This should be no revelation to IT professionals: you have to regularly monitor changes occurring in your network – and mainly for two reasons. The first one is this: continuous monitoring will take pain off meeting compliance requirements and surviving auditor’s visits. The second reason to implement a solution that keeps track of the changes is even more crucial due to the frequency of security incidents that we hear about at least once a week.
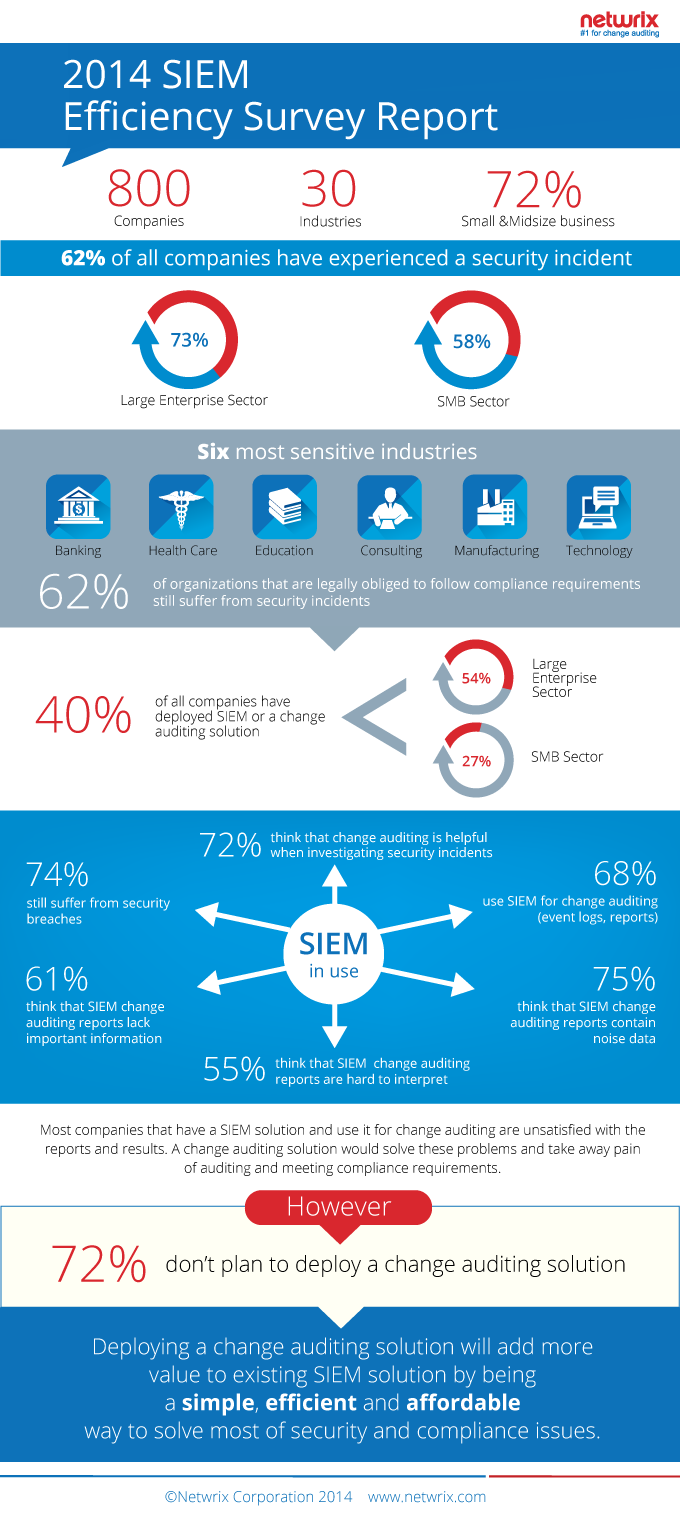
According to the latest 2014 SIEM Efficiency Survey Report, 74% of IT professionals who have deployed a SIEM (security information and event management) solution admitted that it hasn’t significantly reduced security incidents. Moreover, most of those who use a SIEM solution for change auditing purposes are unsatisfied with the reports quality. They are considered hard-to-read, lacking important data and containing lots of noise and gaps in the same time. This makes the task of knowing who changed what, when and where rather difficult.
Despite the rising trend of security breaches, less than a third of organizations plan to strengthen the security by enabling continuous auditing of their IT environments. However, the majority of companies that already use a change auditing solution find them helpful when investigating a security breach.
This infographic shows the main outcome of the Survey in simple numbers.