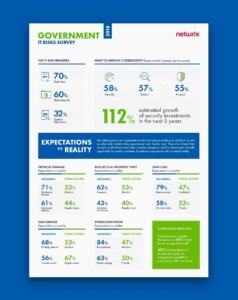
We have used the data from 2018 IT Risks Survey to dive deeper into the problems facing federal, state and local government organizations. The survey covers the six most common types of IT risks: physical damage, intellectual property theft, data loss, data breaches, system disruption and compliance penalties. Not all government organizations deal with these risks effectively; in particular, sometimes they are afraid of certain security issues while in reality they experience completely different incidents. The same is true for threat actors — the people you consider most dangerous are not necessarily the ones who take part in real security incidents.
We surveyed 109 government organizations to find out whether their expectations about the most dangerous cyber threats and threat actors match the reality. The figures below reveal real difficulties that government organizations face on their way to data security, but to bring them to life, we also provide some real-life examples.
Physical damage
Physical security is one of the key components of data protection. Physical damage is any harm to an organization’s hardware assets, e.g., servers, laptops and network devices. In government organizations, issues that can lead to physical damage include an improper storage environment, natural disasters, careless handling or inadequate hardware maintenance.
Physical damage is extremely dangerous for government organizations that are connected with defense; the most common scenarios include damage to critical equipment (e.g., high-tech weapons and command and control systems), as well as hacking that makes these physical assets useless. Physical damage is also harmful for state and local agencies, whose can lose data permanently and suffer long service disruptions.
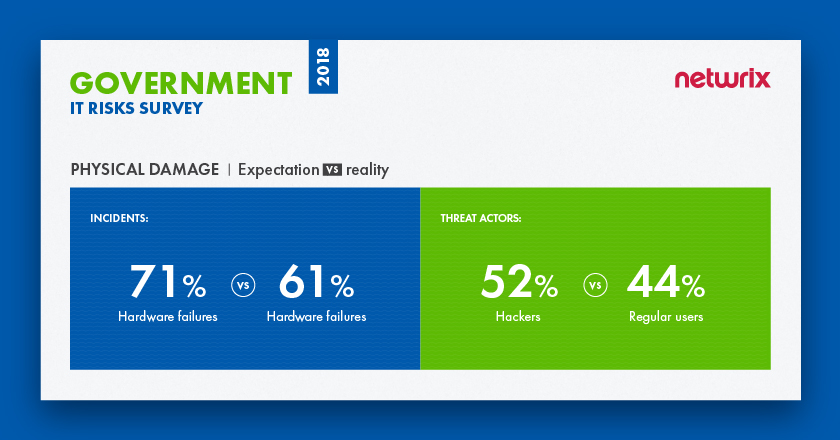
The survey findings reveal that organizations are pretty aware of what they need to be afraid of in this area. The majority of respondents said that they were concerned about hardware failures, and this was in fact the leading cause of physical damage during the past year. However, organizations are not as savvy about threat actors: 52% of respondents named hackers as their biggest threat, while in reality it’s regular business users who cause most physical damage (44%); only 4% named hackers as main actor in the real incidents, the lowest result among all threat actors.
Case study: E-Government system goes down after leak
In 2012, the Bahamas Public Treasury reported that its computer systems went offline after a water leak damaged server equipment operating its e-government services. State Minister for Finance Michael Halkitis confirmed that there was a leak in the Treasury’s building on the third floor, which affected the second floor where the servers were housed. Due to the water damage to equipment, the entire IT environment was disrupted for several days. While there is no evidence of data loss and systems were eventually repaired and restored, no online functions were available for a while, which significantly impacted the routine operations of the Public Treasury.
Intellectual property theft
Intellectual property theft usually involves robbing people or companies of their ideas and inventions. This intellectual property can include everything from trade secrets and proprietary products to software, contracts, grants and agreements. Intellectual property theft might not seem to be relevant to government agencies. However, it can be a very dangerous IT risk for public sector organizations and their contractors that work on extremely important research, particularly in the aircraft manufacturing, IT telecommunications and energy industries. In these cases, intellectual property theft can result in reputational damage, loss of competitive advantage and financial expenses.
