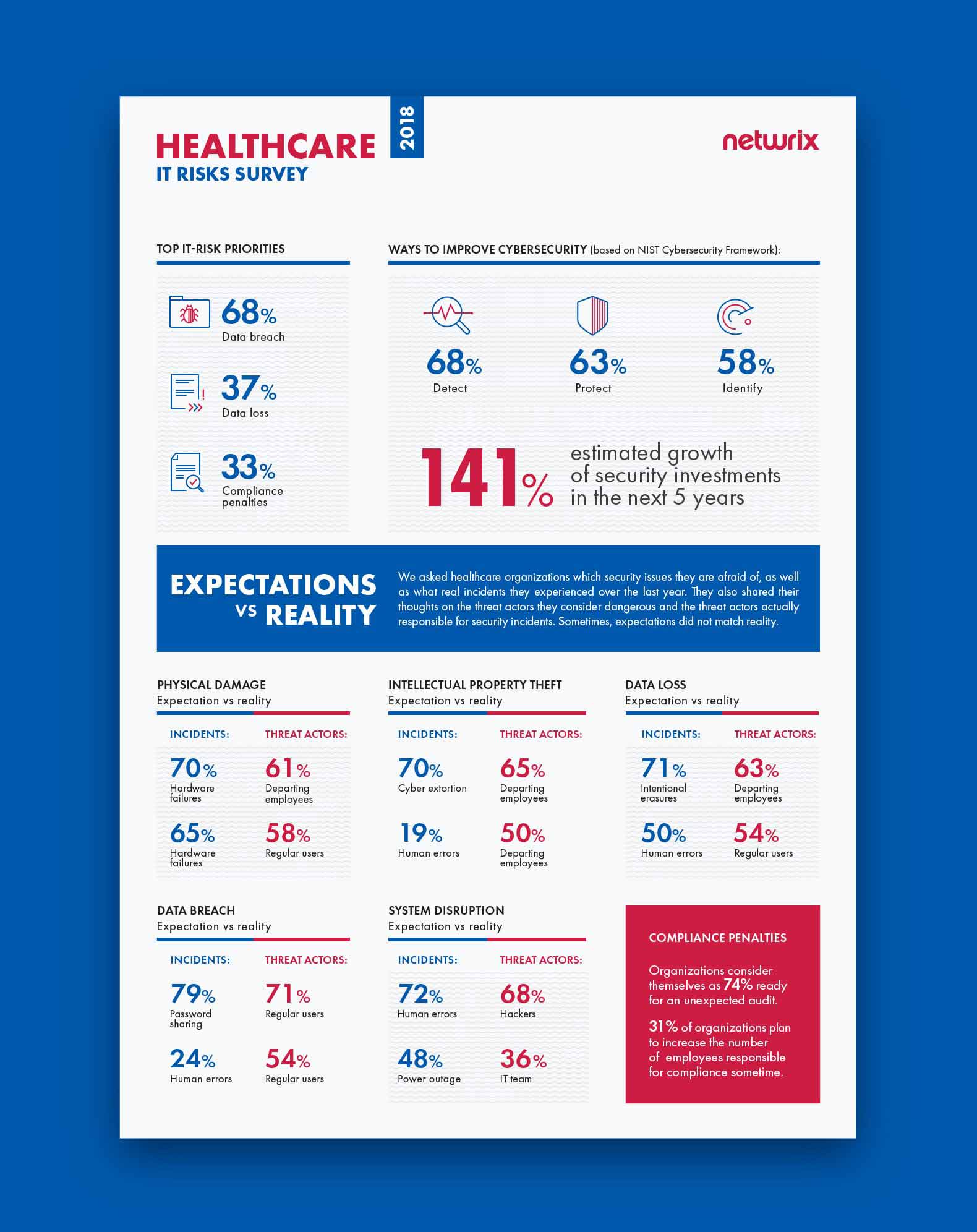
Netwrix conducted its 2018 IT Risks Survey to learn more about how organizations deal with six common IT risks: physical damage, intellectual property theft, data loss, data breaches, system disruption and compliance penalties. We have extracted some interesting data shared by 140 healthcare organizations to learn more about how the industry perceives its threats. Mainly, we were keen to find out whether expectations about these risks match reality — that is, whether the incidents organizations are most worried about are the same as ones they experienced over the year, and whether the threat actors they are afraid of are actually responsible for the real incidents.
