Cloud Usage
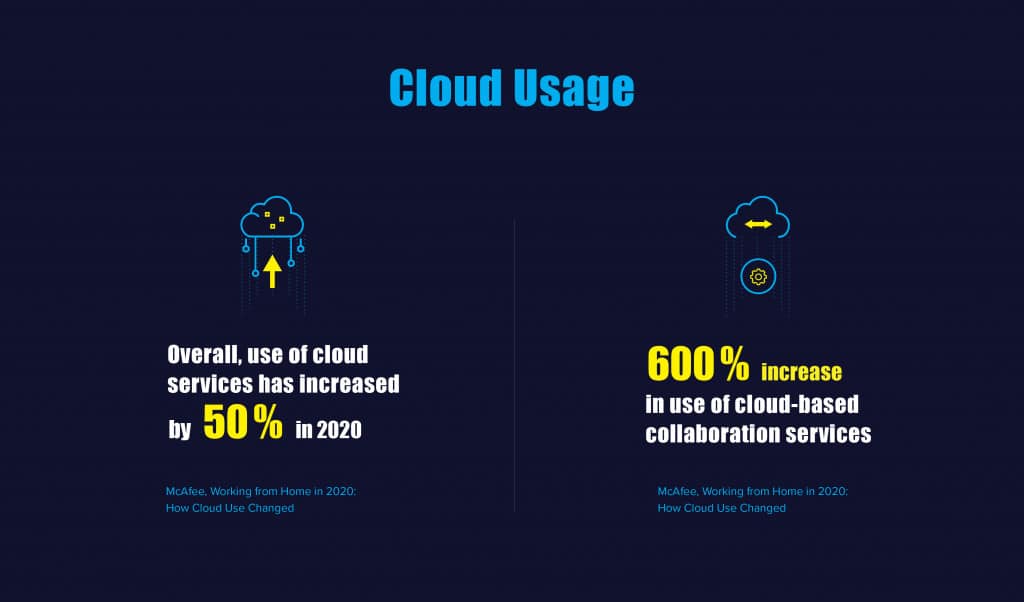
The cloud had become mainstream during the last couple of years, but the year of 2020 has pushed companies to adapt to remote working, which immediately led to a rapid adoption of cloud services. Research indicates that overall use of cloud services across industries has already increased by 50% this year; the most serious effect from the shift to remote working was on cloud-based collaboration tools, which saw an increase of up to 600% in usage (McAfee).
More organizations are undertaking cloud-related initiatives this year than in 2019, and the most substantial growth was in moving on-premises software to SaaS (Flexera).
The future of cloud services is far from cloudy, since remote working will stay with us for a long time. Indeed, 74% of CFOs and finance leaders responding to a recent Gartner survey said they intend to move at least 5% of their on-site employees to remote positions on a permanent basis.

Cloud security concerns
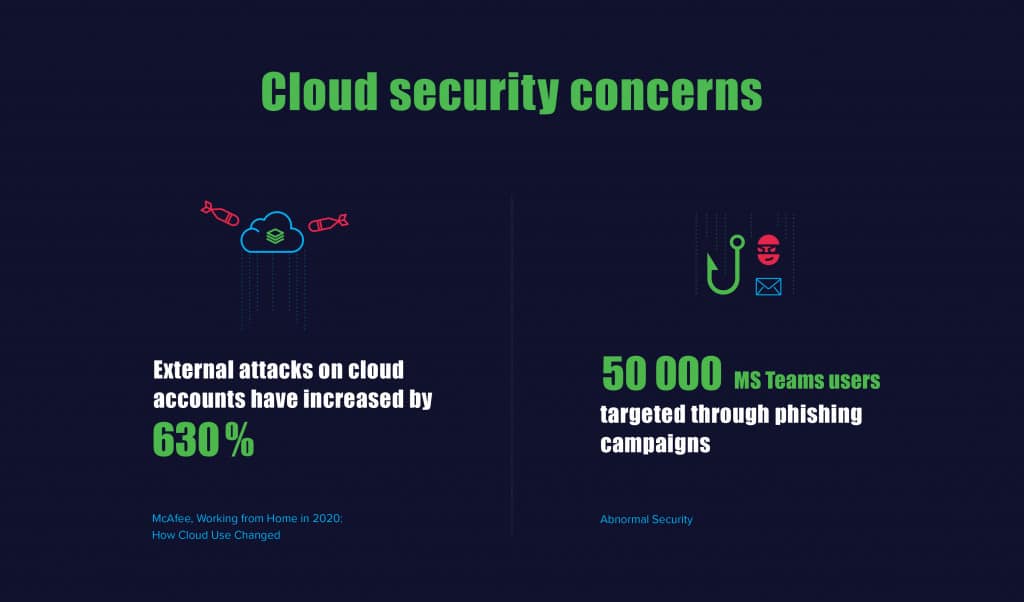
As cloud usage expanded this year, attackers used the chaos and stress to exploit cloud environments. Experts saw a 630% increase in external attacks on cloud accounts (McAfee). In particular, by May 1, two phishing attacks had targeted close to 50,000 Teams users through malicious emails (Abnormal Security).
What makes these attacks likely to succeed? Misconfigurations and other human errors that are a result of hasty deployments (FireMon).
Unfortunately, poor security hygiene is frequent. For example, the Unit 42 Cloud Threat Report found that 60% of cloud storage services have logging disabled, which makes it almost impossible to thoroughly investigate incidents and assess damage. This problem is not new: Last year’s Oracle Cloud Threat Report noted that only 1 in 10 organizations could analyze over 75% of their security events both on premises and in the cloud.

Conclusion
The current explosion in use of cloud services and the corresponding increase in cyberattacks is a call to treat cloud security as a strategic imperative, one that is shared by cloud users and cloud providers. Key security strategies include proactively mitigating security gaps; staying alert to unusual activity; and knowing where your regulated and sensitive data resides and how that data flows, both inside and outside the perimeter.
 of ENG [Free Trial] short-840x350.jpg)