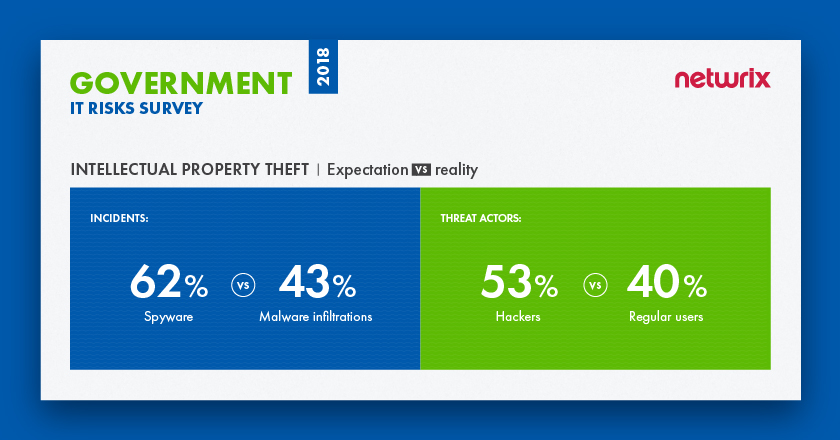
Unfortunately, government organizations seem to be completely unaware of what actually poses threat to their intellectual property. While they are mostly afraid of spyware, they actually experience a much wider specter of threats. Malware infiltrations accounted for 43% of incidents, but spyware specifically was named by only 24% of respondents, placing it fifth among all real incidents. In terms of threat actors, we also see a mismatch between expectations and reality. Most organizations blame hackers for loss of intellectual property, while in fact they are the second biggest threat after regular users, who were the top cause of security incidents (40%).
Case study: U.S. government accuses Chinese hackers of stealing jet engine intellectual property
In 2018, the U.S. Justice Department charged ten Chinese nationals of stealing intellectual property from a pair of unnamed U.S. and French companies in early 2015. According to the complaint, the culprits used a combination of phishing schemes, malware, domain hijacking and other techniques to intrude into a French aerospace company that was developing the engines with a U.S. company. The suspects also allegedly hacked into aerospace companies in Massachusetts, Oregon and Arizona that manufactured engine parts. The malware that hit one French company’s office was the Sakula malware, which was also used in the Anthem, OPM and other attacks.
The reason behind this alleged hack was simple: A Chinese state-owned aerospace company was also working to develop a similar type of engine for use in commercial aircraft. Prosecutors say that the attack was planned by two Jiangsu Province Ministry of State Security (JSSD) officers, working together with six hackers and two insiders at the French aerospace manufacturer’s office. The case is still under investigation; however, in October 2018, the Justice Department announced that JSSD officers had been extradited to Ohio on charges of stealing trade secrets.
Data loss
Data loss occurs when information is destroyed by failures during storage, processing or transmission. This IT risk involves intentional damage (e.g., erasure, session hijacking, malware infiltrations and IoT exploits), as well as human mistakes and software failures. The consequences of data loss for government organizations include service disruptions for employees and the public, and lawsuits from citizens or employees whose data is endangered. If the sensitive data of citizens and employees goes missing (this includes personal, financial information or any other data that is regulated by compliance standards), it can potentially get into the wrong hands and be used for phishing attacks, blackmail or fraud.
