This is our third annual IT Risks Report. Over the years, it has changed significantly. The first surveys explored how organizations tackle IT risks related to security, compliance and operations and the resulting reports revealed that these risks are closely connected. This year, we decided to dive deeper into six IT risks that concern many IT professionals. We asked 1,558 organizations of various sizes, regions and verticals to evaluate their threat landscape and share what they do to minimize these six risks. Here is a summary of the results.
IT Risks
Physical Damage
35% of organizations name hackers as the top threat to their hardware assets, assuming they are responsible for most hardware and power failures. However, in 50% of cases, physical damage is actually the result of employee mistakes, negligence or bad luck. Companies are more likely to have an employee spill coffee on a computer than suffer physical damage from a hacker attack.
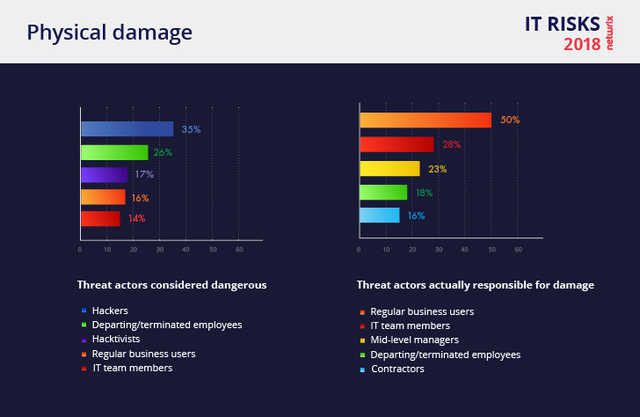
IT team members are second on the list of threat actors, at 28%. In most cases, physical damage they cause is the result of negligence resulting from work overload. This is a frequent situation, especially in the SMB sector: Small IT teams of 1 or 2 people wear too many hats and may sometimes forget to check if the server room is properly air-conditioned, for example.
Of course, there are ways to minimize the risk of hardware failures — you can keep an eye on hardware age and operating and storage conditions, for instance. Human errors are less preventable. According to the survey, 60% of companies plan to improve the detection and protection aspects of their security policies to mitigate this type of risk.
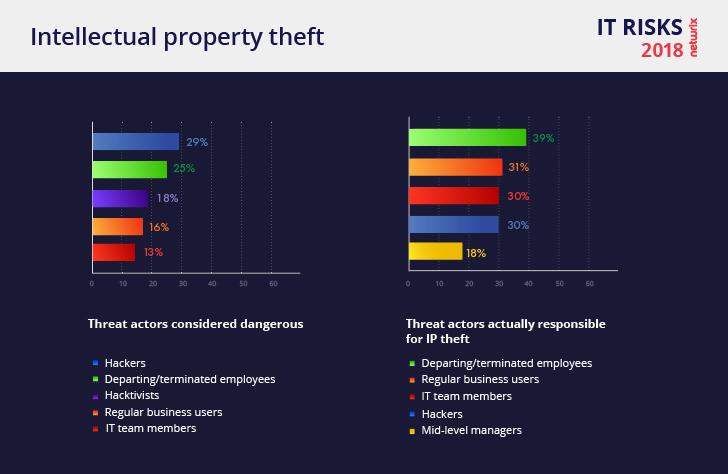
Intellectual Property Theft
Organizations name hackers (29%), human errors (22%), malware infiltrations (21%) and privilege abuse (15%) as the top risks in intellectual property theft scenarios. However, again we see a mismatch between the threat actors that organizations consider dangerous and those who are responsible for actual incidents: Respondents indicate that departing and terminated employees (39%) are actually most likely to steal blueprints, design files, technical documentation and other intellectual property. Regular business users also cause issues; the most common human errors include unintended disclosure and malware infiltrations that started with a user clicking on a malicious link.
Data Loss
Although organizations are most concerned about hackers, simple mistakes by regular business users, IT team members and mid-level managers account for 50% of data loss incidents and hardware failures accounted for 35%.
Quite expectedly, the area that most organizations would like to improve is protection. Unfortunately, you cannot reliably predict hardware failures or eliminate employee mistakes that lead to data loss. The best way to control this risk is to ensure you can identify what has been lost and restore it ASAP.