To illustrate how dangerous these IT risks can be for businesses worldwide, we decided to support the survey results with real-world examples of how they have affected healthcare organizations.
Physical damage
Physical damage is any damage to an organization’s hardware assets, such as its servers, laptops and network devices. Threats that lead to physical damage include natural disasters, improper storage environment, inadequate hardware maintenance or careless handling, employees’ mistakes, and purposeful attacks by hackers. For healthcare organizations, physical damage can lead to loss of protected personal healthcare information (PHI), system outages and inability to provide medical services. In some cases, physical damage is a direct threat to patients’ lives and well-being: If critical equipment is out of order, patients might not get the level of care they urgently need.
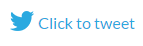
The survey reveals that overall, expectations do match reality when it comes to physical damage. Healthcare organizations consider hardware failures to be the most dangerous security threat, and in fact they are the type of incident that organizations experienced most frequently over the past year. However, there is a gap between the threat actors that organizations consider dangerous and threat actors that are responsible for real incidents. The majority (61%) of organizations see departing employees as the biggest threat, while in reality, it’s regular users who are responsible for the most incidents (58%); disgruntled ex-employees lag well behind, in third place (23%).
Case study: Port Shepstone hospital on fire
In May 2017, a fire occurred at Port Shepstone Provincial Hospital in South Africa. The fire started in the IT server room, destroying computers and other equipment. 200 patients had to be transferred to other hospitals in the area, and several hospital services (e.g., elective eye operations) were temporarily unavailable. A spokesperson for the municipality, Simon April, said the hospital might have lost data stored on its servers as well: “Considering that the server room is the central point where the information is kept, it is possible that information was lost, unless they have some back-up system.”
Intellectual property theft
Intellectual property (IP) includes extremely sensitive information that is protected by copyright, trademark or trade secret laws; cases in which a person intentionally steals or misuses these assets are called intellectual property theft. The risk of IP theft is a particular concern for pharmaceutical companies involved in the research and development of new medicines. Because this research is extremely valuable and the rivalry between pharmaceutical companies is intense, it is no surprise that we often see news about hackers or insiders who have stolen or tried to steal IP for financial gain or revenge.
Intellectual property theft can be driven by competition between corporations, and it can also be undertaken by hackers and malicious insiders. In any case, the potential consequences for healthcare organizations include loss of a competitive edge, slowdown in business growth and loss of highly valuable plans regarding drug development.
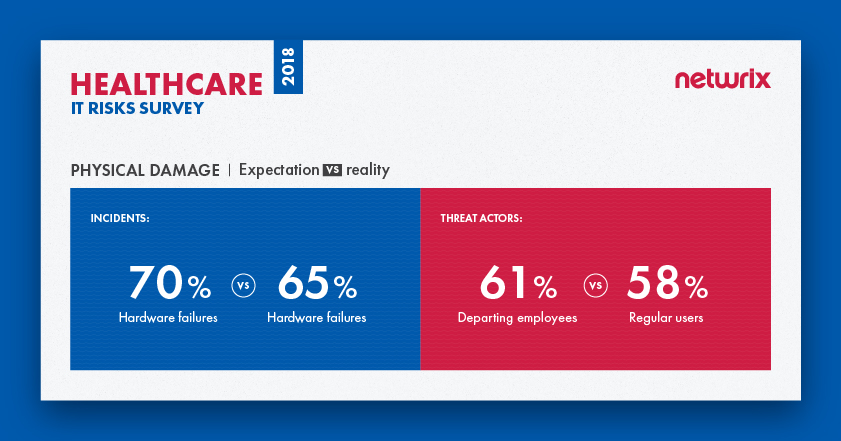
The survey reveals that healthcare organizations do not always understand which activities pose a threat to their intellectual property. Overall, 70% of companies stated they are afraid of cyber extortion, but human errors were actually responsible for the most incidents last year affecting the intellectual property of healthcare organizations; cyber extortion ranked down in fourth place. Although intellectual property theft is mostly associated with malicious intent, human mistakes are more likely to lead to loss of valuable trade secrets, patents and other sensitive data. For instance, negligent IT team members might give excessive access rights to disgruntled employees who are secretly ready to quit, and regular users can make mistakes like clicking on a phishing link that downloads malware, putting intellectual property in danger.