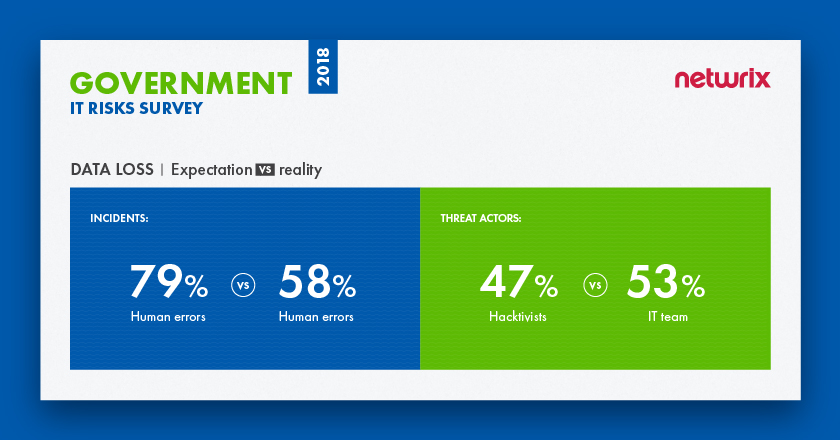
For 70% of government entities data loss is the top priority among IT risks
According to our research, the majority (70%) of respondents said that data loss is their top priority among IT risks. Government organizations correctly consider human errors as the leading root cause of data loss. Unfortunately, their expectations about threat actors are far from accurate. They think hacktivists are the most dangerous threat actors (47%), while in reality the top threat actor is someone you trust the most — an IT team member (53%). Hacktivists are not even in the top five of the most dangerous threat actors; they were mentioned by only 11% of respondents.
Case study: Veterans Affairs loses data due to unencrypted hard drive
In 2006, a data analyst at the U.S. department of Veterans Affairs (VA) had his computer equipment stolen from his home in Maryland — and the hard drive contained unencrypted personal information on 26.5 million people, including veterans and service personnel. The stolen data included names, Social Security numbers, dates of birth and disability ratings.
The analyst reported the incident and eventually the stolen laptop and hard drive were recovered by police. The FBI performed a forensic examination on the computer equipment and reported that no data had been compromised. In 2009, the VA reached an agreement in a class-action lawsuit filed by five veterans who alleged invasion of privacy, agreeing to pay them $20 million for exposing them to the risk of identity theft.
Data breaches
A data breach is a confirmed security incident in which sensitive, protected or confidential data is copied, transmitted, viewed, stolen or used by an unauthorized individual. Threat patterns for this cyber risk involve various malicious techniques, from phishing and state-sponsored attacks to simple human mistakes, lost devices and misconfigured databases.
According to the Verizon 2018 DBIR, one third of all data breaches in the public sector happen due to privilege misuse and errors by insiders. Government organizations store information about both the citizens they serve and the citizens they employ; their personal information one of the top types of data lost in data breaches in the public sector, followed by secrets (e.g., data related to background checks) and medical records. For example, during the infamous breach at the Office of Personal Management (OPM), hackers gained access not only to personal records, but also to information regarding security clearance, which involved extremely confidential facts about current and former government employees. When such data ends up in the wrong hands, it can easily be used for extortion, fraud or blackmail or to harm someone’s reputation.
The consequences of breaches in the public sector involve the resignation of key people, lawsuits, fines, loss of trust from citizens and employees, reputational damage, and huge expenses for security investigations and remediation. In the long term, huge data breaches in the government sector can spur regulatory bodies to mandate new, stricter privacy regulations that could be extremely difficult to comply with and cause much inconvenience to government organizations.
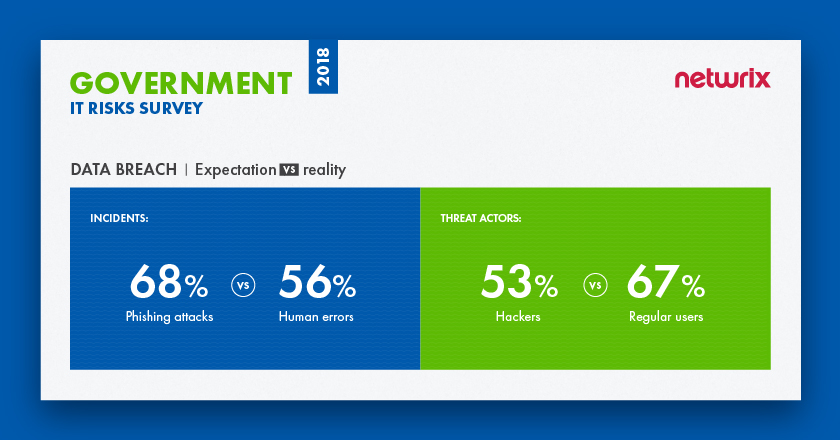
In government sector regular users are responsible for the most data breaches (67%)
According to the survey, data breaches seem to be a weak spot for public sector organizations. 68% of organizations say that phishing attacks are the threat pattern they need to be afraid of, while in reality 56% of organizations report that human mistakes are causing the most trouble; phishing attacks were in third place, experienced by just 39%. 53% said that they are afraid of hackers more than anyone else; however, none of the respondents mentioned hackers as the threat actors responsible for real incidents. In reality, regular users are responsible for the most data breaches (67%).