Although organizations are most concerned about hackers, simple mistakes by regular business users, IT team members and mid-level managers account for 50% of data loss incidents
Data Breach
In most cases, data breaches turn out to be the result of human errors, lack of security awareness and violations of security policy. Human errors (29%), phishing attacks (26%) and password sharing (23%) top the list. Hackers rarely perform targeted attacks because it is costly and requires time, skills and motivation. Instead, they smuggle in malware by tricking employees into opening malicious attachments in phishing emails, or take advantage of poor corporate practices like password sharing.
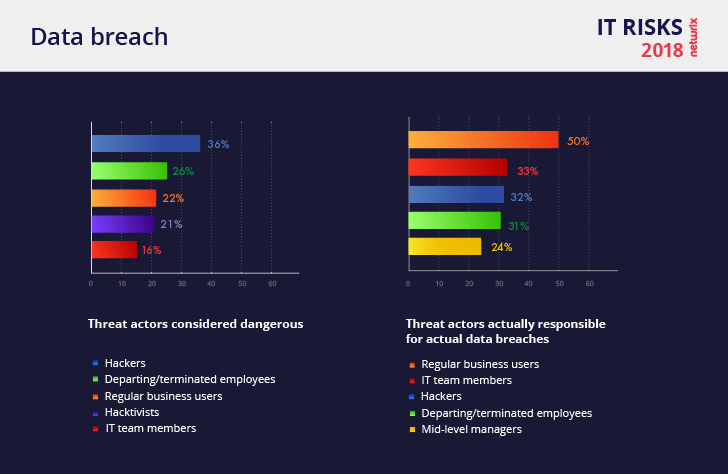
Half of data breaches involve activity by regular business users, followed by IT team members (33%) and mid-level managers (24%). This means that you need to make sure you have visibility into what users are doing and how they deal with sensitive data.
System Disruption
Most issues that can lead to system disruption are extremely hard to predict. Power outages (46%), human errors (43%) and ransomware (27%) are the leading causes of system disruption. One of every five organizations is concerned about cryptojacking — the unauthorized use of computer devices to mine cryptocurrency, but this type of attack is relatively new and has not caused many actual disruptions yet; neither did DDoS attacks (15%).
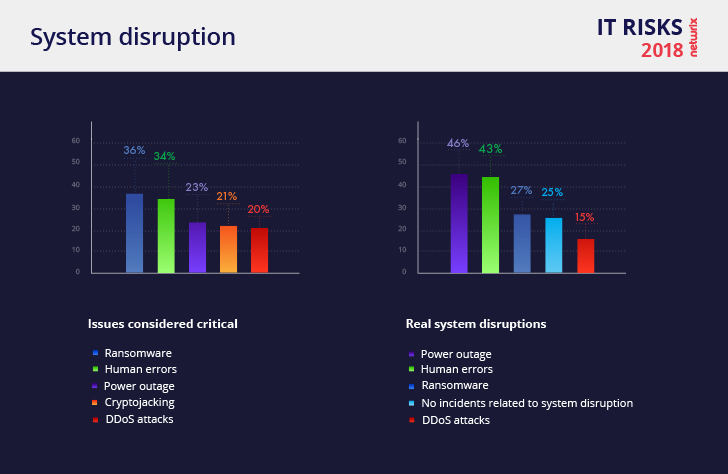
Instead, IT team members (41%) and regular business users (40%) caused the majority of disruptions. Unfortunately, due to negligence, work overload, lack of personnel or lack of security education, employees often make simple mistakes that lead to system outages. Hackers (33%) also represent a certain danger — they take advantage of human mistakes and leverage gaps in cyber security (e.g., system vulnerabilities and unpatched systems) to perform ransomware and DDoS attacks.
Compliance Penalties
Although compliance penalties are not exactly an IT risk, compliance with industry standards depends on fulfilling certain IT requirements. On average, organizations consider themselves as 60% ready for an unexpected compliance check. For smaller organizations (those with up to 500 employees), compliance is more of a challenge; one reason is that they cannot allocate budget for dedicated compliance person.
Unlike with the other IT risks we asked about, where organizations focused mainly on protective measures, when it comes to the risk of compliance penalties, 63% of organizations recognize the need to improve their ability to identify security risks that could lead to compliance failures. This means that organizations do not yet fully understand the goals and requirements of compliance standards, which makes it difficult for them to prioritize their security efforts.