In terms of threat actors, expectations do match reality. The results show that healthcare organizations fully understand who is most dangerous for them — it’s departing employees who cause the most trouble in reality and whom organizations are afraid of.
Case study: Former GlaxoSmithKline employees steal trade secrets
In 2016, five people, including two former research scientists of the pharmaceutical giant GlaxoSmithKline (GSK), were charged in the U.S. with scheming to steal trade secrets and sell them in China. According to prosecutors, the two scientists emailed confidential data about a dozen or more GSK products to their associates, who planned to market the trade secrets through a company they set up in China and go into direct competition with GSK. The stolen data involved information regarding development of multiple biopharmaceutical products, as well as information about GSK research, development and manufacturing of biopharmaceutical products. In 2018, both scientists pleaded guilty to committing intellectual property theft, but the exact amount of financial damage has yet to be calculated.
Data loss
Data loss usually happens when information is destroyed by failures during storage, processing or transmission. Data loss can be deliberate (e.g., erasure, session hijacking, malware infiltrations and IoT exploits), or the result of human mistakes. Another scenario is when a portable device with access to sensitive data is lost or stolen. The consequences of such incidents for healthcare organizations can be severe. If the extremely sensitive data of their clients and employees, which includes personal information, financial data and results of clinical examinations, ends up in the wrong hands, it might be used for phishing attacks, blackmail or fraud. Even if patient data is lost rather than stolen, vital healthcare procedures might be delayed and important decisions might be less well informed. In either case, the company might experience loss of customer loyalty, decrease in business velocity or even bankruptcy.
Loss of other types of data are also a major concern for healthcare organizations. For example, if a pharmaceutical company loses information regarding clinical trials, it might have to start the entire research and development process all over again and therefore fail to launch a new product before a competitor does. Ultimately, the company can lose its competitive advantage and market share, in addition to the time and money spent reproducing the data.
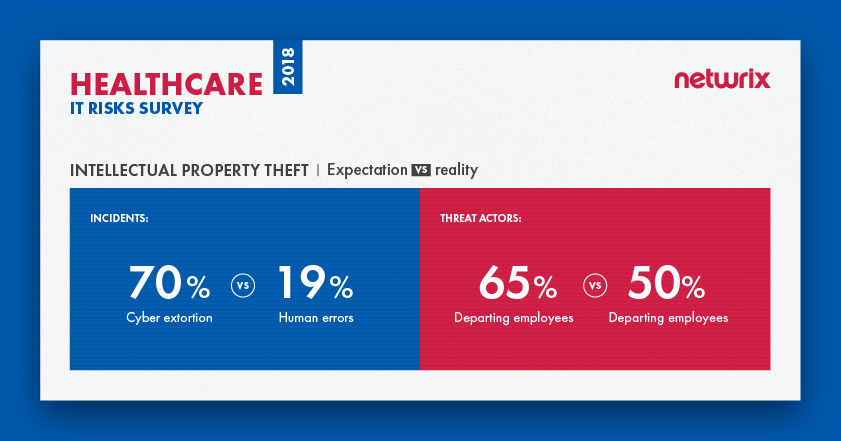
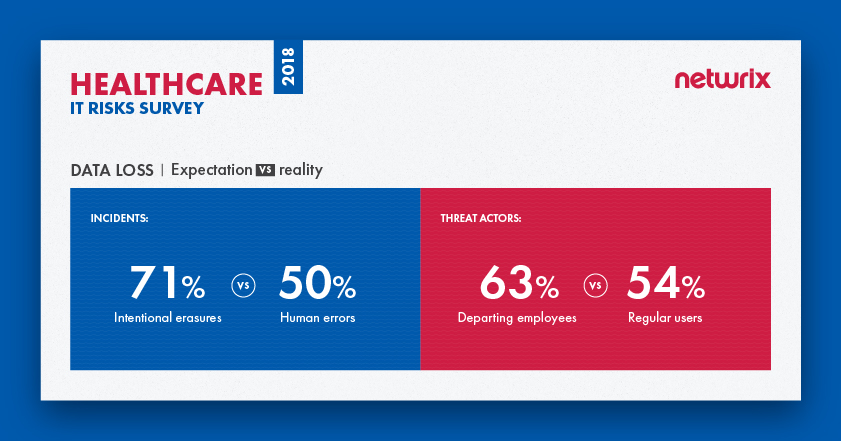
Most data loss (54%) in the healthcare industry is caused by regular users
The survey results indicate that most healthcare organizations fear intentional erasures, while in fact they need to pay more attention to human errors, which are the real number one cause of incidents involving data loss. Intentional erasures are not even in the top five; they were named by only 11% of respondents, which is far less than other causes of data loss (e.g., hardware failures and lost/stolen devices).
