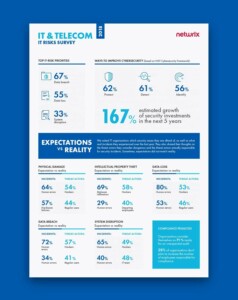
In this blog post, the fourth in our series about common IT risks for major industry sectors, we will focus on organizations in the telecommunications, technology and internet sector. We have extracted data from 2018 IT Risks Survey to find out about their biggest concerns associated with six IT risks: physical damage, intellectual property theft, data loss, data breaches, system disruption and compliance penalties. Practice shows that organizations do not always deal with these IT risks effectively because their expectations towards most dangerous security issues or threat actors do not always match reality. Someone who you trust most may become responsible for a security incident, or you might be hit by issues that you didn’t consider critical.
We polled 140 organizations from this sector to find out whether their expectations towards the most dangerous cyber threats and threat actors coincide with reality. We will illustrate the survey findings with some real cases from IT industry practice.
Physical damage
Physical damage is any harm to an organization’s hardware assets, e.g., servers, laptops or network devices, caused by improper storage environment, inadequate hardware maintenance, natural disasters and other factors. IT companies store a lot of sensitive data, including customer data and extremely valuable intellectual property, so they often invest heavily in the security of their physical assets. This is not a surprise, since the consequences of physical damage for IT companies can be severe. Hardware manufacturers can face production shutdowns, which will make them spend time and money on restoring the equipment, while web services providers and telecoms will be unable to deliver services to their clients. And any IT company that suffers loss of customer data entrusted to them can face reputational damage and huge financial losses due to system downtime.
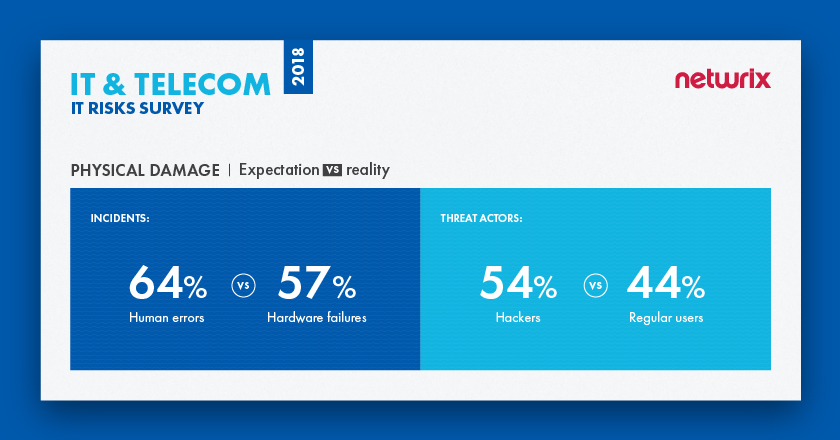
The survey results indicate that organizations are most afraid of human errors, while in reality the most common cause of physical damage is hardware failures, with 57% of respondents experiencing failures that led to physical damage of equipment during the last year. Human errors were third among the incidents that organizations experienced over the year (39%). In terms of threat actors, organizations are not always right about who represents the biggest danger. While the majority assume it’s hackers, in reality, regular users were responsible for the most physical damage incidents in the past year (44%). Only about 11% of respondents mentioned that hackers were involved in these types of incidents, putting them fifth among most dangerous threat actors.
Case study: Thieves steal equipment from Verizon Data Center.
In 2007, thieves stole more than $4 million in IT equipment from a Verizon Business data center. According to a statement by the London Metropolitan Police, three to five male suspects dressed as police officers gained entry to the property by convincing guards that they were investigating reports of people on the roof of the building. The culprits tied up the guards before stealing the company’s hardware, including high-value circuit boards.
A spokesperson from Verizon said that the company had experienced a “service interruption” due to the incident. Despite the loss of high-value equipment, Verizon staff claims that none of company’s sensitive information was stolen.
Intellectual property theft
In the world of IT, we mostly talk about three types of intellectual property (IP): copyrights, trade secrets and patents. Examples include source code, object code, user interfaces, software architectures, proprietary algorithms and other valuable data.