Case study: Office of Personal Management reports one of the largest breaches ever
In March 2014, the U.S. Office of Personal Management (OPM) informed government officials that Chinese hackers had infiltrated the OPM’s computer systems, presumably to collect information on federal employees. The data breach consisted of two separate but linked attacks which exposed over four million records for current and former government employees, including those at the Department of Defense. Overall, 21.5 million Americans were impacted by the breaches. The investigation revealed several flaws in the OPM’s cybersecurity strategy. First, the data was not protected by data masking, redaction or encryption. Second, the OPM failed to implement multi-factor authentication for all employees and contractors who log on to their network. Finally, they failed to prioritize funding for cyber security and struggled to meet many FISMA compliance requirements.
Although the investigation is not yet finished, it is clear that the damage to the government’s credibility far outweighs the impact on security. A federal employee union filed a class-action lawsuit claiming that the OPM’s negligence led to the breach. Also, in the aftermath of the event, both the director and the CIO of the OPM resigned.
System disruption
System disruption may not seem to be not as dangerous as other IT risks (e.g., data breaches), but the consequences for government organizations can be severe. A system disruption (or service interruption) is the inability of IT systems to perform their primary function for a period of time. Common causes of system disruption include power outages, natural disasters, malicious techniques used by insiders and outsiders (including sabotage, DDoS attacks, ransomware and other), and human negligence and mistakes. For government organizations, unplanned downtime means that they cannot function effectively, since they might not be able to schedule appointments, address citizens’ complaints or use their electronic records management (ERM) systems, frustrating employees and citizens alike.
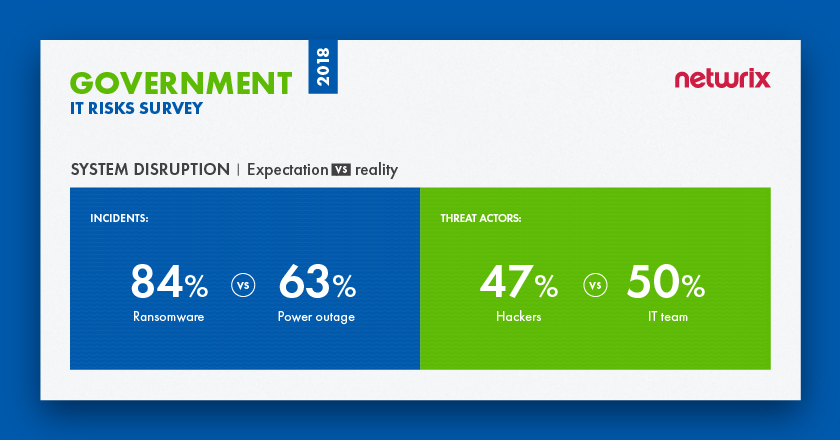
In terms of security incidents that lead to system disruption, organizations are most afraid of ransomware (84%) — this is quite expected, considering the damage that famous ransomware attacks like WannaCry have caused. Nevertheless, in reality, power outages are the most frequent issue (63%), with ransomware in second place (58%). Organizations think hackers are the most dangerous threat actor (47%), but this does not match reality either: IT team members are responsible for the most real incidents (50%), while hackers are in third place (28%).
In 2018, a power outage at the State Information Technology Agency (SITA) affected the systems of some government departments in South Africa, including the presidency. Initially, SITA CEO Dr. Setumo Mohapi said that the massive system disruption was caused by a power outage in the city of Tshwane. However, it was later found that SITA’s own backup generator failed, causing service delays countrywide.