In terms of threat actors, again we see that organizations don’t fully understand whom they need to be afraid of. They fear departing employees more than anyone else (63%), while in reality it is regular business users who cause most data loss. Once again, departing employees may seem dangerous, but they are not even close to being leaders among other threat actors — only 21% of respondents said departing employees participated in real incidents.
Case study: A cancer center in Texas loses large amounts of sensitive data
In 2018, the U.S. Department of Health and Human Services’ Office for Civil Rights announced its fourth largest HIPAA violation penalty, issued to the University of Texas MD Anderson Cancer Center. The case stems from three incidents in 2012 and 2013: An employee’s laptop was stolen and two thumb drives went missing; all of the devices stored electronic protected health information (ePHI) of MD Anderson patients.
In total, the PHI of 34,883 patients was lost and might have been exposed to unauthorized individuals. Analysis revealed that the portable devices containing ePHI were not encrypted, which was a direct violation of HIPAA. Due to their failure to implement security controls required by HIPAA, MD Anderson was ordered to pay $4,348,000 in penalties.
Data breach
Unfortunately, the healthcare industry is not a stranger to data breaches. Recent headline-making breaches include the Premera Blue Cross and Anthem incidents, both in 2015. A data breach is a confirmed security incident in which sensitive, protected or confidential data is copied, transmitted, viewed, stolen or used by an unauthorized individual. In case of the healthcare industry, data breaches often involve the compromise of PHI, but some cases include other types of data, such as payment information or personally identifiable information (PII).
According to the Verizon 2018 DBIR, the most frequent threat pattern for breaches in healthcare is miscellaneous errors, mainly in the form of misdelivery and unintended disclosure. Consequences of a data breach include massive leaks of extremely sensitive data, which can be easily sold on the black market or used for extortion and fraud, as well as lawsuits from enraged customers, substantial compliance fines and reputational damage.
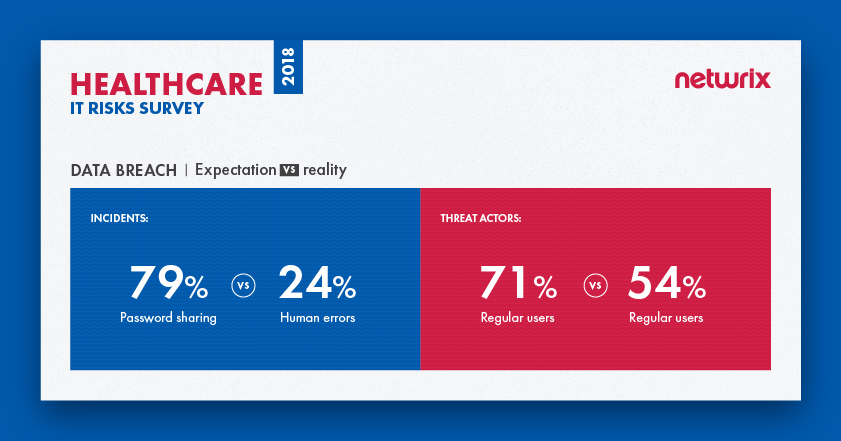
68% of healthcare organizations named data breaches their top priority among IT risks
The majority of survey respondents (68%) named data breaches their top priority among IT risks. Most healthcare organizations (79%) named password sharing as the most dangerous threat pattern. But in reality, most breaches were caused by human errors (24%), such as unintended disclosure or clicking on phishing links. Expectations did match reality regarding threat actors, however: Regular users are seen as the main threat actor and are the main threat actor in reality.
Case study: Premera Blue Cross is in the centre of data breach scandal
In 2015, health insurance giant Premera Blue Cross revealed that a database with information on more than 11 million customers was compromised during a breach in May 2014. A company employee fell victim to a phishing attack that enabled hackers to install malware on the insurer’s network. In a public statement, Premera said that the attackers might have gotten access to customers’ clinical information, banking account numbers, Social Security numbers, birth dates and more.