Intellectual property is perhaps the most valuable asset of any IT company, since it defines their business development and competitive advantage. For this reason, IP theft — whether driven by competition between corporations or undertaken by hackers and malicious insiders — is one of the most critical IT risks for this industry. If a company becomes a victim of intellectual property theft, the consequences can be catastrophic: The company can lose its competitive edge, experience a slowdown in business growth, lose market share, become the subject of expensive and exhausting litigation, and lose time and money trying to fix the damage and figure out their next steps.
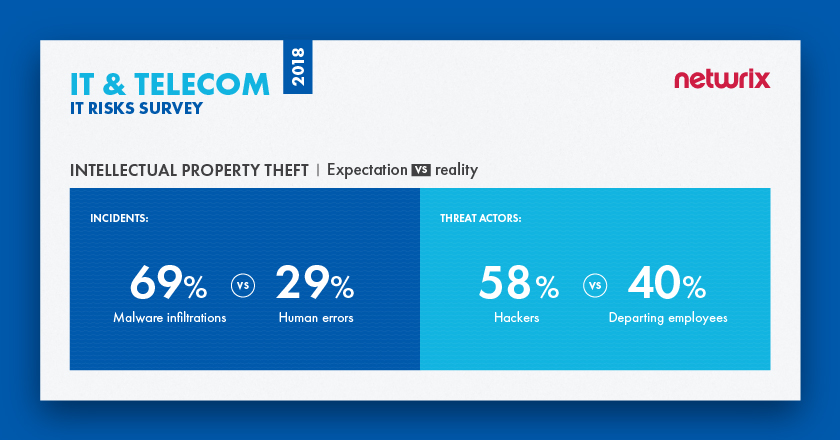
Vast majority of IT organizations (69%) think that malware infiltrations pose the biggest threat to their intellectual property. In reality, human errors caused the most security incidents (29%)
According to the survey results, IT organizations think that malware infiltrations pose the biggest threat to their IP. In reality, human errors caused the most security incidents (29%), with malware infiltrations placing second at 14%. Companies’ expectations towards threat actors also don’t match reality. More than half of respondents (58%) said that they are most afraid of hackers, but departing employees were responsible for the most security incidents (40%). Hackers took second place, accounting for 36% of incidents.
Case study: Former Apple employee accused of stealing trade secrets.
In 2018, former Apple employee Xiaolang Zhang was arrested on charges of theft of a company’s trade secrets. Zhang was hired in 2015 to work on Apple’s self-driving car project. His work involved designing and testing circuit boards that would analyze sensor data. In 2018, he informed Apple that he was quitting his job and going to China to work for an autonomous vehicle startup called XMotors. Later, Apple discovered that Zhang had downloaded blueprints related to self-driving cars to his laptop and taken circuit boards and a Linux server from one of its hardware labs.
The case is now under investigation. XMotors said it is “highly concerned” but claims that there is no indication that Zhangever communicated any of Apple’s sensitive information to XMotors.
Data loss
If IT companies permanently lose sensitive data, which includes the personal and financial data of their customers (e.g., usernames, passwords, dates of birth, billing details etc.) and intellectual property (e.g., blueprints and source code), they will have to spend time and resources trying to recover the data and inevitably face reputational damage. Also, they may experience system disruptions and face lawsuits from enraged customers.
Organizations know exactly which security issue leads to most cases of data loss —human errors. However, many of them (53%) delude themselves, thinking that hackers are the most dangerous threat. The reality is, regular users are behind the most data loss incidents (46%), with hackers placing third (33%).

Case study: A startup is in crisis mode because an employee deleted the wrong files.
In 2017, code management startup GitLab suffered a major backup failure due to an employee’s mistake. GitLab’s system administrator tried to fix a slowdown on the site by clearing out the backup database and restarting the copying process. But he accidentally specified the name of the primary database instead, starting a wipe of 300GB of live production data that was due to be replicated; just 4.5GB remained by the time he canceled the command. The site had to be taken down for emergency maintenance for six hours, during which the team discovered that none of their five backup routines was working correctly. As a result, the company suffered permanent loss of six hours of production database data.
GitLab made the incident public and kept the GitLab community informed about the progress of the issue resolution via tweets, blogs and even a live-stream YouTube channel (now offline). GitLab assured its users that the lost data didn’t actually contain anyone’s code; it was just specific types of metadata such as comments. Despite its transparency throughout the incident, Gitlab still faced reputational damage and was criticized for ignoring best practices and not testing its backups.
Data breaches
Data breaches are not as frequent in the IT sector as in other sectors (e.g., healthcare). However, if a data breach hits an IT company, especially one focused on end users, it hits them hard. According to the Verizon 2018 Data Breach Investigations Report, hackers and malicious insiders attack IT companies mainly for financial gain or espionage. The most frequent types of data compromised are personal data and credentials, which is not a surprise, since many IT companies store and process large volumes of customer information, like emails, dates of birth, usernames and passwords, as well as more specific types of data (e.g., social networks, photographs and location information). Hackers can sell this data on a black market or use it in phishing attacks and fraud schemes.
The consequences of a data breach in the IT sector can be severe. First are the fines and legal actions for non-compliance — just remember how in 2018, Facebook CEO Mark Zuckerberg had to testify to the U.S. Senate about possible data misuse. Other consequences involve reputational scandals, loss of market share and other financial damage; for instance, the notorious Yahoo breach impacted Verizon’s 2016 plans to acquire the company, leading to the $4.8 billion deal price being cut by $350 million.
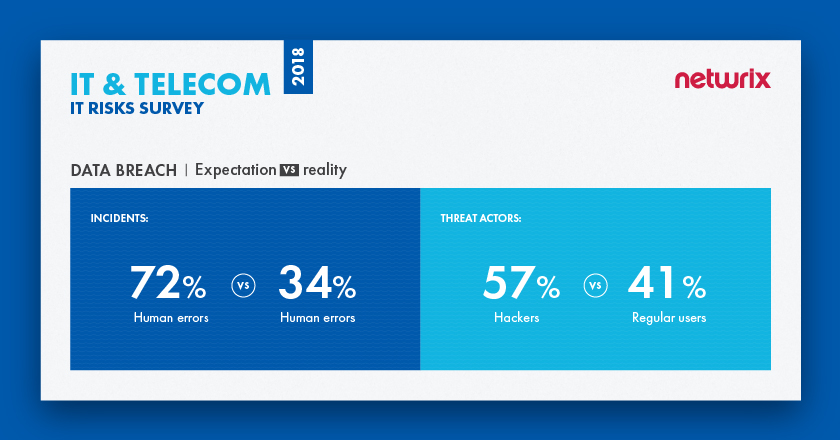
72% of IT and Telecom organizations consider human factor as the most significant threat to their systems and data
Our research shows that the vast majority of IT organizations are aware that human factor poses the most significant threat to their systems and data: 72% said this is the most dangerous threat pattern, and 34% said it had led to real data breaches. However, IT companies blame hackers for data breaches, while in fact regular users are involved in the most incidents (41%). Hackers are second biggest threat actor, responsible for 39% of data breaches suffered by respondents during the past year.
Case study: eBay suffers a large data breach due to compromised employee credentials.
In 2014, online auction site and global retailer eBay became a victim of a huge cyberattack that compromised its main database. Hackers compromises a small number of employee log-in credentials, giving them access to eBay’s corporate network. According to a eBay spokesperson, the hackers stole 145 million records, which contained passwords, email addresses, birth dates, mailing addresses and other personal information, but not financial data such as credit card numbers.
Although the database was compromised between late February and early March 2014, the incident was not discovered and reported until May 2014. The company was largely criticized for the way it responded to the breach and for being slow to inform customers about the theft of their personal data. In July 2014, CEO John Donahoe admitted that the breach and the following company-wide password reset affected eBay’s commerce volume: Due to a reduced level of traffic, the company’s revenue growth slowed to 6% in Q3 2014, as compared to 11% and 9% growth in the past two quarters of 2014. Looking ahead, the company lowered its revenue guidance for the second half of fiscal year 2014 by around $300 million.
System disruption
A system disruption (or service interruption) is the inability of IT systems to perform their primary function for a certain period of time. Common causes of system disruption include power outages, malicious incidents caused by insiders and outsiders (including sabotage, DDoS attacks and ransomware), and human mistakes.
The severity of this risk for an IT company depends on the company’s specifics. For example, cloud companies, web service providers and telecom companies will be in real trouble if system disruption occurs, since if services are unavailable, they cannot fulfill their obligations to customers, which leads to financial and reputational damage and loss of loyal clients.
Most survey respondents (65%) said that human errors are most critical security issue. Indeed, human errors caused 40% of downtime incidents over the last year. However, organizations are not as savvy about threat actors: Organizations think that hackers are their biggest threat, while in reality the main threat actors are IT team members. 48% of organizations said that their own IT team members were involved in incidents that led to system disruption. Nevertheless, hackers are still a major threat, taking second place by accounting for 41% of real incidents.

Case study: Amazon’s web servers went down due to human error.
Amazon’s web hosting services are among the most widely used, which means that if Amazon’s servers go down, a lot of things go down with them. This is what happened in 2017 with Amazon’s Simple Storage Service (S3), when an Amazon employee was debugging an issue with the billing system and accidentally took more servers offline than intended. That error started a domino effect, taking down multiple websites that store content and run services with Amazon S3. Up to 150,000 sites — belonging to Apple, Adobe, Expedia, Freshdesk, Kickstarter, Mailchimp, Slack, Twillio and more — were affected to some degree. Not only did this impact the companies directly, it also caused problems for the millions of small businesses that rely on these sites for their day-to-day operations.
The outage lasted roughly five hours. Days after all services were restored, Amazon offered a detailed explanation about why its S3 cloud storage service went down. The company said it was making some changes to ensure that a similar human error in the future wouldn’t have as large an impact. This massive outage raised discussion about centralization of internet infrastructure; some analysts even concluded that AWS should be regulated as a monopoly.
Compliance penalties
While organizations from strictly regulated sectors like healthcare and finance have to comply with specific industry standards like HIPAA and GLBA, in the IT industry, the situation is slightly different, since there are no standards that specific to this sector. However, IT companies store large volumes of sensitive data, so their compliance routine depends on the types of data they store and process. Companies that process payment data (e.g., online auction site like eBay) have to comply with PCI DSS, and public companies like Google have to comply with SOX. In addition, IT companies that process the personal information of customers must comply with a growing number of data privacy regulations, such as the GDPR and the upcoming CCPA and PIPEDA. Finally, voluntarily adopting some of the many best-practice standards and frameworks available, such as COBIT, SOC 2 and ISO 27001, will improve IT governance practices and enhance a company’s credibility.
Inability to meet the requirements of mandatory standards can result in reputational scandals, legal actions and huge fines. For example, the maximum penalty for non-compliance with GDPR is 20 million euros or 4% of global annual turnover, whichever is higher.
According to Netwrix’s survey, IT organizations consider themselves 71% ready for unexpected compliance checks, which is above the average (66%) for all industries; in fact, IT was second only to the healthcare industry, where 74% say they are ready for an unexpected audit. 28% of IT organizations don’t plan to increase the number of employees responsible for compliance at all.

Case study: Major IT companies are targets of first official complaints for GDPR non-compliance.
On the first day of GDPR enforcement in May 2018, Facebook and Google were hit with a raft of lawsuits that accused the companies of forcing users into sharing their personal data. The 3.9-billion-euro suit against Facebook and 3.7-billion-euro suit against Google were filed by pro-privacy advocate Max Schrems on behalf of unnamed users of Facebook, WhatsApp, Instagram and Google’s Android operating system.
According to Schrems, the companies have forced its users into agreeing to new terms of service in breach of the GDPR requirement that such consent should be freely given: “Facebook has even blocked accounts of users who have not given consent. In the end, users only had the choice to delete the account or hit the agree button.”
Both companies have disputed the charges, arguing that existing measures were adequate to meet GDPR requirements. Both cases are now under investigation. If the allegations prove true, Google and Facebook face fines of as much as four percent of their global revenues for the preceding fiscal year.
Summary
The survey results reveal that organizations from the IT and telecom industry are usually savvy about identifying threat patterns that represent the biggest danger to their systems and data. They understand that the human factor is the leading root cause of most incidents. However, just like other industries, they are often mistaken about the real threat actors. For every IT risk, they blame hackers, while in reality their own business users and members of IT team are responsible for most incidents.
Protection against data breaches is the top IT risk priority for the majority of IT organizations (67%). This is not a surprise, since these organizations store and process the sensitive data of their customers and face serious consequences if it is compromised. According to Ponemon’s 2018 Cost of Data Breach Study, the technology industry is fifth per capita cost of data breaches ($170 per each lost or stolen record), and the average total cost of a data breach is $3.86 million.
Headlines about IT organizations that have suffered data breaches and the natural desire to protect themselves against IT risks more effectively might be key reasons why IT organizations plan to increase their security investments by 167 % in the next 5 years — the biggest result among all industries — and consider protection against external and internal threats as the key way to improve cybersecurity.