What is DNS?
DNS (Domain Name System) is a key component of the Internet infrastructure. DNS functions as a distributed directory service that translates human-readable domain names into machine-readable IP addresses. When you type a website address into your browser, the DNS system helps your browser find the right server on the internet. When people type names like www.test.com, DNS translates domain names into IP addresses so that browsers can load internet resources.
DNS uses a hierarchical and distributed database to manage the mapping of domain names to IP addresses. This hierarchy includes root servers, TLD (Top-Level Domain) servers, and authoritative DNS servers. To improve efficiency and speed, DNS responses are often cached at several levels, including on your local machine and DNS servers, so repeated queries for the same domain can be resolved faster.
Traditional DNS process
DNS process ensures that you are directed to the correct website associated with the domain name you entered. The traditional DNS process involves below steps.
- User Request: When you type a domain name into your browser, a DNS query is initiated to find the IP address associated with that domain.
- DNS Resolver: Your query first goes to a DNS resolver, which is typically provided by your Internet Service Provider. The resolver’s job is to find the IP address by querying other DNS servers if it does not already have the information cached.
- Root DNS Server: If the resolver does not have the answer, it queries one of the root DNS servers. The root servers do not have the IP addresses but direct the resolver to the appropriate Top-Level Domain (TLD) DNS servers (e.g., for .com or .org).
- TLD DNS Server: The TLD server directs the resolver to the authoritative DNS server for the specific domain.
- Authoritative DNS Server: The authoritative server keeps the actual DNS records for the domain, provides the IP address for the requested domain.
- Response: The resolver receives the IP address from the authoritative server and returns it to your browser.
- Caching: The resolver and your browser cache the IP address for future requests, reducing the need to repeat the lookup process.
Security risks associated with traditional DNS
Traditional Domain Name System (DNS) operations present several inherent security risks. Being one of the oldest parts of internet infrastructure, DNS was not designed with strong security features, which has led to its exploitation in many forms of cyber-attacks. Below are some key security risks associated with traditional DNS:
| DNS Spoofing | This attack involves inserting a false address record into the cache of a DNS server. If attackers can poison the DNS cache, they can redirect users to malicious websites without their knowledge, even if the users type the correct address into their browsers. This method can be used to spread malware or to conduct phishing attacks to steal user information. |
| Man-in-the-Middle (MitM) Attacks | Because traditional DNS queries and responses are not encrypted, they are susceptible to eavesdropping and interception. Attackers can use this vulnerability to insert themselves between the user and their DNS requests, redirecting them to fraudulent sites or spying on their internet activity. |
| DNS Tunneling | Attackers can utilize DNS queries and responses to smuggle data in and out of a network, bypassing traditional network security measures like firewalls. DNS tunneling can be used for data exfiltration, command and control of malware, or bypassing internet usage policies and restrictions. |
| Distributed Denial of Service (DDoS) Attacks | DNS servers can be targeted by DDoS attacks, whereby a network of compromised computers (a botnet) floods a DNS server with an overwhelming volume of queries. This can render the DNS service slow or completely unavailable, disrupting access to websites and online services for legitimate users. |
| Domain Hijacking | By exploiting vulnerabilities or through social engineering attacks (such as phishing), attackers can gain control of a domain’s DNS settings. They can then redirect the domain’s traffic to malicious sites, intercept emails and sensitive information, or disrupt access to the legitimate services hosted under the domain. |
| Zero Day Vulnerabilities | DNS queries and responses are transmitted in plaintext over the network. This makes them susceptible to interception by anyone with access to the network, including ISPs, network administrators, or malicious actors. Attackers can capture and analyze DNS traffic to monitor which websites users are visiting, potentially leading to privacy breaches. |
| Eavesdropping | DNS queries and responses are transmitted in plaintext over the network. This makes them susceptible to interception by anyone with access to the network, including ISPs, network administrators, or malicious actors. Attackers can capture and analyze DNS traffic to monitor which websites users are visiting, potentially leading to privacy breaches. |
| DNS Amplification Attacks | This type of DoS attack involves exploiting the DNS infrastructure to amplify the volume of traffic directed at a target. Attackers send small queries to open DNS resolvers that respond with large answers, overwhelming the target. This can lead to significant service disruptions and network congestion. |
| DNS Rebinding | DNS rebinding attacks involve manipulating DNS responses to make a victim’s browser communicate with internal network addresses or servers. This can expose internal network resources to the internet, potentially leading to unauthorized access or data breaches. |
Introduction to DNS over HTTPS (DoH)
DNS over HTTPS is an advancement in enhancing the security and privacy of internet users. DoH encrypts DNS queries using the HTTPS protocol, which secures communication over the web. By embedding DNS queries within the overall encrypted data traffic between a client and a server, DoH DNS provides a significant privacy advantage. It prevents third parties from seeing what websites you are trying to access. In addition to improved privacy, DoH also enhances security. It helps protect against certain cyber-attacks, such as DNS spoofing or eavesdropping.