In April 2014, the U.S. Office of Personnel Management (OPM) warned Premera that it “found numerous security flaws during a routine audit of Premera’s systems” just a month before the incident was revealed. As a result, Premera Blue Cross faced a substantial class-action lawsuit, which argued that Premera failed to adequately protect its customers’ personal information and notify them of the data breach in a timely manner. Moreover, according to court documents revealed in 2018, Premera is now accused of intentionally destroying a computer and software logs that might have provided evidence that hackers stole data from its systems after the class-action lawsuit had been filed.
System disruption
A system disruption (or service interruption) is the failure of certain systems to provide or perform their primary function for a period of time. Common reasons include system failures (including power outages), natural disasters, malicious techniques used by both outsiders and insiders (e.g., DDoS attacks, sabotage and ransomware), and human mistakes. For healthcare organizations, unplanned downtime means that they cannot function effectively, since the disruption might affect every aspect of their operations, from patient care to admissions to supply chain and more. For example, a system disruption might prevent an organization that relies on electronic health record (EHR) systems from registering patients, scheduling appointments and accessing test results. System disruptions also create problems for organizations that provide clinical healthcare to patients from a distance using IT (telemedicine), and for pharmaceutical companies, which might not be able to continue their research and therefore lose precious time and money.
Once again, expectations do not match reality here. Although human mistakes (72%) are considered the leading cause of system disruption, most incidents are actually the result of power outages (48%); human mistakes place second (45%). And while healthcare organizations blame hackers for most system disruption, they report that it’s IT team members who are responsible for most real incidents (36%); hackers lag behind in sixth place, named by 29% of respondents.
Case study: NHS suffers largest ransomware attack ever
Though ransomware wasn’t the top cause of real system disruptions, one well-known case that illustrates the consequences of system disruption in the healthcare industry is ransomware-related. Because it affected several hospitals at once, there was a massive public outcry. You guessed it — it’s the WannaCry NHS case in the UK.
When the WannaCry cyberattack spread worldwide in 2017, the British NHS was the worst hit. Hospitals and GP surgeries in England and Scotland were among at least 16 health service organizations hit by the ransomware attack, which used malware called Wanna Decryptor to encrypt data. The demand for payments of $300 to $600 to restore access was the least of the problem — the attack caused major disruptions to surgery schedules in the UK. Since the attack affected key systems, including telephones, staff were forced to revert to pen and paper and use their own mobiles for daily operations. They also had to turn away patients and cancel appointments; patients were advised to seek medical care only in emergencies.
Compliance penalties
Compliance penalties are not be exactly an IT risk, but they are a major concern for healthcare organizations. Compliance standards get stricter and new ones appear regularly, so adhering to all the requirements is increasingly challenging. Healthcare organizations have to comply not only with standards specific to their industry (e.g., HIPAA and the HITECH Act), but also with standards like PCI DSS if they accept credit card payments. The most obvious consequence of non-compliance is huge fines: For example, fines for HIPAA violations can reach $50,000, or up to $1.5 million for repeat violations.
Compliance standards require organizations to prove that PHI and other personal data of patients and employees are thoroughly protected at all times. Our survey found that healthcare organizations consider themselves as 74 % ready for an unexpected compliance check. About a third (31%) of organizations say that they plan to increase the number of employees responsible for compliance sometime; however, others (24%) say that they don’t plan to hire additional people for compliance tasks in the future.

Case study: Anthem agrees to pay the largest HIPAA breach settlement in history
In December 2014, hackers compromised a database owned by Anthem, the second largest health insurer in the U.S. The compromise wasn’t discovered until January 27, 2015, after a database administrator discovered his credentials being used to run a suspicious query. In the interim, hackers stole the data of 78 million plan members, including their names, addresses, dates of birth, medical identification numbers, employment information, email addresses and Social Security numbers.
In 2018, Anthem agreed to pay a $16 million fine for the 2015 data breach and to undertake a robust corrective action plan to address the compliance issues discovered by Office of Civil Rights (OCR) during the investigation. This fine is more than triple the previous record HIPAA breach settlement amount of $5.55 million, levied against Advocate Health Care in 2016.