Security Basics
Security Controls
To combat IT risks, you need to understand what risks pose the biggest threat to the business and be able to prioritize your security efforts to ensure that you use your resources to maximum effect. Security best practices are a huge part of any security strategy, but, unfortunately, most of organizations are failing to implement them properly. The main issue here is giving preference to a few security controls and neglecting others. Around 60% of respondents patch software and update user passwords once a quarter. But 20% of organizations rarely or never get rid of stale and unnecessary data or classify the data they store. Organizations also fail to control shadow IT — only 21% review the software that employees use on quarterly basis.
Visibility
Despite their lack of insight into data and applications, over 60% of organizations think that their level of visibility into user activity is high enough. Unfortunately, this is a false sense of security.
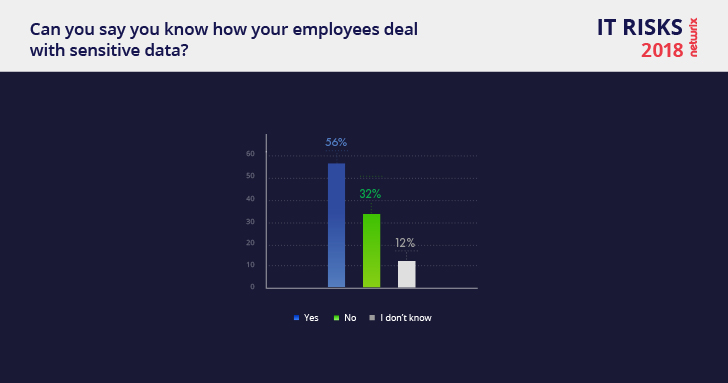
44% of organizations either do not know or are unsure of what their employees are doing with sensitive data
Almost half of respondents (44%) either do not know or are unsure of what their employees are doing with sensitive data and have very little control over the unauthorized activity of employees.
Risk Assessment
The good news is that 70% of companies have done IT risk assessment. The bad news is that only 33% do it regularly. Risk assessment procedures can vary.
Although 70% of companies have done IT risk assessment at least once, only 33% re-evaluate their IT risks regularly
For example, an IT company with a lot of intellectual property, a financial organization and a healthcare provider will have different priorities and will conduct risk assessment differently. Both the threat landscape and your IT environment are constantly evolving, so you have to do risk assessment at least once a year to fully understand which security areas need the most attention.
Incident Response Plan
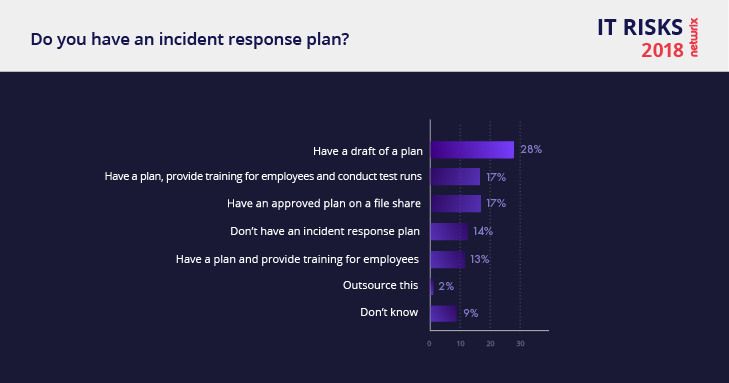
Remediation is something that was widely discussed during the last couple of IT conferences I attended. Unfortunately, the report shows that only 17% of organizations have an actionable incident response plan. The rest either have a draft of a plan, have a plan but do not communicate it well, or have no plan at all, which means that they cannot respond promptly when a security incident occurs and minimize the damage.
Key Takeaways
1. Reality rarely match expectations.
Organizations think they are targeted by hackers, but real-life incidents show that privileged users are much more dangerous. Even if hackers target your company with malware, it is your employees who open the door and let them in by opening a malicious attachment or clicking on a duplicitous link. The same mismatch works for visibility into the IT environment: Companies say they have enough visibility into users and data, yet they still admit they struggle to know how their employees are interacting with sensitive files.
2. Human errors lead to more incidents than malicious actions.
Most security incidents associated with insider activity happen due to human mistakes rather than malicious intent. Security incidents happen mostly because people forget to lock their computers, fall for phishing emails, or download sensitive data to a flash drive so they can work from home on the weekend.
3. Security basics are still neglected.
Many organizations fail to faithfully follow the security best practices recommended by security professionals. By ignoring these simple and relatively cheap best practices, organizations do themselves a disservice, as they remain in the dark regarding vulnerabilities and critical cyber threats.