The adoption of DoH is growing, with support integrated into many modern web browsers e.g., Firefox, Chrome, and operating systems. Enabling DoH connection involves configuring your web browser or entire device to use a DNS resolver that supports DNS over HTTPS.
Importance of DNS over HTTPS (DoH) in enhancing privacy and security
Traditional DNS queries and responses are sent over plaintext, making them vulnerable to DNS spoofing, eavesdropping, manipulation, or interception by hackers. This can pose significant risks, including the potential for privacy breaches, censorship, and security threats such as man-in-the-middle attacks. DoH resolves these issues by encrypting DNS requests and including them in the HTTPS protocol. HTTPS, being a secure version of HTTP, uses encryption (SSL/TLS) to protect the data transmitted between the user and the server. In regions where internet access is heavily monitored or restricted, encrypted DNS queries can bypass certain types of censorship and filtering, enabling access to information and websites that might otherwise be blocked.
While DoH enhances privacy and security, it is important to select a trustworthy DNS provider (see DNSSEC), as the provider will have the ability to see your DNS queries. With its support, popularity and integration with browsers and operating systems, there is ongoing debate about the centralization risks and potential for abuse, since a few major companies offering DoH services could have access to extensive data about internet user behavior.
Traditional DNS vs DNS over HTTPS (DoH)
Traditional DNS and DNS over HTTPS are both methods of resolving domain names into IP addresses, but they differ significantly in terms of privacy, security, and implementation. DNS over HTTPS offers significant advantages in terms of privacy and security compared to unencrypted DNS. While it requires some manual configuration, for many users, the benefits will outweigh these minor inconveniences.
| Features | Traditional DNS | DNS over HTTPS |
| Encryption | DNS queries and responses are transmitted in plaintext. This means that anyone with access to the network, such as malicious actors, can intercept and read the DNS queries and responses. | Encrypts DNS queries and responses using HTTPS. This encryption prevents eavesdropping and tampering by making the DNS traffic unreadable to unauthorized parties. |
| Privacy | DNS queries are visible to network intermediaries like ISPs and can be used to track user browsing activities. ISPs and other entities can potentially log and monitor DNS requests to infer user behavior and interests. | Provides enhanced privacy by encrypting DNS queries, so they cannot be easily monitored or logged by ISPs or other network observers. Helps prevent tracking of user browsing habits based on DNS traffic. |
| Security | Susceptible to attacks such as DNS spoofing or cache poisoning, where malicious actors can manipulate DNS responses to redirect users to malicious sites. Lack of encryption means DNS responses can be intercepted and altered. | Improves security by ensuring that DNS responses are encrypted and cannot be tampered with during transit. Protects against DNS spoofing and cache poisoning by verifying the integrity of the DNS data. |
| Performance | Typically performs well and is widely supported across all networks and devices. No encryption overhead, so it may have lower latency compared to DoH. | May introduce slight latency due to the encryption and decryption process. In many cases, the performance impact is minimal, and DoH can even offer performance benefits by reducing DNS filtering or interception. |
| Implementation | Universally supported and used by default in most systems and networks. Simple to configure, with no additional setup required for basic functionality. | Requires support from both the client (browser or operating system) and the DNS resolver. Increasingly supported by modern browsers and operating systems but may need manual configuration or updates to enable. |
| Centralization and Management | DNS traffic is generally distributed among several DNS resolvers. Easier for network administrators to manage and monitor DNS traffic. | Can centralize DNS traffic through fewer DoH providers, raising concerns about the concentration of DNS queries with these large entities. |
| Use cases | Suitable for general use where high privacy and security are not primary concerns. Commonly used in most networks and environments. | Ideal for users and organizations prioritizing privacy and security. Useful in environments where protecting against DNS surveillance and tampering is critical. |
| Reliability and Flexibility | Operates over port 53, relies on a hierarchical model (root, TLD, authoritative servers) that can be susceptible to failures and attacks at various levels. | Operates over port 443, allowing DoH traffic to blend with regular HTTPS traffic. This makes it harder for actors to block or censor content without disrupting all web traffic. |
Benefits of DNS over HTTPS
DNS over HTTPS provides several benefits over traditional DNS, as it focuses on enhancing privacy and security for internet users.
Enhanced privacy and security
DNS over HTTPS stands out as a significant improvement due to its encryption of DNS queries over traditional DNS protocols. This encryption ensures that only the user and the DNS resolver can understand the content of the DNS queries and responses. DNS queries are wrapped in the same encryption used for HTTPS traffic, which is the protocol securing most web traffic. This means that DNS queries blend in with the rest of the encrypted internet traffic, making it much harder for any intercepting entity to single out and monitor a user’s DNS requests.