Summary and future plans
The survey results show that the expectations of healthcare organizations do not necessarily match reality. In fact, human errors or malicious actions by business users usually do more harm than malware infiltrations and other hacker activities.
Data breaches top the list of IT risks that most influence the industry, which is not a surprise, considering the severe consequences that organizations have to face if they suffer a data breach. These can involve litigation, reputational damage, loss of customer loyalty, suspension or loss of license and, of course, financial damage — the 2018 Ponemon Cost of Data Breach Study says that healthcare industry has the highest per capita data breach cost of all industries (around $408 for each lost or stolen record).
Healthcare organizations take these risks seriously. They plan to increase their security investments by 141% in the future, and they consider detection of security incidents as the key way to improve cybersecurity.
View the full infographics with the 2018 IT Risks Survey results for the healthcare industry here:
FAQ
How to prevent data breaches in healthcare?
Preventing healthcare data breaches requires a defense-in-depth approach that starts with identity security. The most effective strategy combines access controls, continuous monitoring, and incident response planning. Implement least privilege access principles – healthcare workers should only access patient data necessary for their specific role. Deploy real-time monitoring systems that can detect unusual access patterns, such as a nurse suddenly accessing hundreds of patient records outside their department. Regular security awareness training is crucial, as human error contributes to the majority of healthcare breaches. Don’t forget the basics: patch management, encryption of data at rest and in transit, and secure backup procedures. The key insight most healthcare organizations miss: preventing breaches isn’t about perfect security – it’s about making your organization a harder target than competitors.
What is HIPAA compliance and why does it matter?
HIPAA compliance is the healthcare industry’s framework for protecting patient privacy and securing protected health information (PHI). It matters because compliance extends beyond avoiding fines (which can reach millions of dollars). HIPAA compliance builds patient trust, reduces legal liability, and creates a security-conscious culture throughout your organization. The regulation covers three main areas: the Privacy Rule (who can access PHI), the Security Rule (how to protect electronic PHI), and the Breach Notification Rule (what to do when things go wrong). Forward-thinking healthcare organizations view HIPAA as a competitive advantage rather than a burden – patients increasingly choose providers they trust with their most sensitive information.
Why is cybersecurity important in healthcare?
Healthcare cybersecurity is critical because patient safety and data privacy are inseparable in modern medicine. When cyber attacks disrupt hospital systems, they don’t just compromise data – they can delay critical treatments, cancel surgeries, and force emergency departments to divert patients. Healthcare organizations store some of the most valuable data on the dark web: complete medical histories, Social Security numbers, insurance information, and financial data all in one place. Unlike credit card numbers that can be quickly canceled, medical identity theft can take years to resolve and can be life-threatening if falsified medical records lead to incorrect treatments. The rise of connected medical devices and telemedicine has exponentially expanded the attack surface, making robust cybersecurity not just important – it’s essential for patient care and organizational survival.
What are the biggest healthcare IT risks?
The biggest healthcare IT risks combine traditional cyber threats with industry-specific vulnerabilities. Insider threats top the list – healthcare workers with legitimate access who intentionally or accidentally misuse patient data account for the majority of incidents. Ransomware attacks specifically targeting healthcare systems have grown exponentially, with attackers knowing hospitals can’t afford extended downtime. Medical device vulnerabilities represent an emerging threat as more devices connect to hospital networks without adequate security controls. Supply chain attacks through third-party vendors provide attackers with backdoors into healthcare networks. Don’t overlook the human factor: phishing attacks that trick staff into providing credentials or downloading malware remain devastatingly effective. The most dangerous risk is organizational complacency – assuming that good intentions and regulatory compliance alone are enough to prevent sophisticated, motivated attackers.
How to implement healthcare cybersecurity best practices?
Implementing healthcare cybersecurity best practices requires balancing security with the operational realities of patient care. Start with identity and access management – ensure every user has unique credentials and implement multi-factor authentication across all systems. Deploy network segmentation to isolate critical medical devices and patient data systems from general IT infrastructure. Establish continuous monitoring that can detect anomalies without generating alert fatigue for already busy IT teams. Create incident response plans specifically tailored to healthcare scenarios where system downtime directly impacts patient safety. Regular vulnerability assessments and penetration testing should focus on both IT systems and medical devices. Most importantly, foster a security-conscious culture through ongoing training that helps staff understand how cybersecurity directly connects to patient care quality and safety.