As a result, all government operations were suspended and all critical data (e.g., birth, marriages, death, smart ID and passport services) was unavailable for several days. Making the situation even worse, another outage occurred shortly after systems were restored. Although SITA apologized to citizens and stakeholders for the system failure, SITA executives were widely criticized for lack of disaster recovery procedures and backup plans, which left them unable to respond promptly to the incidents.
Compliance penalties
Government organizations need to comply with a variety of laws and regulations; these include both government-oriented standards like FISMA, NIST 800-171 and CJIS, and more general standards like HIPAA and GDPR. Although compliance penalties are not exactly an IT risk, they are still a major concern for government organizations. Violations of some compliance standards (e.g., FISMA) can result in a reduction in federal funding or reputational damage, while failure to comply with stricter standards can also lead to prosecution and significant fines.
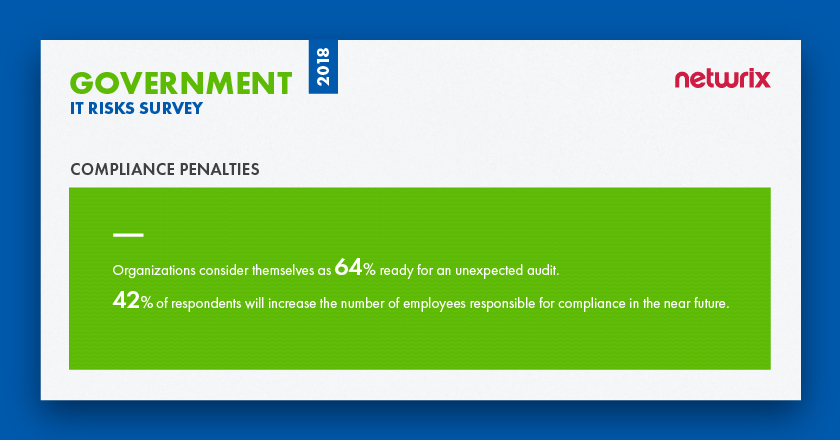
Although 64 % of government organizations consider themselves ready for an unexpected compliance check, 42% of respondents plan to increase the number of employees responsible for compliance in the near future. Unfortunately, as is often the case in the public sector, lack of budget leaves 37% of government organizations unable to hire additional personal to ensure regulatory compliance.
Case study: Alaskan state agency agrees to pay a fine to settle HIPAA violations
In 2012, the Alaska Department of Health and Social Services (DHSS) and the state’s Medicaid agency agreed to pay the Department of Health and Human Services (HHS) $1.7 million to settle HIPAA violations. While investigating a breach in which a portable storage device with ePHI of Medicaid beneficiaries was stolen from the vehicle of a DHSS employee, HHS found that DHSS did not have adequate policies and procedures in place. According to the report, DHSS had not completed risk analysis, implemented sufficient risk management measures, conducted security training for its workforce members, or addressed device and media encryption. In addition to agreeing to a fine of $1.7 million, HHS and Alaska crafted an action plan to correct those mistakes.
Summary
The Netwrix survey shows that government organizations do not always make the right decisions about security. Expectations do not always match reality — agencies focus on headline-making cyber threats like ransomware and spyware, but simple human mistakes and power outages do more harm in real life. The same is true for threat actors: In almost every threat category, organizations see the schemes of hackers and hacktivists, and fail to see that it’s actually their own employees who cause the most trouble and need to be under continuous control.
Other interesting results include the fact that it’s data loss, not data breaches, that is seen as the top IT risk. This IT risk is associated not only with service disruption but also with lawsuits from customers and employees, and harm to individuals if this data ends up in the wrong hands. These consequences, as well as the desire to deal with other IT risks more effectively, may be why most government organizations plan to increase their security investments by 112% in the next 5 years, and consider the identification of potential issues as the key way to improve cybersecurity.
View the full infographics for the 2018 IT Risks Survey and the results for the government sector here: