The Obama administration’s “Cloud First Initiative” in 2011 gave federal and local agencies the green light to explore cloud services. Both Amazon Web Services and Microsoft Azure immediately provided special offerings targeted at governmental needs, and agencies have been quickly embracing them. According to Fortune, AWS GovCloud has been growing by 221% year over year since 2011, and Microsoft estimates that more than 10,000 U.S. government organizations already leverage Microsoft Cloud for Government services.
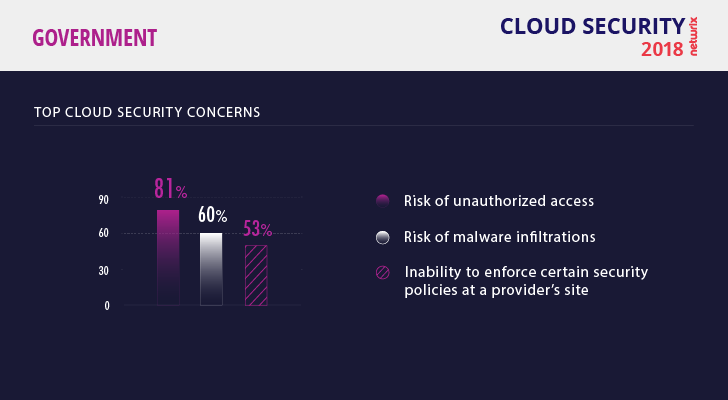
What are the top security concerns for data in the cloud?
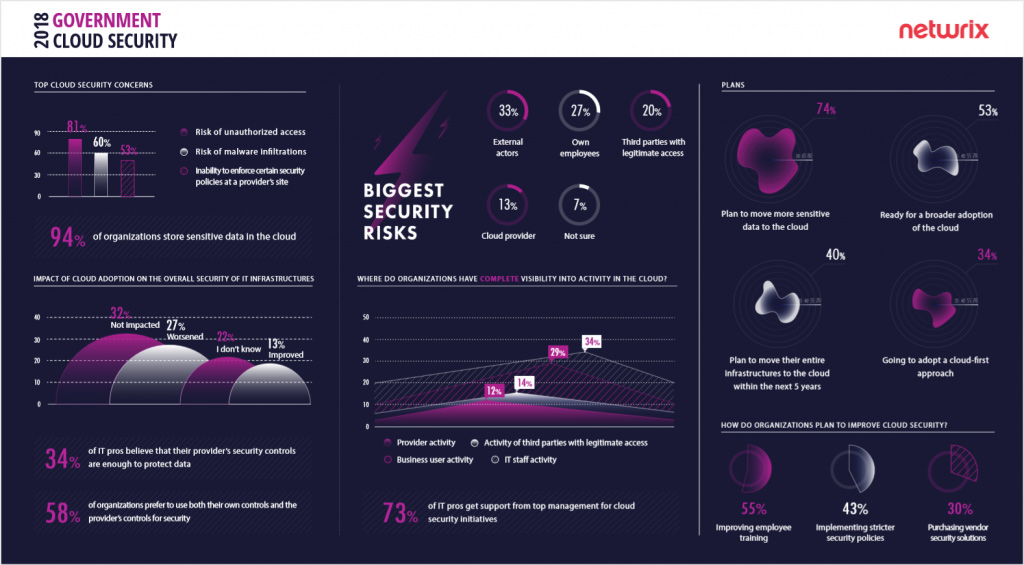
In fact, 94% government agencies surveyed in the Netwrix 2018 Cloud Security: In-Depth Report keep sensitive data in the cloud. But even though the CIA chose Amazon Web Services as a trusted provider in 2013, most government organizations are still uneasy about security in the cloud.
Their top concern, according to the survey, is the risk of unauthorized access. Malware comes in second, which is no surprise; the Petya and WannaCry attacks in 2017 have shaken up IT teams around the world. Although WannaCry didn’t affect many U.S. government agencies, the 2018 ransomware attack on Atlanta’s Department of Watershed Management was described by Reuters as “one of the most disruptive hacks ever to strike a U.S. local government.” More than half of all agencies would love to have more robust security settings and be able to enforce their security policies at the cloud provider’s site.
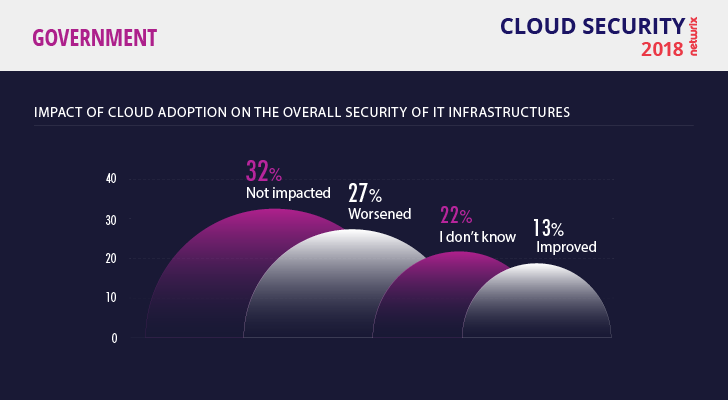
How has cloud adoption affected security?
Overall, only 13% of respondents think that their security has improved since cloud adoption, which is the lowest result across all industries surveyed. About a third (32%) say their security situation has not changed, and 27% say it has gotten worse. These results are surprising; it seems that no matter how many security services cloud providers offer (AWS, for example, has 17 security, identity, and compliance products available), government entities still feel insecure. To protect themselves, 58% of respondents choose to use their own security controls in addition to the ones offered by providers.
Are agencies concerned enough about the insider threat?
Not surprisingly, in this age of state-sponsored attacks and espionage, 33% of respondents name external actors as their main threat to data integrity. This number is identical to the result from the retail industry; both government secrets and credit card numbers will always be a target of attacks. Following hackers, respondents named their own employees and third parties as the most dangerous threat actors, showing that agencies are aware of the insider threat.
However, the insider threat really should move up in priority, since attackers often use compromised credentials.
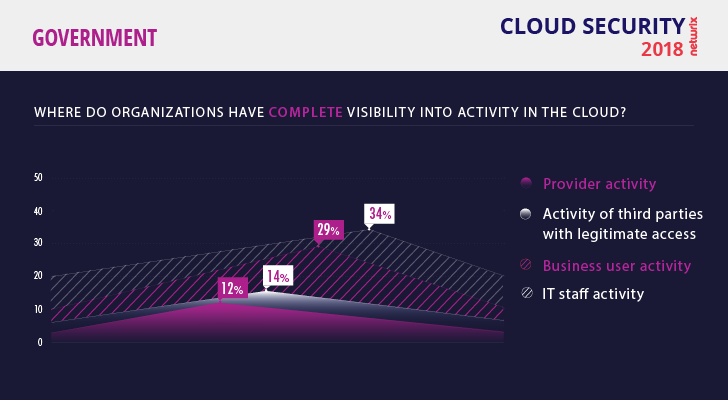
Few government agencies have visibility into the activity of IT staff (34%) and business users (29%). Control over user behavior is still not common
The recent Verizon Data Breach Investigations Report found that the public sector is the most vulnerable to social attacks, mostly phishing. Unfortunately, few respondents reported having complete visibility into the activity of their various internal actors, which is required to detect and block these types of attacks.
Are government agencies planning more cloud adoption?
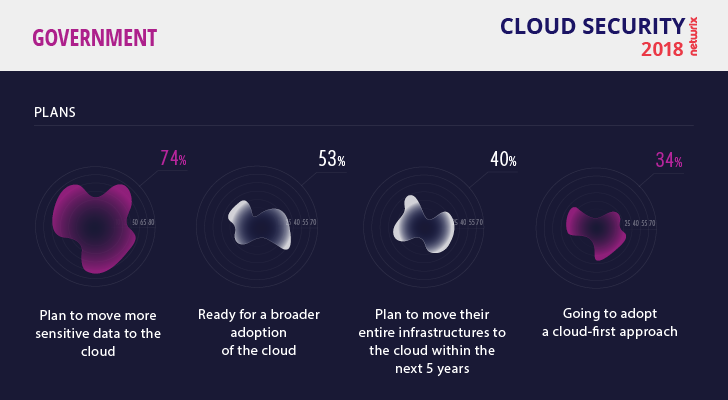
Cloud adoption by federal agencies is expected to remain solid, reaching nearly $3.3 billion in 2021, according to a recent IDC report. In fact, the goal of government services being 100% cloud-based could soon come true; more than half of respondents said they are ready for broader cloud adoption, including more advanced options than standard services like email and collaboration tools. 74% of agencies plan to move more sensitive data to the cloud, and 40% plan to migrate their entire IT infrastructure to the cloud within 5 years. But even though the Cloud-First Initiative was signed off on 7 years ago, only 34% of agencies are planning to implement a cloud-first approach.
How do agencies plan to improve security in the cloud?
Obama’s cloud-first speech stressed the importance of beating cyber threats that endanger national security. Now is an opportune time to act. More than 70% of respondents confirm that their senior management supports security initiatives in the cloud, which could lead to a sharper focus on cloud security and increased budgets to support it.
To improve cloud security, 55% of government agencies plan to increase employee training and 43% are going to update their security policies
Agencies’ specific plans for security improvement are very down to earth. To mitigate the insider threat, 55% of them plan to increase employee training, and 43% will tighten security policies.
But it’s not clear how security teams are going to measure the results, given their current lack of visibility into user activity. Without insight into who accesses sensitive data, it is hard to ensure that your employees are taking their lessons to heart and following security best practices.
Agencies also need to ensure that their IT teams are well trained and security oriented. The auditor’s report on the ransomware attack on the Department of Homeland Security found that poor training of IT personnel resulted in multiple failures that contributed to the incident; these failures included misconfiguration of settings, use of unsupported operating systems, poor patch management and insufficient planning for recovery from service disruptions. Note that this incident happened with an on-premises infrastructure; we can only imagine what might have happened if the DHS had been 100% cloud-based. Clearly, saving a little money by making do with inexperienced security professionals can actually be quite costly in the long run.
Conclusion
Different agencies have different goals in moving to the cloud. According to Gartner, “national governments see cloud as strategic IT modernization, whereas local and regional governments pursue the immediate tactical benefits of innovation and cost savings.”
No matter what your goals are or how far you have gone with the cloud, it is never too late to take steps to ensure you know exactly where all your sensitive data resides, who has access to it and who actually uses it. In fact, these steps are fundamental if you want to adopt a data-centric approach and mitigate data breach risks efficiently.
View the full infographics (click on the image to open a high resolution version in a new tab)