Departing employees can be a big source of data leakage for organizations; in fact, there are at least 5 reasons why departing employees can be a real pain. So we need to take a closer look into how to reduce this risk.
Of course, as soon as an employee leaves the company — whether because they quit or retired, were fired or laid off, or something else — you need to immediately deactivate all of the user’s accounts and terminate all access to corporate resources. But that’s not nearly enough. Weeks or months before the actual moment of termination, employees often know that they are planning to leave, or suspect that they are going to be fired or laid off. This gives them plenty of time to copy confidential information to take with them before you deactivate their accounts.
Fortunately, even in these scenarios, there are 5 key ways to reduce the risk of employee theft of confidential information on their way out. Every organization should consider making these best practices part of their security strategy.
1) Set up permissions properly
Because we don’t know who will turn out to be a rogue employee, it’s essential to establish and enforce the principle of least privilege: Grant each user access to only the systems and data they need to do their jobs, and nothing more. In particular, follow these best practices for configuring access lists on your file servers.
2) Monitor changes to permissions
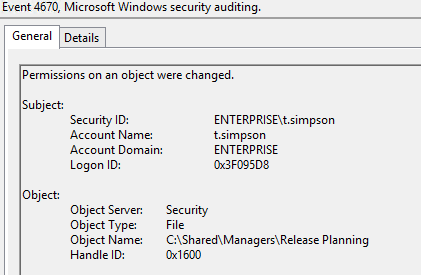
Once permissions are set up, we need to track and document all changes made to them. By making sure that all changes are authorized, we can reduce the risk of anyone getting access rights they don’t need, either accidentally or maliciously. Third-party solutions can automate change tracking, reporting and alerting, saving you time while reducing the risk of overlooking critical changes. If you use choose to native tools, the process is far more manual. For example, in order to spot changes to NTFS permissions, after you set up auditing on your file server, you need to track Event ID 4670:
3) Monitor the activity of privileged users when they are accessing critical files
The most efficient effective way to do this is with privileged user monitoring software, change auditing software or data leak protection (DLP) software. You can also use native tools, but they are not nearly as easy to configure and use.
For example, if you want to determine who read a certain file on your file share, you’ll need to take multiple steps:
a. Navigate to the required file share, right-click it and select “Properties”.
b. Select the “Security” tab ? Click the “Advanced” button ? Go to the “Auditing” tab ? Click the “Add” button.
c. Configure the following settings:
– Principal: “Everyone”; Type: “All”
– Applies to: “This folder, subfolders and files”
– Advanced Permissions: “List folder / read data”
d. Click “OK” three times.
e. Run gpmc.msc on your domain controller and create a new GPO.
f. Edit the new GPO: Go to Computer Policy | Computer Configuration | Windows Settings | Security Settings. Then do all of the following:
– Go to “Local Policies” ? Select “Audit Policy” ? Under “Audit object access”, check both the “Success” and “Failure” checkboxes.
– Go to “Advanced Audit Policy Configuration” ? Select “System Audit Policies” ? Select “Object Access” ? Under “Audit file system”, check both the “Success” and “Failure ” checkboxes.
– On the same screen, under “Audit handle manipulation”, check both the “Success” and “Failure” checkboxes.
g. Link the new GPO to the OU with your file servers and force Group Policy update by running the “gpupdate /force” command at the command prompt.
h. Open the Event Viewer and search the security log for event ID 4663 with the string “Accesses: ReadData (or ListDirectory)”:
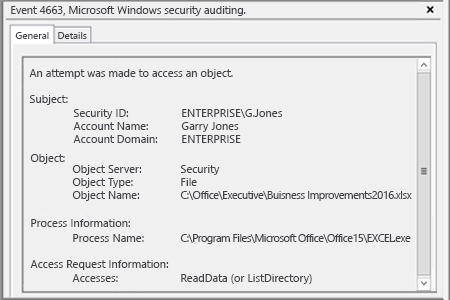
This could be also helpful when you need to restore critical data that was lost somehow.
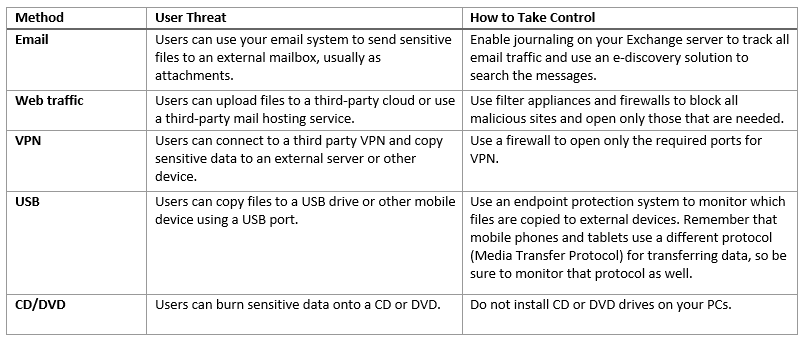
4) Take control over data leakage methods
Here are some of the most common ways employees transfer data out of your network, and what you can do in each case:
5) Encrypt data at the file system level
Encrypting the critical data on your file servers protects it, because even if a departing employee steals the data, they cannot read it except from your workplace. File system level encryption is offered by third-party vendors but it is usually not cheap, so the data you encrypt should be worth it.
Implementing these 5 key best practices will dramatically reduce the risk of data theft by departing employees. Of course, they could still manually copy information from the screen on to paper, take photos of individual screens, or steal your decryption key. But all of these options are more complicated and time-intensive than just copying or transferring files electronically.
Be aware that some of these 5 best practices are not cheap to implement and maintain, so be sure to carefully assess your risk and act accordingly, repeat the risk assessment and response process regularly, and make sure everyone follows user termination best practices scrupulously.