Preventing eavesdropping
Eavesdropping in the context of internet communication is when third parties, such as cyber attackers, ISPs, or even governmental agencies, intercept and monitor data being transmitted over the network. With traditional DNS, these entities can easily see and record the websites a user attempts to visit, posing significant privacy and security risks.
Protects browsing habits
DNS over HTTPS significantly improves user privacy by shielding browsing habits from Internet Service Providers and potential hackers. Traditional DNS queries are conducted in plain text, which leaves users vulnerable to malicious entities and can reveal a user’s browsing habits and visited websites. DoH addresses these vulnerabilities by wrapping DNS queries in HTTPS encryption.
Prevents DNS spoofing and man in the middle attacks
DNS spoofing and man-in-the-middle attacks are common cyber-attacks that can lead to serious security breaches, including theft of sensitive information, delivery of malware, and redirection to malicious websites. DNS spoofing, also known as DNS cache poisoning, occurs when an attacker introduces corrupted DNS data into the cache of a DNS resolver. This manipulated data misleads the resolver into directing users to fraudulent websites even though they enter legitimate addresses. MitM (man-in-the-middle) attacks happen when attackers secretly intercept and alter the communication between user and DNS resolver. DoH mitigates these risks by using encryption and HTTPS to secure the communication channel between the user and the DNS resolver.
DoH Compatibility and support with modern browsers and OS
DNS over HTTPS has widespread support and compatibility with many of the modern web browsers and operating systems.
Web Browsers
- Mozilla Firefox: Firefox was one of the pioneers in adopting DoH, offering it as an option since late 2018, but officially added in February 2020. Users can easily enable DoH within the browser settings.
- Google Chrome: Google also has started testing DoH since late 2018 along with Mozilla, but added support in Chrome in version 83, released in May 2020. The browser automatically upgrades DNS queries to DoH if the user’s DNS service provider supports it.
- Microsoft Edge: Edge also supports DoH, leveraging the same automatic upgrade mechanism for DNS queries provided the DNS service provider supports DoH.
- Opera: Opera browser has also integrated DoH support, allowing users to enable the feature in the settings to secure their DNS queries.
- Safari: Apple’s Safari has started to adopt DoH capabilities as well, with plans to enhance privacy and security for its users through encrypted DNS queries.
Operating Systems
- Windows: Microsoft has incorporated DoH directly into Windows, starting with Windows 10. This integration at the OS level means that all apps and services on the Windows device can benefit from DoH without needing individual support within the apps themselves.
- macOS: Apple, through updates to macOS, has begun to integrate support for encrypted DNS, including both DoH and DNS over TLS (DoT). This allows users to configure network settings to utilize DoH for all DNS queries made by the system.
- Linux: While Linux distributions do not usually come with DoH enabled by default, there are many tools and resolvers such as “systemd-resolved”, “dnscrypt-proxy”, and “Cloudflare’s 1.1.1.1” that Linux users can configure to use DoH.
- Android: Android 9 (Pie) and newer versions support DNS over TLS, and there is growing support for DoH. This can be configured either by using a private DNS option in the network settings (DoT for now) or via specific apps designed to enable DoH.
- iOS: Starting with iOS 14, Apple has provided support for encrypted DNS (both DoH and DoT), allowing users to configure DNS settings either at the device level or per individual network.
How DNS over HTTPS (DoH) works
DNS over HTTPS works by encrypting the data between the user’s device and the DNS resolver.
- Initiation of a DNS Query: When users attempt to visit a website, the browser needs to resolve the domain name into an IP address. With DoH enabled, rather than sending this DNS query over an unencrypted connection, the request is made over HTTPS.
- Encapsulation of the Query in HTTPS: DoH takes the DNS request and encapsulates it within a standard HTTPS request, encrypting the data using SSL/TLS.
- Transmission to DoH-Compatible Resolver: The encrypted DNS query is then sent to a DNS resolver that supports the DoH protocol. These resolvers are responsible for interpreting the query of the domain to IP address.
- Resolver Processes the Query: The DoH-compatible resolver decrypts the HTTPS request to access the DNS query, processes it, finds the corresponding IP address for the requested domain name, and then prepares a DNS response.
- Encrypted Response Sent Back: The resolver encapsulates the DNS response in an encrypted HTTPS response and sends it back to the user’s device.
- Browser Receives and Deciphers Response: Once your device receives the encrypted response, it decrypts the data to extract the DNS information. The browser then uses the provided IP address to establish a secure connection with the web server hosting the website.
- Continuous Secure Communication: After the initial encrypted DNS resolution, further communication between your web browser and the website continues to be encrypted, maintaining a secure connection that protects your data from eavesdroppers.
Differences between DoH and DoT
DNS over HTTPS and DNS over TLS (DoT) are both security protocols designed to protect the privacy of your DNS queries, however, they work in slightly different ways and on different parts of internet connections.
- DoH works over HTTPS and uses port 443, which is the same port used for secure web browsing. DoT uses its own designated port 853 to encrypt DNS queries.
- Both DoH and DoT encrypt DNS queries, but they do it at different layers of internet communication. DoH encapsulates DNS within HTTP traffic, making it part of the web data. DoT encrypts DNS queries at the transport layer, using TLS (Transport Layer Security), but keeps DNS traffic separate from other types of internet traffic.
- DoH can be easily integrated into web browsers and applications because it operates through HTTP. DoT is implemented at the operating system level or on DNS servers.
- Because DoH traffic is indistinguishable from normal HTTPS traffic, it’s much harder for ISPs or anyone on a network to see or block DNS queries. DoT can be easier to block due to its unique port usage.
- Both DoH and DoT improve security and privacy compared to traditional DNS queries, which are unencrypted. The choice between them might depend on your specific needs for privacy, the network you are on, and the devices and applications you use.
DoH enablement in Windows 10 by registry
- Click on the “Start” menu, type “regedit”, and hit Enter. If prompted by User Account Control (UAC), click Yes.
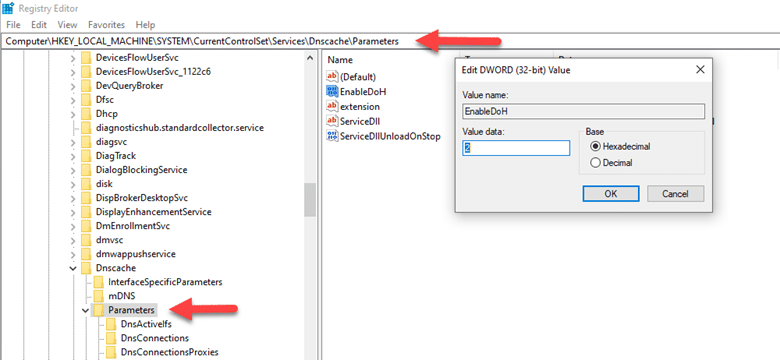
- In the Registry Editor, navigate to the following key “HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Dnscache\Parameters”.
- Right-click on the “Parameters” key, select New, and then DWORD (32-bit) Value. Name this new value “EnableDoh”, set the Value data to 2, and click OK.
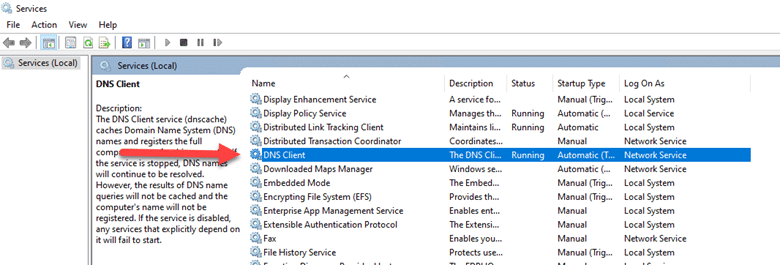
- For the changes to take effect, restart the “DNS Client service” from the Services app.
How to enable DoH in Windows 10
Microsoft has started to support DNS over HTTPS from Windows 10 version 20185 and later. Below are the steps to enable DoH on Windows10.
- Click on the Start menu and click the “Settings” icon or press “Win+I” to open Settings.
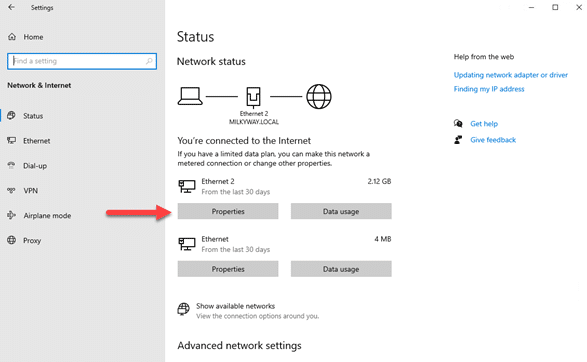
- Go to Network & Internet – Status and click on “Properties” for your active internet connection.
- Scroll down to IP settings and click “Edit” under DNS settings.
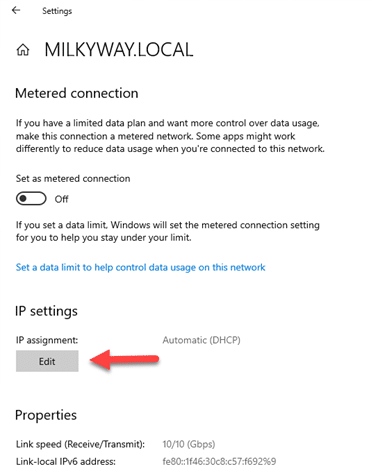
- Change the setting from “Automatic (DHCP)” to “Manual”.
- Provide the IP address of a DNS server that supports DoH. For example, Google’s 8.8.8.8 and 8.8.4.4 for IPv4.
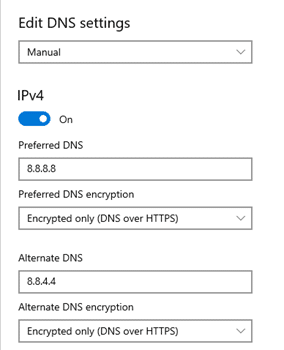
- Select “Encrypted only (DNS over HTTPS)” as the preferred and alternate DNS encryption method.
- Click “Save” to apply your DNS settings.
How to enable DoH in Windows 11
Follow the steps below to enable DNS over HTTPS in Windows 11.
- Press “Win+I” on your keyboard to open the settings.
- Click on “Network & internet” section.
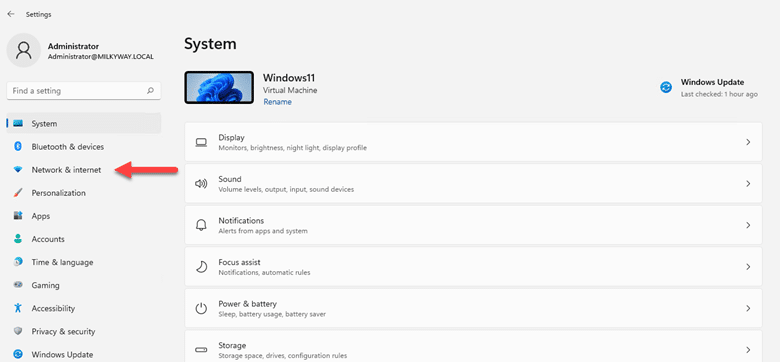
- Click on the type of connection you are using, Wi-Fi or Ethernet). In this example, we have “Ethernet”.
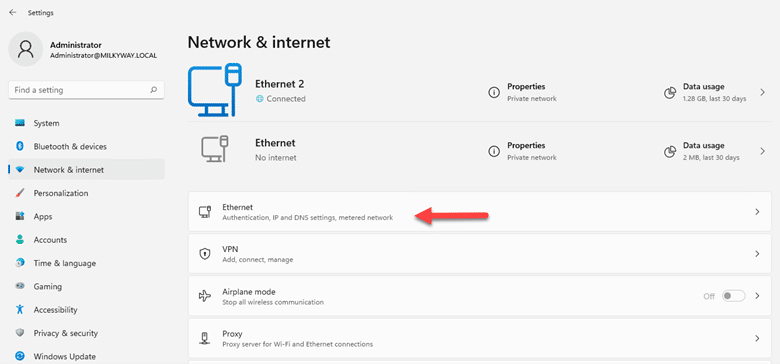
- In the network properties page, click on the “Edit” button for “DNS server assignment” section.
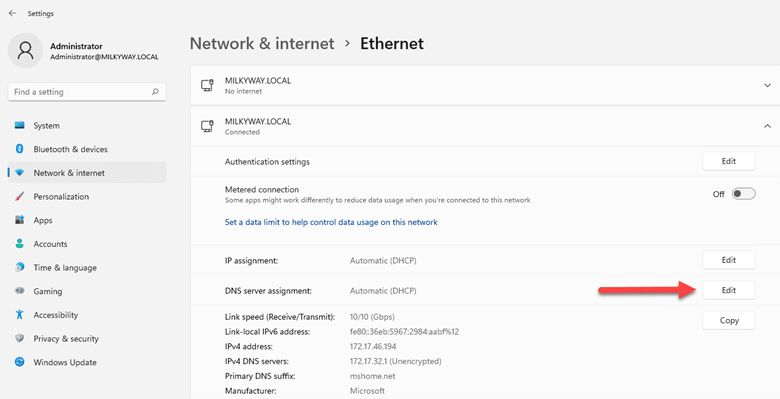
- Set the “Preferred DNS” and “Alternate DNS” addresses. You can use public DNS servers that support DoH. For example:
For Cloudflare: 1.1.1.1 (Preferred DNS) and 1.0.0.1 (Alternate DNS)
For Google: 8.8.8.8 (Preferred DNS) and 8.8.4.4 (Alternate DNS)
- Change the “Preferred DNS encryption” setting to “Encrypted only (DNS over HTTPS)” for “Preferred DNS” and “Alternate DNS” addresses.
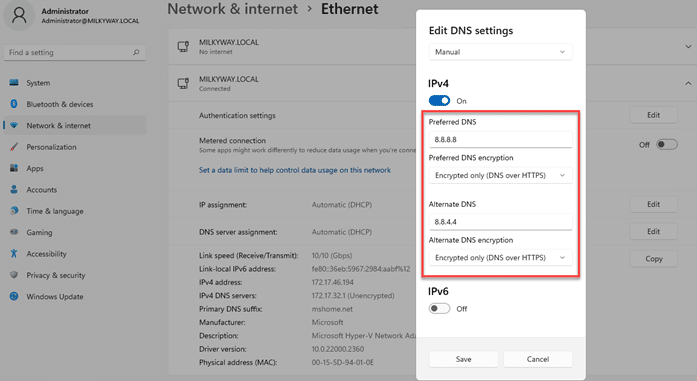
- Click the “Save” button to apply the settings.
How to enable DoH across a network using Group Policy
Changing DNS over HTTPS settings via Group Policy ensures that all network devices use DNS over HTTPS for their DNS queries.
- Press “Win + R” to open the Run dialog, type “gpmc.msc”, and hit Enter. Group Policy Management Console will be opened.
- Navigate to an existing GPO for which you want to enable setting, right-click on the GPO and choose “Edit”.
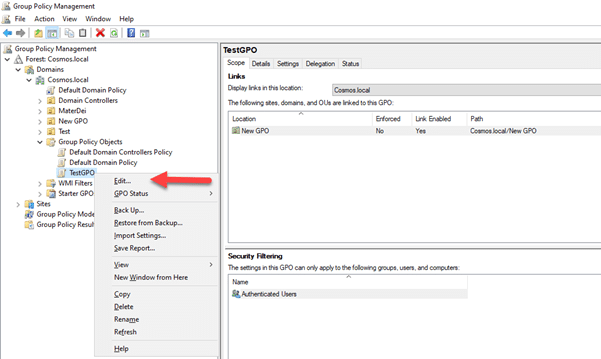
- In the Group Policy Management Editor, navigate to “Computer Configuration- Policies – Administrative Templates – Network – DNS Client.
- Locate the setting “Configure DNS over HTTPS (DoH) name resolution”, right-click on it, and select “Edit”.
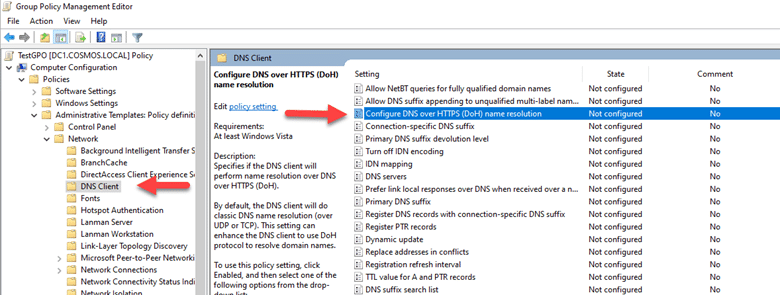
- Set the option to “Enabled” to activate DoH Policy, select “Allow DoH” from drop down in “Configure DoH options” section.
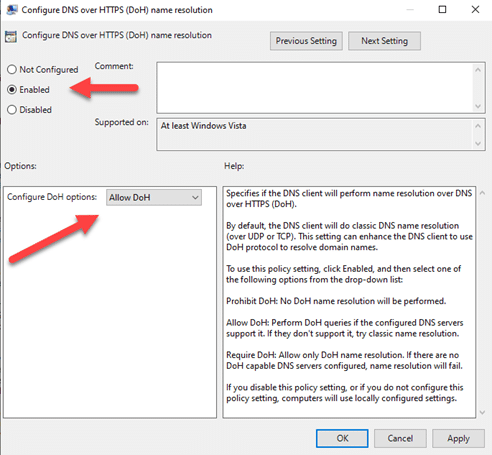
- Click “Apply” and then “OK” to save the changes. Close the Group Policy Management Editor.
- To ensure that the new settings are applied immediately, you need to force a Group Policy update on the client machines. This can be done by running the command “gpupdate /force” in the Command Prompt on each client machine, or by restarting the machines.
Enabling DoH in browsers
Google Chrome
- Open Chrome and click on the three dots in the upper right corner to access the menu.
- Go to “Settings” – “Privacy and security” – “Security”.
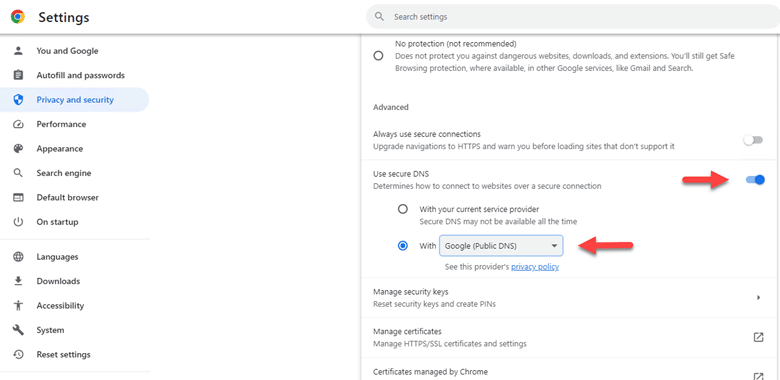
- Scroll down to “Advanced” and look for the “Use secure DNS” option.
- Turn on “Use secure DNS” by flipping the switch.
- You can choose to use the service provider chosen by Chrome or select a custom provider from the provided list.
Mozilla Firefox
- Open Firefox and click on the burger menu in the upper right corner, then select “Settings”.
- Click on the “Privacy & Security” setting on left side.
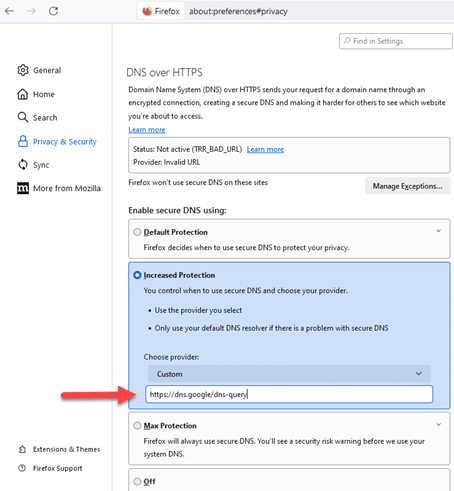
- Scroll down to the section “DNS over HTTPS”.
- Choose “Increased Protection” or “Max Protection”, according to your need.
- The dropdown to “Choose Provider” will be enabled, by default two providers “Cloudflare and NexDNS” are available in Firefox, but if you want to use any other e.g. Google DoH or Quad9 Doh servers, you can choose “Custom” and provide their DoH server URL in the box, as shown below.
Microsoft Edge
- Open Edge and click on the three dots in the top right corner to open the menu.
- Click on “Settings” then click on “Privacy, search, and services”.
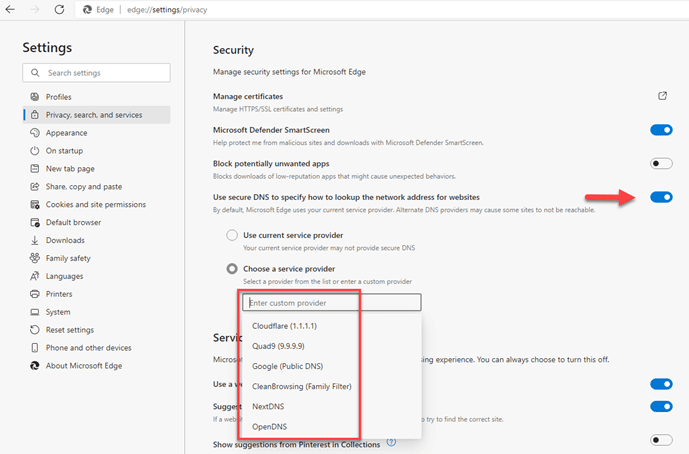
- Scroll down to the “Security” section.
- Find the “Use secure DNS to specify how to lookup the network address for websites” setting and turn it on.
- You have the option to use the provider selected by Edge or pick a custom provider by entering their details.
DNS over HTTPS (DoH) providers
Since the official release of DoH in October 2018, Several DNS providers offer secure and privacy-focused DNS over HTTPS services. These providers offer many features beyond encrypted DNS, such as content filtering, security from malicious websites, and enhanced privacy options. Below are some well-known DNS over HTTPS providers.
Cloudflare
Offers fast performance, strong privacy policies, no logging of user data, and support for DNS over TLS (DoT) as well.
Resolver Addresses:
- IPv4: 1.1.1.1 and 1.0.0.1
- IPv6: 2606:4700:4700::1111 and 2606:4700:4700::1001
- DoH URL: https://dns.cloudflare.com/dns-query
Provides high reliability and performance, integrates with Google’s security infrastructure, and supports DNS over TLS (DoT) as well.
Resolver Addresses:
- IPv4: 8.8.8.8 and 8.8.4.4
- IPv6: 2001:4860:4860::8888 and 2001:4860:4860::8844
- DoH URL: https://dns.google/dns-query
Quad9
Focus on security and privacy, blocks malicious domains, and supports DNS over TLS (DoT) as well.
Resolver Addresses:
- IPv4: 9.9.9.9 and 149.112.112.112
- IPv6: 2620:fe::fe and 2620:fe::9
- DoH URL: https://dns.quad9.net/dns-query
OpenDNS
Owned by Cisco, offers customizable security and filtering options, and integrates with Cisco’s security solutions.
Resolver Addresses
- IPv4: 208.67.222.222 and 208.67.220.220
- IPv6: 2620:119:35::35 and 2620:119:53::53
- DoH URL: https://dns.opendns.com/dns-query
CleanBrowsing
Specializes in filtering content and offers DoH for a safer browsing experience, particularly focused on protecting children online.
Resolver Addresses:
- IPv4: 185.228.168.168 and 185.228.169.169
- IPv6: 2a0d:2a00:1:: and 2a0d:2a00:2::
- DoH URL: https://doh.cleanbrowsing.org/dns-query
Potential conflicts of DoH with existing cybersecurity solutions
DNS over HTTPS deployment can create conflicts with existing cybersecurity solutions and practices. Understanding these potential conflicts can help organizations and individuals adapt their cybersecurity strategies to accommodate DoH effectively.
Network Monitoring and Visibility
Traditional cybersecurity tools often rely on the ability to monitor DNS traffic to detect and mitigate threats like malware, phishing, and data exfiltration. Since DoH encrypts DNS requests, it can reduce the visibility these tools have into DNS queries, potentially allowing malicious activities to go unnoticed.
Content Filtering and Blocking
Many organizations and network administrators use DNS-based filtering to block access to malicious, inappropriate, or non-compliant websites. With DoH, DNS queries are encrypted, potentially bypassing these content filters unless the filtering solutions are adapted to inspect and control HTTPS traffic or have endpoints configured to use specific, controlled DoH servers.
Data Loss Prevention
DLP systems monitor data movements to prevent sensitive information from leaving the secure network perimeter. These systems often analyze DNS queries for signs of data exfiltration. DoH can complicate this process by encrypting the queries, thus requiring DLP systems to adjust their monitoring strategies, possibly by decrypting DoH traffic at network boundaries, which might raise privacy concerns.
Regulatory Compliance
Organizations subject to regulatory requirements for logging and inspecting network traffic might find DoH challenging, as it encrypts DNS data that could otherwise be easily monitored for compliance purposes. Adapting to these changes while maintaining compliance might necessitate updates to network architecture and policies.
Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS)
IDS and IPS units scan network traffic for signs of suspicious activity. By encrypting DNS queries, DoH can limit these systems’ ability to analyze potentially malicious DNS requests or responses, thereby necessitating updates or reconfigurations to analyze HTTPS traffic or use alternative detection methods.
DNSSEC – validating the source of DNS data
DNSSEC is a set of security enhancements that allow the verification of the identity of root DNS server and authoritative DNS server during the process of DNS resolving. Next to other attacks, DNSSEC prevents attacks on DNS caches. As it does not encrypt the communication between a DNS client and a DNS server, it is an additional security aspect for the Domain Name System.
Conclusion
Online privacy and security are increasingly important. DNS over HTTPS encrypts DNS queries, enhancing user privacy and security. Although it faces challenges, it represents a significant shift in internet infrastructure and governance. As DoH gains traction, discussions about DNS encryption will continue to evolve, encouraging the development of new alternatives.
FAQs
What is DNS over HTTPS?
DNS over HTTPS is an improvement to tradition DNS, as traditional DNS sends plain text queries to DNS servers which can be intercepted by adversaries, but DNS over HTTPS sends the encrypted queries to supported DNS over HTTPS resolvers throughout the process.
Should I use DNS over HTTPS?
Yes, you should use DNS over HTTPS for protecting your online privacy and security, which is more important than ever. DoH encrypts the process of translating website names into IP addresses, making it harder for others to see which websites you visit and giving you more online privacy and security.
Is DNS over HTTPS enabled by default?
Whether DNS over HTTPS is enabled by default depends on the browser or operating system you are using. As of start of 2020, some browsers have started to enable DoH by default, while others require users to manually turn it on. For example, Mozilla Firefox and Google Chrome were one of the first major browsers to enable DoH by default for users in certain regions. Operating systems like Windows and MacOS have also been working on integrating DoH directly into the OS, which allows all DNS traffic to be encrypted, not just traffic from web browsers.
How do I check DNS over HTTPS settings?
Checking DNS over HTTPS settings varies depending on the browser or operating system you are using. For most browsers you can enable or look for these settings, by going into “browser settings – Privacy & Security” section, for windows operating systems you can check DoH settings by going into “Settings – Network & Internet – Properties” for your active network connection.
Do Windows 10 and Windows 11 support DNS over HTTPS?
Yes.



